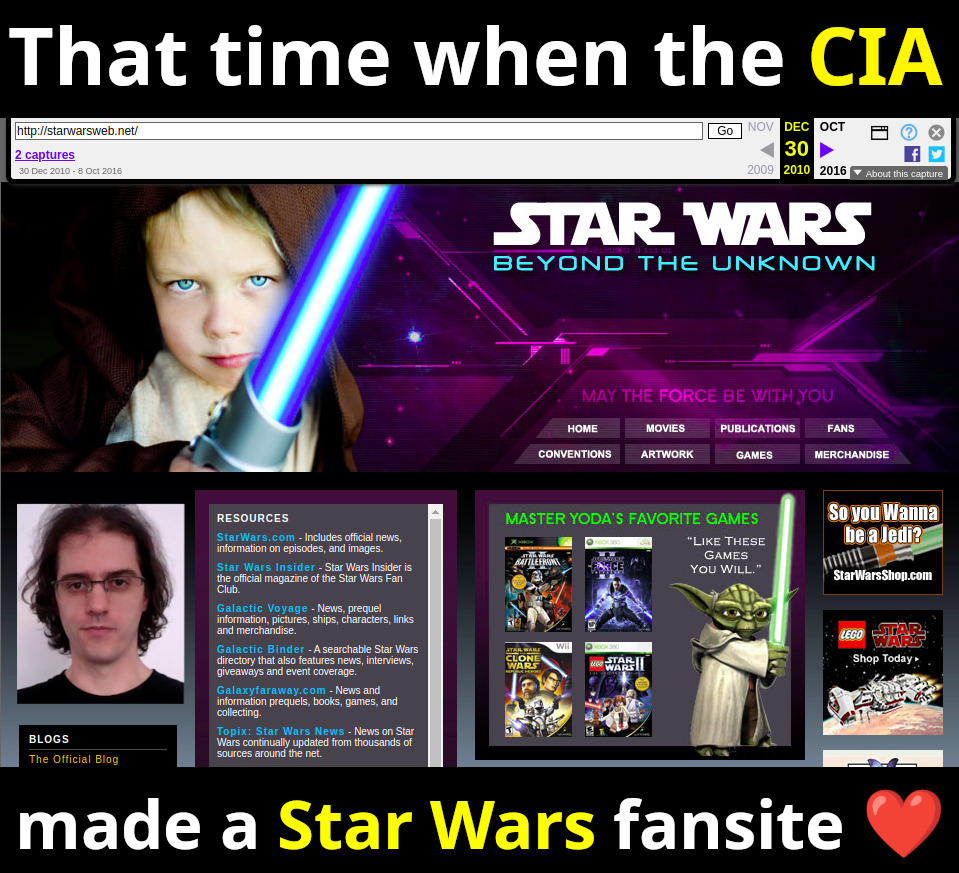
CIA 2010 covert communication websites Updated 2026-02-12
This article is about covert agent communication channel websites used by the CIA in many countries from the mid 2000s until the early 2010s, when they were uncovered by counter intelligence of some of the targeted countries, notably Iran and China, circa 2010-2013.
This article uses publicly available information to publicly disclose for the first time a few hundred of what we feel are extremely likely candidate sites of the network. The starting point for this research was the September 2022 Reuters article "America’s Throwaway Spies" which for the first time gave nine example websites, and their analyst from Citizenlabs claims to have found 885 websites in total, but did not publicly disclose them. Starting from only the nine disclosed websites, we were then able to find a few hundred websites that share so many similarities with them, i.e. a common fingerprint, that we believe makes them beyond reasonable doubt part of the same network.
If you enjoy this article, consider dropping some Monero at: 4A1KK4uyLQX7EBgN7uFgUeGt6PPksi91e87xobNq7bT2j4V6LqZHKnkGJTUuCC7TjDNnKpxDd8b9DeNBpSxim8wpSczQvzf so I can waste it on my foolish attempts to improve higher education. Other sponsorship methods: Section "Sponsor Ciro Santilli's work on OurBigBook.com".
The discovery of these websites by Iranian and Chinese counterintelligence led to the imprisonment and execution of several assets in those countries, and subsequent shutdown of the channel by the CIA when they noticed that things had gone wrong. This is likely a Wikipedia page that talks about the disastrous outcome of the websites being found out: 2010–2012 killing of CIA sources in China, although it contained no mention of websites before Ciro Santilli edited it in.
Of particular interest is that based on their language and content, certain of the websites seem to have targeted other democracies such as Germany, France, Spain and Brazil.
