Also wired phones don't require modulation, which likely made their development much easier than wireless voice transmission. You just send the signal as a voltage differential directly obtained from the air pressure: how the telephone works.
There are two types of people:
- those who are autodidacts
- those who didn't really learn
Some possible definitions:
Thus OurBigBook.com.
There's about 60 of them.
Seems to simulate the world in an extremely elaborate way.
Ciro can't help but to think that with a little content work, this game engine could also produce a Factorio-like (conveyor belts mentioned in passing at: discourse.cataclysmdda.org/t/vehicle-unloading/10783), or a The Sims-like, or an Stardew-valley-like. E.g. even stuff like house building is already included: www.youtube.com/watch?v=QnCYGSlZ1gE
They're also adding more and more allyied NPC management in "faction camps" it seems: www.reddit.com/r/cataclysmdda/comments/edg5y0/a_beginners_guide_to_faction_bases/ thus approaching the game further to Dwarf Fortress or RimWorld.
Ciro Santilli played this for 1 day and a half non-stop with save scumming in 2022, then he deleted his saves and uninstalled the game, and started Googling to see how end games can look like, as usual.
The problem is that it is a bit hard to find edited gameplay with highlights only, the type of people who play those games are just regular nerds right. But there is a lot of gameplay videos, just not edited ones.
Then two days later Ciro re-downloaded it and played more, just no so nonstop, the urge was too strong. Two days later, he deleted the save again after clearing out a middle sized town, and reaching a large town.
Then Ciro learned about debug menu, which is the best way to experience all buildings/weapons/abilities easily without grinding more than necessary. TODO any simple easy way to become invincible there? discourse.cataclysmdda.org/t/prompt-for-certain-debug-commands/19209/5Lol. Found a "Debug invincibility" and "Debug invisibility" under mutations.
We do not accept feature requests for the debug menu.
But a few days later he played a bit more for a day non-stop after having learnt some more techniques from YouTube, and then deleted again.
Ciro noticed that the part of this game that he likes the most is the early game. Raiding low populated areas like farms is joy. Once you get a car and stabilize, things become a bit less fun, and it is then just a matter of getting more and more powerful with a lot of routine work, which takes time. Sleeping in tents is quite tempting as well, there's a campfire overmap tile that is great. You can actually take down tents Ciro later learnt... that's awesome.
A major joy of this type of game is the ability to loot shops and homes without any moral implications since the former owners are all dead/zombified.
Another major joy is the incredible value you attach to items you discover, because they are truly life changing.
For example, Ciro was first obsessed with his duffel bag, which could carry huge volumes, and made fixing it a top priority once it got ripped!
Then he was obsessed about the 4x4 car he found, which looks like this:where:What a great design! Enough room for a lot of loot, and also the reinforced frame to kill zombies without destroying the car, all while not being overly heavy which spends a lot of fuel, not being too wide which makes maneuvering in cities with broken cars on the road hard! Also the trunks were large enough for large water tanks, which solves your clean water supply forever.
fffffF
fttsfF
fttsfF
fffffFf: frameF: reinforced framet: trunks: seat
Humvees are also good, but they are wider, have a lot of useless seats, and consume diesel, a lot of diesel, runs out very quickly. But they are even tougher than the 4x4, and have a turret that can fire at zombies.
It should be noted however that larger towns are generally just too much to use a car to clear, you will just waste too much fuel/car damage/real world time. The only way is to go at night it seems.
And then guns. The power of a guns is something to behold. Encounters that would easily be your death become one shot escapes. But of course, ammo is very limited, so you want to use each precious shot wisely! FEMA camps are a good place to get some easy powerful rifles and reasonable amount of ammo. Just drive in front of the entrance, and make the armed guards follow you out, then run them over. Try not to attract the zombie inside though, they are useless civilians without weapons, and just take up your time.
This game is also very good to learn some English if you are not a native, as you have to learn what all those bit and bobs you never needed to say before are.
