CIA 2010 covert communication websites Hits without nearby IP hits Updated 2025-07-16
Here we list of suspected domains for which the correct IP was apparently not found since there are no neighbouring hits.
These are suspicious, and suggest either that we didn't obtain the correct reverse IP, or a change in CIA methodology from an older time at which they were not yet using the obscene IP ranges.
For example, in the case of inews-today.com, 2013 DNS Census gave one IP 193.203.49.212, but then viewdns.info gave another one 66.175.106.146 which fit into an existing IP range, and which assumed to be the correct IP of interest.
A similar case happened when we found IP 212.209.74.126 for headlines2day.com with dnshistory.org: dnshistory.org/historical-dns-records/a/headlines2day.com.
It is also possible that some of them are simply false positives so they should be taken with a grain of salt. Further reverse engineering e.g. of comms or HTML analysis might be able to exclude some of them.
It is interesting to note that Reuters seems to have featured disproportionately many hits from that range, one wonders why that happened. It is possible that they chose these because they actually didn't have any nearby hits to give away less obvious information, though they did pick some from the ranges as wel.
In what follows we list the domains with possible reverse IPs and what was explored so far for each. We consider IPs not in a range to be uncertain, and that instead their domains might have been previously in a range which we
dailynewsandsports.com. Found with: 2013 DNS Census virtual host cleanup heuristic keyword searches
- 216.119.129.94. rdns source: viewdns.info "location": "United States", "owner": "A2 Hosting, Inc.", "lastseen": "2012-04-13". Tested viewdns.info range: 216.119.129.85 - 216.119.129.86, 216.119.129.89 - 216.119.129.99, ran out of queries for 87 and 88
- 216.119.129.90: eastdairies.com 2011-04-04. Promising name and date, but no archives alas.
- 216.119.129.97: miideaco.com 2016-02-01
- 216.119.129.114 Found with: 2013 DNS Census virtual host cleanup heuristic keyword searches, also present on viewdns.info but at a later date from previous "location": "United States", "owner": "A2 Hosting, Inc.", "lastseen": "2013-11-29". Tested viewdns.info range: 216.119.129.109 - 216.119.129.119
- 216.119.129.110: dommoejmechty.com.ua. Legit.
- 216.119.129.111: dailybeatz.com: Legit
- 216.119.129.113:
- audreygeneve.com
- reyzheng.com
- jacintorey.com
- 216.119.129.114: dailynewsandsports.com. hit.
- 216.119.129.115: afxchange.com legit/broken
- 216.119.129.116: danafunkfinancial.com: legit
- 208.73.33.194 on securitytrails.com
iranfootballsource.com:
- 34.98.99.30 Kansas City - United States Google LLC 2021-05-24
- 184.168.221.94 United States GoDaddy.com 2020-07-21
- 50.63.202.66 United States GoDaddy.com 2020-07-07
- 50.63.202.86 United States GoDaddy.com 2020-05-28
- 184.168.221.94 United States GoDaddy.com 2020-05-13
- 50.63.202.74 United States GoDaddy.com 2020-04-29
- 50.18.223.191 San Jose - United States Amazon.com 2015-03-23. Sources: 2013 DNS Census and viewdns.info
- no viewdns.info hits +- 10
- 85.13.200.108 United Kingdom Coreix Dedicated Customer Allocation 2013-06-30. Source: viewdns.info
- 85.13.200.108: 1000 hits, so unlikely to be the one
iraniangoalkicks.com:
- 68.178.232.100: treverse IP source: viewdns.info. see rastadirect.net.
- 208.71.138.130 2010-02-22 -> 2010-08-06, QWK.net Hosting, L.L.C.. source: dnshistory.org/historical-dns-records/a/iraniangoalkicks.com. Large shared hosting domain, no good nearby hits, several legit sites.