If anyone can find others websites, or has better techniques feel free to contact Ciro Santilli at: Section "How to contact Ciro Santilli". Contributions will be clearly attributed if desired. Some of the techniques used so far have been very heuristic, and that added to the limited amount of data makes it almost certain that some websites have been missed. Broadly speaking, there are two types of contributions that would be possible:
- finding new IP ranges: harder and more exiting, and potentially requires more intelligence
- better IP to domain name databases to fill in known gaps in existing IP ranges
The fact that citizenlabs reported exactly 885 websites being found makes it feel like they might have found find a better fingerprint which we have not managed to find yet. We have not yet had to pay for our data. If someone wants to donate to the research, some ideas include:
- dump $400 on WhoisXMLAPI to dump whois history of all known hits and search for other matches. Small discoveries were made like this in the past and we'd expect a few more to be left. We don't expect huge breakthroughs from this, but at only $400 it is not so bad
- dump a lot more ($15k+? needs confirmation as opaque pricing) on DomainTools. We are not certain that they have any superior data since there is no free trial of any kind, but it would be interesting to test the quality of the data they acquired from Farsight DNSDB if you are really loaded
Disclaimers:
- the network fell in 2013, followed by fully public disclosures in 2018 and 2022, so we believe that the benefit of giving the public this broader historic understanding outweighs the risks that agents could be found so many years later by sloppy secret services
- Ciro Santilli's political bias is strongly pro-democracy and anti-dictatorship, but with a good pinch of skepticism about the morality US foreign policy in the last century
CIA 2010 covert communication websites Find missing hits in IP ranges Updated 2025-07-16
It is because there was nothing there, or just because we don't have a good enough reverse IP database?
It is possible that DomainTools could help with a more complete database, but its access is extremely expensive and out of reach at the moment.
Putting 140 USD into WhoisXMLAPI to get all whois histories of interest for possible reverse searches would also be of interest.
CIA 2010 covert communication websites IP and DNS metadata Updated 2025-07-19
Sources of whois history include:
- whois-history.whoisxmlapi.com/ from whoisXMLAPI. Notably they also have historical reverse WHOIS... tools.whoisxmlapi.com/reverse-whois-search but it needs credits. TODO we need to squeeze this a but further at some point.
When that data comes in JSON format as from whoisXMLAPI, we are going to just dump it in github.com/cirosantilli/media/blob/master/cia-2010-covert-communication-websites/whois.json
The vast majority of domains seem to be registered either via domainsbyproxy.com which likely intgrates with Godaddy and is widely used, and seems to give zero infromation at all about the registrar.
A much smaller number however uses other methods, some of which sometimes leak a little bit of data:Big question: webmasters.stackexchange.com/questions/13237/how-do-you-view-domain-whois-history DomainTools also has it.
- Network Solutions, LLC. These sometimes give a tiny bit of information: one name. Other times they are hidden behind Perfect Privacy, LLC. Examples>Pulley, Tammy
- alljohnny.net: L. Glaze. tools.whoisxmlapi.com/reverse-whois-search "Glaze, L." has
- webstorageforme.com. web.archive.org/web/20130917230604/http://webstorageforme.com/ broken, cqcounter.com/whois/www/webstorageforme.com.html blank
- welcometonyc.net. Hit!
- international-smallbusiness.com. Same IP as alljohnny.net and quite possibly hit..
- alljohnny.com. Hit!
- locateontheweb.com. cqcounter.com/whois/www/locateontheweb.com.html broken/test page
- rolling-in-rapids.com. web.archive.org/web/20111101080224/rolling-in-rapids.com no archives but cqcounter.com/whois/www/rolling-in-rapids.com.html hit style! viewdns.info/iphistory/?domain=rolling-in-rapids.com puts it at:
- 208.91.197.132 British Virgin Islands CONFLUENCE-NETWORK-INC 2014-01-31
- 65.218.91.9 United States UUNET 2013-12-20 so matchwith welcometonyc.com but not listed at viewdns.info/reverseip/?t=1&host=65.218.91.9 because of the viewdns.info reverse IP bug!
- differentviewtoday.com: tools.whoisxmlapi.com/whois-history-search kind of empty no name
but presumably these are the names of employees of the company? We are yet to see two identical names however, which also suggests fake names. Network Solutions appears to offer both hosting and domain registration, and the CIA seems to have used this service combo a lot.- golf-on-holiday.com: Pulley, Tammy. No tools.whoisxmlapi.com/whois-history-search reverse hits.
- intoworldnews.com: Benjamin McGrew. Only that hit for reverse name at tools.whoisxmlapi.com/reverse-whois-search
- magneticfieldnews.com: Sarah Lowell tools.whoisxmlapi.com/reverse-whois-search has 9 domains
- sarahlowell.com: web.archive.org/web/20110208130657/http://sarahlowell.com/ Yoga instructor.
- puppychallengesacademy.com
- sarahlowelldogtraining.com
- puppychallenges.com. web.archive.org/web/20130517151924/http://puppychallenges.com/ wordpress.
- puppychallenges.net
- realwomensduathlon.com. No archives of era: web.archive.org/web/20180808101430/http://realwomensduathlon.com/
- magneticfieldnews.com. Hit.
- highflyingagility.com. Legit? Service offer.