The default tileset when running
cataclysm-tiles is a huge improvement over the text version, but still, could be a bit higher res. Overmap tilesets were only added in 2021 it seems: www.reddit.com/r/cataclysmdda/comments/pxtqsn/new_overmap_tileset_available/. Edit: 0.F appears to come with the proper Ultima tileset by defualt via cataclysm-dda-data Ubuntu 22.04 package. Fantastic!There are other built-in tiles under settings, but all of them are way too resolution for a casual gamer.
github.com/I-am-Erk/CDDA-Tilesets has a good tileset pack. To install on Ubuntu 21.10, drop the release under:and then select
~/.local/share/cataclysm-dda/gfx/UltCa from Settings > Tiles in the main menu. It does make things much more immediately understandable. Edit: after some initial plays, Ciro had a second look at the default -tiles graphics, and they are not so bad. But still, the higher resolution is better. Edit: looks like they are going to merge it in-tree, which is great! github.com/CleverRaven/Cataclysm-DDA/commits/master/gfx/UltimateCataclysmNo default sounds, but has a soundpacks mechanism. Sad for now default, but cool for the configurability:
Installation is similar to tilesets, but you put it under
sounds/ instead of gfx/. Restart required to select the soundpack option, and another restart required for the selected option to be used, clunky.This is the type of thing that prevents wider adoption of this game, it is just too hard to figure out things.
The other major requirement for casual players would be mouse clicking stuff with dropdown menus that show what you can do there (e.g.
E and Shift + G), and better menus, everything should be also doable with a mouse in addition to the keyboard shortcuts.Besides the zombies, it also has some high tech stuff like bionics and aliens mixed in. And mods add other stuff, e.g. cddawiki.chezzo.com/cdda_wiki/index.php?title=Magiclysm which is quite cool. The design document/lore spoilers explain that this is the actual cause of te cataclysm: cataclysmdda.org/lore-background.html
The cool thing about this type of game is that enemies are really powerful, which is so much more realistic. Even a single zombie has to be given lots of respect, especially since healing is a slow process like real life, and killing one feels like an achievement.
Some other cool points:
- www.reddit.com/r/cataclysmdda/comments/3m92cc/are_worlds_truly_infinite/ the map is truly infinite. Everything is persistent. They must freeze things in some state of course when the player is not around, and hydrate it (using React.js-like terminology!) when you come back, but they all look very plausibly continuous to how things where. They call the fully simulated world the "reality bubble": cddawiki.chezzo.com/cdda_wiki/index.php?title=Reality_bubble That pages says though that not everything hydrates. Shame there are no oceans yet: www.reddit.com/r/cataclysmdda/comments/huvnon/when_are_we_getting_oceans/But there are lakes, and lake islands: cddawiki.chezzo.com/cdda_wiki/index.php?title=Lake but they are quite rare on the mapgen, outside of fixed scenario starts.
Tips for beginners:
- a Reddit list: www.reddit.com/r/cataclysmdda/comments/hsxpco/things_you_wish_you_knew_when_you_started_playing/
- go to town at night, zombies are even blinder than you, it is possible to sneak by massive hoards, fighting one enemy at a time, even when they are well packed together. The only possible reason to go out during the day is to smash zombies with a car without crashing.
- favoriting items makes you not drop them by default with
,. This is fundamental so you can drop loot while keeping survival stuff on you. - indestructible and faster than you early game enemies, encounter means certain death: Survivor zombie, Giant cockroach, Giant wasp. Walking on trails is also potentially deadly, which is very annoying... sometimes you only see dealy enemies like wolves when you are on top of them on trails. Not sure what to do about that.
- pick up all items from any surrounding tile:
/, then on leftIfor inventory, on rightAfor area. You can also examine items witheif not everything fits, and sort by category withs. That's the most important menu in the game! - duffel bags are the best thing ever made, carry huge volumes, and you can craft them too!