- securitytrails.com/domain/iraniangoalkicks.com/history/a says:
- 2011-03-31 68.178.232.100
- 2008-09-01 208.71.138.130
iraniangoals.com:
- 68.178.232.100: see rastadirect.net
- 69.65.33.21 - Flushing - United States - GigeNET - 2011-09-08. Also at: dnshistory.org/historical-dns-records/a/iraniangoals.com 2009-08-03 -> 2011-01-12 69.65.33.21 viewdns.info/reverseip/?t=1&host=69.65.33.21 80 virtual nothing pops to eye on quick read:
- 69.65.33.2: onemincustomerservice.com. web.archive.org/web/20091015044922/http://www.onemincustomerservice.com/. Doesn't feel like a hit. cqcounter.com/whois/www/onemincustomerservice.com.html error
- 69.65.33.5: 400+ domains
- 69.65.33.6: 4 domains but recent resolutions only
- similar status for everything else withing +-20. A couple of domains, no easy hits
- securitytrails.com/domain/iraniangoals.com/history/a same from 2008-09-17
football-enthusiast.com:
- 212.4.18.14: Tested viewdns.info range: 212.4.18.1 - 212.4.18.29. This is a curious case, rather close to 212.4.18.129 sightseeingnews.com, but not quite in the same range apparently. Viewdns.info also agrees on its history with only "212.4.18.14", "location" : "Milan - Italy", "owner" : "MCI Worldcom Italy Spa", "lastseen" : "2013-06-30" of interest.
cyhiraeth-intlnews.com:
news-latina.com: domainsbyproxy.com 2007-12-17
- dnshistory.org/historical-dns-records/a/news-latina.com 2010-03-11 -> 2010-08-16 64.92.111.3. this has several hits for the same IP on DNS Census 2013 which is unusual. Tested viewdns.info range: 64.92.111.1 - 64.92.111.13
- viewdns.info/iphistory/?domain=news-latina.com
- 68.178.232.100 United States AS-26496-GO-DADDY-COM-LLC 2011-08-11 virtual
- 64.92.111.3 United States MASSIVE-NETWORKS 2011-07-27 mdeium virtual viewdns.info/reverseip/?t=1&host=64.92.111.3
- web.archive.org/web/20110211133905/http://tipsypotpole.com/ off
- web.archive.org/web/20250000000000*/quantumhealing.com popular
- web.archive.org/web/20110202114353/http://outdoortradition.com/ redirecting. dawhois.com/www/outdoortradition.com.html not found.
- web.archive.org/web/20250000000000*/gtinvestigations.com popular
- web.archive.org/web/20250000000000*/dig-itmag.com big
europeannewsflash.com:
- viewdns.info/iphistory/?domain=europeannewsflash.com
- 68.178.232.100 United States AS-26496-GO-DADDY-COM-LLC 2011-10-09 virtual
- 216.131.66.209 San Francisco - United States STRTEC 2011-09-08. Tested viewdns.info range: 216.131.66.201 216.131.66.219
- dnshistory.org/historical-dns-records/a/europeannewsflash.com 2010-02-06 -> 2010-08-02 216.131.66.209. Tested.
outlooknewscast.com:
- dnshistory.org/historical-dns-records/a/outlooknewscast.com
- 2009-08-08 -> 2011-02-11 74.53.159.130. Tested viewdns.info range: 74.53.159.120 - 74.53.159.140
- 74.53.159.130: aeromedhistory.org 2014-11-29
- 74.53.159.130: mariposahorticultural.com 2022-11-28
- 74.53.159.130: thewritestuffresume.com 2011-04-04. Legit.
- 2009-08-08 -> 2011-02-11 74.53.159.130. Tested viewdns.info range: 74.53.159.120 - 74.53.159.140
- viewdns.info/iphistory/?domain=outlooknewscast.com
- 204.93.178.121 Chicago - United States SERVERCENTRAL 2011-09-08. Tested viewdns.info range: 204.93.178.111 - 204.93.178.131. Skimmed through, nothing of great interest.
- 74.53.159.130 United States SOFTLAYER 2011-04-04. Tested.
24hoursprimenews.com:
- dnshistory.org/historical-dns-records/a/24hoursprimenews.com 2009-12-14 -> 2011-10-04 216.9.68.24. Mid virtual: viewdns.info/reverseip/?t=1&host=216.9.68.24 had a quick look but no hits:
- viewdns.info/iphistory/?domain=24hoursprimenews.com 216.9.68.24 United States VONAGE-BUSINESS 2012-01-11. Tested.
- securitytrails.com/domain/24hoursprimenews.com/history/a same
farsi-newsandweather.com:
- dnshistory.org/historical-dns-records/a/farsi-newsandweather.com 2010-02-07 -> 2010-08-03 69.49.101.19. Tested viewdns.info range: 69.49.101.9 - 69.49.101.19
- viewdns.info/iphistory/?domain=farsi-newsandweather.com
- 68.178.232.100 United States AS-26496-GO-DADDY-COM-LLC 2012-01-11 virtual
- 69.49.101.19 Canada INFB-AS 2011-11-13. Tested.
global-view-news.com:
- dnshistory.org/historical-dns-records/a/global-view-news.com 2010-02-13 -> 2010-08-04 67.220.228.130. Tested viewdns.info range: 67.220.228.120 - 67.220.228.160:
- 67.220.228.150: investfromhome.co.uk 2011-09-05. No archives.