- ropies.com. web.archive.org/web/20111101080224/http://ropies.com/
- medicatechinfo.com: Jason Noll. Has the following hits at tools.whoisxmlapi.com/reverse-whois-search
- dreamschemedesigns.com. Legit
- dreamschemedesigns.net
- aviationturbinesinternational.com. No relevant archives.
- garysluhan.com. Seems legit.
- cjlogic.com: registrar Godaddy (not Network Services!) and contact:This image is his Gmail's current profile image as of 2025: openclipart.org/detail/19437/high-wing-airplane
Noll, Jason noll.jason@gmail.com 104 Southridge Ct. Marthasville, Missouri 63357 United States (660) 441-0780 Fax -- - medicatechinfo.com. Hit.
- health-men-today.com. Hit. Holy fuck it has two hits out of 7!!!
- mydailynewsreport.com: Rebecca Melancon on tools.whoisxmlapi.com/reverse-whois-search:
- rebecca-melancon.com. web.archive.org/web/20180808172531/http://rebecca-melancon.com/ pilates teacher
- swlabuyahome.net
- swlalistmyhome.net
- rebeccaworking4yousite.com
- mylakecharlescityguide.com
- swlalistmyhome.com
- rebeccaworking4you.com
- swlabuyahome.com
- calcasieuhouses.com web.archive.org/web/20111013212502/http://calcasieuhouses.com/. Wordpress. Copyright Rebecca Melancon, Equal Housing Opportunity.
Message from Rebecca
Welcome to Calcasieu Houses! Here you will find not only information about Real Estate in Calcasieu Parish & the Lake Charles area, but also information about the area itself. I am constantly adding content so please check back often. I can help you with relocation, buying, selling, as well as looking for a great restaurant or a new activity to do! There will be information on Lake Charles, Sulphur, Westlake, & Moss Bluff. If you have something you would like to see added to the website, please feel free to contact me!
- mydailynewsreport.com. Hit.
- plugged-into-news.net: Godfrey Hubbard. Searching tools.whoisxmlapi.com/reverse-whois-search for two terms "Godfrey" "Hubbard" gives a small list of 20 domains including plugged-into-news.net. They all appear to have both words in them. Searching just "Hubbard, Godfrey" has only 3 hits:so it seems to match the strings exactly!
- hubbardgodfrey.online
- plugged-into-news.net
- hubbardgodfrey.com
- alljohnny.net: L. Glaze. tools.whoisxmlapi.com/reverse-whois-search "Glaze, L." has
- godaddy without domainsbyproxy.com: a few of the websites are registered in Godaddy without domainsbyproxy. These might be the ones that gives out the most information:
- baocontact.com
How on Earth did did Citizen Labs find what seems to be a DNS fingerprint??? Are there simply some very rare badly registered domains? What did they see!
Project Euler Created 2025-03-20 Updated 2026-01-30
They don't have an actual online judge system, all problems simply have a single small string solution, almost always integer or fixed precision floating point, and they just check that you've found the value.
The only metric that matters is who solved the problem first after publication. This is visible e.g. at: projecteuler.net/fastest=454 but only for logged in users... Lol it is ridiculous. The "language" in which problems were solved is just whatever the user put in their profile, they can't actually confirm that.
Problems are under CC BY-NC-SA: projecteuler.net/copyright
Once you solve a problem, you can then access its "private" forum thread: projecteuler.net/thread=950 and people will post a bunch of code solutions in there.
How problems are chosen:
projecteuler.net says it started as a subsection in mathschallenge.net, and in 2006 moved to its own domain. WhoisXMLAPI WHOIS history says it was registered by domainmonster.com but details are anonymous. TODO: sample problem on mathschallenge.net on Wayback Machine? Likely wouldn't reveal much anyways though as there is no attribution to problem authors on that site.
www.hackerrank.com/contests/projecteuler/challenges holds challenges with an actual judge and sometimes multiple test cases so just printing the final solution number is not enough.
Updates 60 new CIA website screenshots discovered on CQ Counter whoisXMLAPI whois history squeezed further and better understood Created 2025-04-15 Updated 2025-07-16
I also squeezed whoisXMLAPI harder but nothing much came out.
The vast majority of domains use domainsbyproxy.com privacy which does not seem to leak any information on their whois except dates which appear well spread out.
I did notice however that some of the sites are registered with Network Solutions, LLC and a few others in Godaddy without domainsbyproxy.com. These have names of people on them, and I did as many whoisXMLAPI searches for those names as I had the patience for.
A few had another known hit on the results, and a new hit domain came out of this: rolling-in-rapids.com which as it turns out has no Wayback machine archive, but does have a CQ Counter archive which allowed me to confirm the hit page style. That one was found by reverse searching for the registrant of
alljohnny.com, "Glaze, L." on tools.whoisxmlapi.com/reverse-whois-search and its IP matches 65.218.91.9 from welcometonyc.net.If anyone would like to donate 140 USD to dump into whoisXMLAPI I could dump all the known hit histories and have a look at them to see if anything else comes out on reverse search.
whoisfreaks 2025-08-08