- smash (
S) zombie corpses after you kill them, or else they will re-raise after a few hours. They will be wounded and easy to kill however. - just like in real life, cars are the ultimate killing machine. For some reason though, it does not smash zombie corpses. They can also carry infinite crap, after clearing up a town, you can just pick up EVERYTHING without thinking too much, just hit
,. To bulk move things into/off a car, just hold Enter until the inventory is full. So sort huge piles by category: Shift + V then S:.Just like in real life, bicycles are pretty good if you can't find a working car, as they don't consume fuel, just stamina. You can even go around hordes if you are crazy enough, and try to look for working cars in towns, but going on the countryside would be wiser. Just make sure you always have enough stamina to cycle out to safety if your electric motor isn't working, which is often the case!Electric cars can also be recharged from the sun, which means they will never run out. They are generally not very strong, so not suitable for ramming, and the battery runs out relatively soon. But great to stop out of town. - head encumbrance does not seem to do anything besides limit how many hats you can wear, so do ware that motorcycle helmet: www.reddit.com/r/cataclysmdda/comments/a5nq6c/head_encumbrance/
- headlamps are a must
- on the overmap
m, you can fast travel withShift + Wtwice. Not perfect path finding, but saves a lot of useless clicking! - on the EVAC shelter computer, contact us is not useless at all! It shows the nearest refugee center, and can show a lot of map because it shows the full road path there
- climb buildings to see further out. You can start by climbing the EVAC shelter via gutter with
>! But to go down pipes you have to examine it, not<, it's weird. Edit: actually, you can "climb down" any ledge, so that's why. But you can still get hurt, so don't do it unless it is really necessary. You will want to carry the telescope, or a binoculars with you at all times most likely, as it is just a huge asset. You just can't climb back up without the water pipe. Radio tower and silos are other good buildings to climb, and radio towers often contain telescopes which allow you to see very very far, climbing those is a top priority when scouting a new region. Don't jump down, even of 1 floor, as it hurts you. A bit exaggerated, but so be it. - you can grind fabrication easily to level 1 even without a book: www.reddit.com/r/cataclysmdda/comments/6r2477/best_way_to_grind_fabrication/ This is fundamental to make the all important brazier. And you'll learn that dumping things in the brazier unnecessarily burns them out, the uninsuitive "Construct" > "Firewood Source" is a must.
- place brazier immediately outside of the EVAC shelter window, this way you avoid smoke problems, but can still cook from the inside.
- shopping carts are the very best mechanism to carry a lot of loot in town besides a car. And there's a foldable version that can fit into cars, but you have to craft it... www.youtube.com/watch?v=kccBl7cksPY. Most important item ever.
- there's a built-in debug menu that allows you to cheat whatever you want: spawn items, change your stats (e.g. 10000 strenght and smash through walls? no problem), learn skills, reveal map, and teleport. You have to bind a key to it before using it from
?,,is a good bind candidate. Now that's real fun, being God. - auto-smash mode is a must
- you likely should look into spears: www.reddit.com/r/cataclysmdda/comments/7m99jb/why_melee_with_anything_besides_spears/. Reach attacks from spears are OP, as you can hit a zombie, run, wait for it to come in range, hit from afar, run, and so on. Then after killing a zombie, you wait until your stamina recovered with
|. This allows to safely kill anything as fast as you without taking hits. Wooden spear is a good first one, and it is not flimsy and lasts a while, like 30-50 zombies maybe. A pitch fork is another good option if you can find one.
How a typical early day looks like for a newbie: go to down, fight 5 zombies, get some stuff from houses, and run back home because your limbs are too weak and could break. Get home 10AM, and read the hole day and night. Repeat.
A fun play style is: get a car, clear out a small town with a library, bring food and books back to the base, fill the 4 60L tanks with water and bring them on the car as well, and then just read for several days until the food runs out. Repeat. It is not super serious if you don't have a car though, as even "shallow water" pools found in every forest can fill one of them. Exploitative mechanic BTW.
Top feature requests for Ciro Santilli:
- www.reddit.com/r/cataclysmdda/comments/2mni5z/can_i_store_items_in_a_backpack_and_drop_the/. As of 0.E-3-1, drop happens automatically on Take off, but then you have to pick up items that go overweight/volume one by one.
- find items in my inventory by quality, or at least all item qualities in a single sortable table, otherwise it is too hard to know which item can do what
- fill all empty containers with something, e.g. water from a large pool into 25 plastic bottles
- view wound details without having to select bandage or antiseptic.
@"EFFECTS" has a summary, but it is too tiny, that stats window should be fullscreen for sure - realism requests. Ciro is a big fan of realism in CDDA, the more the better, and if you don't like something, just use the debug menu!
- shitting/peeing system
- when you wash clothes (currently important because zombie worn clothes that you pickup are generally filthy and reduce morale), make the clothes wet and require drying. There are even already some rotation clothes handers in houses, but just putting on a bench would be enough. And of course, higher temperatures mean faster drying, next to a fire would be ideal. Wearing wet clothes would of course make you cold and demoralized.
- exercise/fitness
TODO how to create a custom non random map/scenario? Possible from JSON: discourse.cataclysmdda.org/t/guide-to-adding-new-content-to-cdda-for-first-time-modders/17781/13/ ?