- viewdns.info/iphistory/?domain=global-view-news.com
- 68.178.232.100 United States AS-26496-GO-DADDY-COM-LLC 2012-01-11 virtual
- 69.90.161.195 Canada COGECO-PEER1 2011-09-08. Unknown. Tested viewdns.info range: 69.90.161.185 69.90.161.205. Some virtual misses. viewdns.info/reverseip/?t=1&host=69.90.161.195 medium virtual, canada.
health-men-today.com:
- dnshistory.org/historical-dns-records/a/health-men-today.com
- 2011-01-07 -> 2011-01-07 69.90.162.165. Tested viewdns.info range: 69.90.162.155 - 69.90.162.175. Virtuals.
- 2009-11-30 -> 2010-05-27 67.220.228.224. New range with global-view-news.com? Tested viewdns.info range: 67.220.228.214 67.220.228.234
- 2009-08-01 -> 2009-09-19 69.42.58.50. Tested viewdns.info range: 69.42.58.40 - 69.42.58.60. Virtuals, canada.
- viewdns.info/iphistory/?domain=health-men-today.com
- securitytrails.com/domain/health-men-today.com/history/a
- 69.42.58.50 Aptum Technologies 2008-09-01 (17 years) 2008-09-04 (17 years) 3 days
firstnewssource.com:
pars-technews.com:
- dnshistory.org/historical-dns-records/a/pars-technews.com 2009-08-08 -> 2011-02-13 74.220.219.104 Tested viewdns.info range: 74.220.219.94 74.220.219.114. viewdns.info/reverseip/?t=1&host=74.220.219.104 medium virtual haven't bothered much.
- viewdns.info/iphistory/?domain=pars-technews.com 74.220.219.104 United States UNIFIEDLAYER-AS-1 2012-11-12. Tested.
newdaynewsonline.com:
- dnshistory.org/historical-dns-records/a/newdaynewsonline.com 2010-03-10 -> 2010-08-15 76.163.54.16. Tested viewdns.info range: 76.163.54.6 76.163.54.26. viewdns.info/reverseip/?t=1&host=76.163.54.16 empty.
- 76.163.54.23: leewoodwork.com 2014-07-05
- viewdns.info/iphistory/?domain=newdaynewsonline.com
- 74.91.154.56 United States INTERNAP-BLOCK-4 2012-11-12 unknown range. Tested viewdns.info range: 74.91.154.46 74.91.154.66
- 74.91.154.61: benefitsla.com 2013-04-21. Legit.
- 76.163.54.16 United States WINDSTREAM 2011-09-08 unknown range. Tested.
- 74.91.154.56 United States INTERNAP-BLOCK-4 2012-11-12 unknown range. Tested viewdns.info range: 74.91.154.46 74.91.154.66
sportsnewsfinder.com:
- dnshistory.org/historical-dns-records/a/sportsnewsfinder.com 2009-08-11 -> 2011-02-24 66.113.196.128. Tested viewdns.info range: 66.113.196.118 66.113.196.138. viewdns.info/reverseip/?t=1&host=66.113.196.128 empty.
- viewdns.info/iphistory/?domain=sportsnewsfinder.com
- 50.63.202.58 United States AS-26496-GO-DADDY-COM-LLC 2013-03-23 some similar hits on other sites, possibly all flukes
- 207.150.219.159 United States AFFINITY-INTER 2013-03-02
- 66.113.196.128 United States NETNATION 2012-01-11. Tested.
newsworldsite.com:
- viewdns.info/iphistory/?domain=newsworldsite.com
- 68.178.232.100 United States AS-26496-GO-DADDY-COM-LLC 2013-05-20 big virtual
- 204.93.159.80 Chicago - United States SERVERCENTRAL 2013-04-21. Tested viewdns.info range: 204.93.159.70 204.93.159.90. viewdns.info/reverseip/?t=1&host=204.93.159.80 medium virtual.