Their dominating Q&A communication channels are terrible, as of 2021 everything you google leads to: www.reddit.com/r/cataclysmdda/ which suffers from online forums that lock threads after some time are evil (edit: this changed since). They've since made a discourse thankfully however: discourse.cataclysmdda.org/
Source code overview:
- it is funny how the
lang/directory with translations is by far the largest of the repo ta 100MB, way larger thangfx, it's comical
One of the things it simulates is some level of builing stuff:
- you can build a wooden house: www.youtube.com/watch?v=QnCYGSlZ1gE including floor, roof, windows. There are also concrete walls. Of course, building is useless, what you really want is a super mega truck that doubles as a home.
- TODO can you generate power e.g. in solar cells or not, and wire it into home appliances? www.reddit.com/r/cataclysmdda/comments/4zm7tf/solar_panels_useless/ from 2016 says no.The solution would be simple... just mark the edge incoming wire from the reality bubble as a magic source that has a given voltage/max amperage/total power or total wattage available. Would be good enough. Sure, some estimates might be hard, e.g. how much sun is there in a far away location of the map, etc. but just having some average of those values would be good enough. E.g. average temperature of an off bubble tile would also be useful to calculate food rotting time.
- cddawiki.chezzo.com/cdda_wiki/index.php?title=Power says yes "farmhouse kitchen running off of outside solar, cabled in"
- www.reddit.com/r/cataclysmdda/comments/9j9e16/wired_homes_and_electrical_systemgrid/ from 2018 says no due to fundamental reality bubble limitations, the only way is with power coming from stuff mounted on vehicles...
A related obvious application would be refrigerators. www.youtube.com/watch?v=G6B0KBJHvZs from 2021 mentions again that you can't have power without vehicles. TODO do the refrigerators in a powered 01 lab protect food?The fork github.com/cataclysmbnteam/Cataclysm-BN is actually trying to add an electric grid...
Cataclysm: Dark Days Ahead Review by SsethTzeentach (2018)
Source. This game really is right up Seth's alley, glad he tried it out. Perhaps his review was partly what motivated Ciro Santilli to give it a try. But the other part, perhaps even more important, was the joy of trying out crappy open source video games. Ciro especially likes Seth's observation that you could just go all in Mad Max mode. Since vehicles are so powerful, you can just clean up towns with them and basic weapons, then either get a new vehicle when the old one goes bust, or at least very easily find gas. Another good observation is that crafting in this game is amazing.This game is quite detailed: www.youtube.com/watch?v=w4Jmqp8a_bU
Superconductivity is one of the key advances of 21st century technology:
- produce powerful magnetic fields with superconducting magnets
- the Josephson effect, applications listed at: Section "Applications of Josephson Junctions"
- twitter.com/bicyclelobby
- Shifter YouTube channel: www.youtube.com/channel/UC9-ZlLTioqMZowRLZHscozw. Has many videos about making cycling as means of transport. He's from Calgary, Canada.
- banprivatecarsinlondon.com/ Ban Private Cars in London
- stopkillingcyclists.org
- Reclaim the Streets
- www.youtube.com/@NotJustBikes
- kidsonbike.org: they make some large bike rides to promote themselves, good method
- 2024 www.designboom.com/design/latvia-cyclists-car-skeletons-vehicle-size-10-10-2014/ cyclists with car skeletons
Theory that gases are made up of a bunch of small billiard balls that don't interact with each other.
This theory attempts to deduce/explain properties of matter such as the equation of state in terms of classical mechanics.
Why do symmetries such as SU(3), SU(2) and U(1) matter in particle physics? by  Ciro Santilli 40 Updated 2025-07-16
Ciro Santilli 40 Updated 2025-07-16
Physicists love to talk about that stuff, but no one ever has the guts to explain it into enough detail to show its beauty!!!
Perhaps the wisest thing is to just focus entirely on the part to start with, which is the quantum electrodynamics one, which is the simplest and most useful and historically first one to come around.
Perhaps the best explanation is that if you assume those internal symmetries, then you can systematically make "obvious" educated guesses at the interacting part of the Standard Model Lagrangian, which is the fundamental part of the Standard Model. See e.g.:
- derivation of the quantum electrodynamics Lagrangian
- Physics from Symmetry by Jakob Schwichtenberg (2015) chapter 7 "Interaction Theory" derives all three of quantum electrodynamics, weak interaction and quantum chromodynamics Lagrangian from each of the symmetries!
Notably, axelmaas.blogspot.com/2010/08/global-and-local-symmetries.html gives a good overview:so it seems that that's why they are so key: local symmetries map to the forces themselves!!!
A local symmetry transformation is much more complicated to visualize. Take a rectangular grid of the billiard balls from the last post, say ten times ten. Each ball is spherical symmetric, and thus invariant under a rotation. The system now has a global and a local symmetry. A global symmetry transformation would rotate each ball by the same amount in the same direction, leaving the system unchanged. A local symmetry transformation would rotate each ball about a different amount and around a different axis, still leaving the system to the eye unchanged. The system has also an additional global symmetry. Moving the whole grid to the left or to the right leaves the grid unchanged. However, no such local symmetry exists: Moving only one ball will destroy the grid's structure.Such global and local symmetries play an important role in physics. The global symmetries are found to be associated with properties of particles, e. g., whether they are matter or antimatter, whether they carry electric charge, and so on. Local symmetries are found to be associated with forces. In fact, all the fundamental forces of nature are associated with very special local symmetries. For example, the weak force is actually associated in a very intricate way with local rotations of a four-dimensional sphere. The reason is that, invisible to the eye, everything charged under the weak force can be characterized by a arrow pointing from the center to the surface of such a four-dimensional sphere. This arrow can be rotated in a certain way and at every individual point, without changing anything which can be measured. It is thus a local symmetry. This will become more clearer over time, as at the moment of first encounter this appears to be very strange indeed.
axelmaas.blogspot.com/2010/09/symmetries-of-standard-model.html then goes over all symmetries of the Standard Model uber quickly, including the global ones.
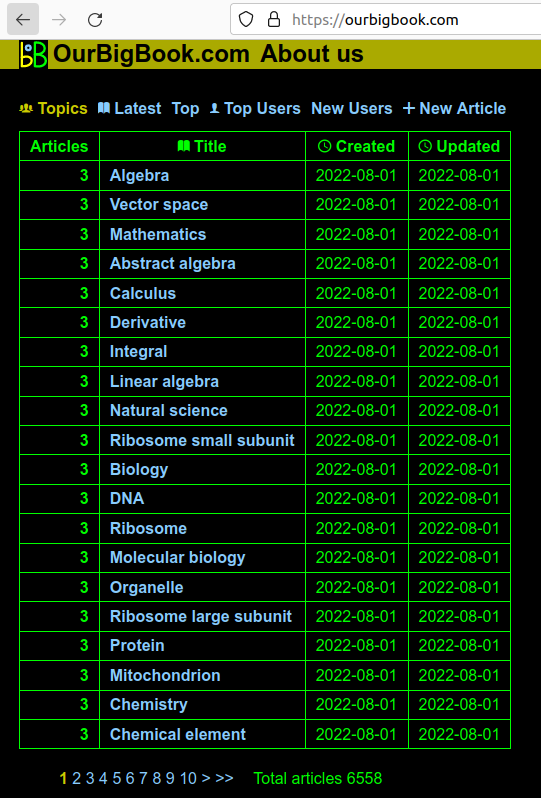
The new default homepage for a logged out user how shows a list of the topics with the most articles.
This is a reasonable choice for default homepage, and it immediately exposes users to this central feature of the website: the topic system.
Doing this required in particular calculating the best title for a topic, since it is possible to have different titles with the same ID, the most common way being with capitalization changes, e.g.:would both have topic ID
JavaScript
Javascriptjavascript.The algorithm chosen is to pick the top 10 most upvoted topics, and select the most common title from amongst them. This should make topic title vandalism quite hard. This was made in a single SQL query, and became the most complext SQL query Ciro Santilli has ever written so far: twitter.com/cirosantilli2/status/1549721815832043522
Screenshot showing the list of topics
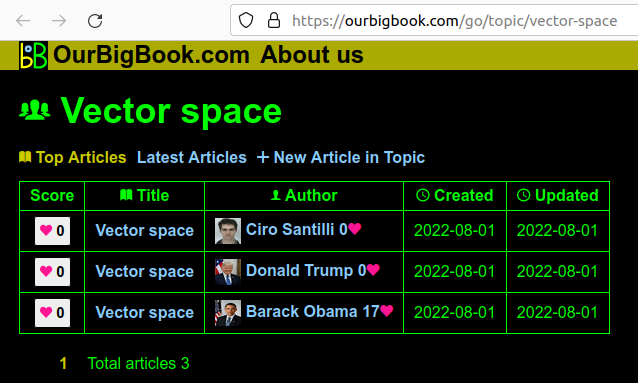
. The page is: ourbigbook.com for the logged out user, ourbigbook.com/go/topics for the logged in user.Screenshot showing a topic page
. The page is: ourbigbook.com/go/topic/vector-space. Before this sprint, we didn't have the "Vector Space" at the top, as it wasn't necessarily trivial to determine what the preferred title would be.You can now write:in lieu of the old:
<Blue cats> are nice.
= Blue cat
= Big blue cat
{parent=Blue cat}\x[blue-cat]{c}{p} are nice.
= Blue cat
= Big blue cat
{parent=blue-cat}Before
. After
. Added font awesome icons. github.com/ourbigbook/ourbigbook/issues/151
Didn't manage to subset, but so be it for now: stackoverflow.com/questions/62395038/how-can-i-export-only-one-character-from-ttf-woff-file-to-avoid-load-unnecessa/71197892#71197892
Ciro's Edict #5 Make  Ciro Santilli 40 Updated 2025-07-16
Ciro Santilli 40 Updated 2025-07-16
\Include headers show on table of contents work for cirosantilli.com by One of the key advances of the previous update was to show include headers on the table of contents.
This was to allow splitting source files freely.
While that goal was in principle achieved in that commit, when I went ahead to split the huge index of cirosantilli.com into multiple files, I notice several bugs that took a week to fix.
After all of these were solved, I finally managed to split the README at: github.com/cirosantilli/cirosantilli.github.io/commit/84c8a6e7fdbe252041accfb7a06d9b7462287131 and keep the previous desired output. You can now see that the README contains just:
\Include[ciro-santilli]
\Include[science]
\Include[mathematics]
\Include[technology]
\Include[art]This split led to a small positive modification of the output as follows. Previously, a section such as "Quantum Electrodynamics" would have been present in the monolithic README.ciro as:If you visited cirosantilli.com/quantum-electrodynamics, you would see see a link to the "nosplit" version, which would link you back to cirosantilli.com#quantum-electrodynamics, but that is not great, since this is was a humongous page with all of the README.ciro, and took long to display.
= Quantum electrodynamicsAfter the split,
= Quantum electrodynamics is present under science.ciro, and the nosplit version is the more manageable cirosantilli.com/science#quantum-electrodynamics.The key changes that were missing for that to happen were:
Ciro's Edict #4 Further improvements to the website's base technology by  Ciro Santilli 40 Updated 2025-07-16
Ciro Santilli 40 Updated 2025-07-16
github.com/cirosantilli/node-express-sequelize-nextjs-realworld-example-app contains the same baseline tech as OurBigBook, and I have been use to quickly test/benchmark new concepts for the website base.
I'm almost proud about that project, as a reasonable template for a Next.js project. It is not perfect, notably see issues on the issue tracker, but it it quite reasonable.
The side effects of ambitious goals are often the most valuable thing achieved once again? I to actually make the project be more important thatn the side effects this time, but we'll see.
Since the last update, I've made some major improvements to the baseline tech of the website, which I'll move little by little into OurBigBook. Some of the improvements actually started in OurBigBook.com. The improvements were:
- got a satisfactorily comprehensive linting working at: this commit. Nothing is easy, not even that! Part of the wisdom extracted to: stackoverflow.com/questions/58233482/next-js-setting-up-eslint-for-nextjs/70519682#70519682.
- fully rationalized directory structure to avoid nasty errors that show up in Next.js when accidentally requiring backend stuff on the client. Commit. A detailed explanation of this was extracted to: stackoverflow.com/questions/64926174/module-not-found-cant-resolve-fs-in-next-js-application/70363153#70363153.
- create an extremely clean and rationalized way to do API tests from a simple
npm test. These now actually start a clean server, and make full HTTP requests to that server. Commit. Wisdom extracted to: stackoverflow.com/questions/63762896/whats-the-best-way-to-test-express-js-api/70479940#70479940. - greatly reduce the number of SQL queries, fully understood every problem
- more intelligently using JOINs where I have managed to get Sequelize to do what I fucking want. This also led to several sequelize Stack Overflow answers as usual: stackoverflow.com/search?tab=newest&q=user%3a895245%20%5bsequelize%5dEverything that I didn't manage to do because of crappy sequelize is documented at: github.com/cirosantilli/node-express-sequelize-nextjs-realworld-example-app/issues/5
- better understanding Next.js/React/useSWR do avoid doing double API queries
There are unlisted articles, also show them or only show them.