- 204.93.159.84: team-merk.com 2011-08-11. No archives.
todaysnewsreports.net:
- viewdns.info/iphistory/?domain=todaysnewsreports.net
- 208.91.197.132 British Virgin Islands CONFLUENCE-NETWORK-INC 2013-07-01
- 205.178.189.129 United States NETWORK-SOLUTIONS-HOSTING 2013-05-20 likely virtual
- 173.255.131.72 Reno - United States UK-2 Limited 2012-08-27. Tested viewdns.info range: 173.255.131.62 173.255.131.82. Virtual and modern hits only.
- 67.213.211.232 United States UK-2 Limited 2011-09-07 unknown. Tested viewdns.info range: 67.213.211.222 67.213.211.242. viewdns.info/reverseip/?t=1&host=67.213.211.232 empty.
- 67.213.211.236: icf-finan.com 2015-01-20
- 67.213.211.237: playinside.me 2016-02-04. Nice domain hack, but no.
- 67.213.211.239: reality-sexxx.com 2011-09-08
hassannews.net:
- viewdns.info/iphistory/?domain=hassannews.net
- 208.91.197.132 British Virgin Islands CONFLUENCE-NETWORK-INC 2013-07-08
- 205.178.189.131 United States NETWORK-SOLUTIONS-HOSTING 2013-07-01. Likely virtual.
todayoutdoors.com:
- dnshistory.org/historical-dns-records/a/todayoutdoors.com
- 2009-08-11 -> 2010-07-07 174.133.44.90. Tested viewdns.info range: 174.133.44.80 174.133.44.100. Virtual and modern. viewdns.info/reverseip/?t=1&host=174.133.44.90 two modern domains.
- 2011-03-01 -> 2011-03-01 174.123.172.82 unknown. Tested viewdns.info range: 174.123.172.72 174.123.172.92. Virtuals.
- viewdns.info/iphistory/?domain=todayoutdoors.com
- 68.178.232.100 United States AS-26496-GO-DADDY-COM-LLC 2011-07-02 virtual
- 174.123.172.82 United States SOFTLAYER 2011-04-04. Tested.
globaltourist.net:
- dnshistory.org/historical-dns-records/a/ 2009-07-30 -> 2011-01-01 69.59.20.215 unknown. Tested viewdns.info range: 69.59.20.205 69.59.20.225. Virtuals.
- viewdns.info/iphistory/?domain=globaltourist.net
- 216.172.170.14 United States NETWORK-SOLUTIONS-HOSTING 2013-07-08
- 216.21.239.197 United States NETWORK-SOLUTIONS-HOSTING 2012-06-25
- 68.178.232.100 United States AS-26496-GO-DADDY-COM-LLC 2012-04-09 big virtual
- 174.136.34.154 United States IHNET 2012-03-12 unknown. Tested viewdns.info range: 174.136.34.144 174.136.34.164
- 74.119.145.101 Frankfurt am Main - Germany PERFORMIVE 2011-09-07. Tested viewdns.info range: 74.119.145.91 74.119.145.111. One virtual.
- 69.59.20.215 United States ATLRETAIL 2011-06-22. Tested viewdns.info/reverseip/?t=1&host=69.59.20.215
terrain-news.com:
- JAR
- viewdns.info/iphistory/?domain=terrain-news.com None in simple ranges.
- 204.11.56.25 British Virgin Islands CONFLUENCE-NETWORK-INC 2013-11-08. Virtuals.
- 208.91.197.19 British Virgin Islands CONFLUENCE-NETWORK-INC 2013-05-20. Virtual 167. viewdns.info/reverseip/?host=208.91.197.19&t=1 not very promising.
- eurotravelnyc.com legit web.archive.org/web/20110201195411/http://eurotravelnyc.com/
- 208.187.167.20 United States DATANOC 2012-01-11. Tested viewdns.info range: 208.187.167.10 208.187.167.30. Newer domains. viewdns.info/reverseip/?t=1&host=208.187.167.20 only has one conck.ooo. WTF.
- securitytrails.com/domain/terrain-news.com/history/a same:
intlnewsdaily.com
- dnshistory.org/historical-dns-records/a/intlnewsdaily.com 2010-02-21 -> 2010-08-06 75.126.136.179. unknown range. viewdns.info/reverseip/?t=1&host=75.126.136.179 empty checked 75.126.136.171 - 75.126.136.179
- viewdns.info/iphistory/?domain=intlnewsdaily.com
- 208.91.197.19 British Virgin Islands CONFLUENCE-NETWORK-INC 2013-05-20. Virtual. Tested.
- 63.247.95.50 Austell - United States NTHL 2012-06-29 unknown. Tested viewdns.info range: 63.247.95.40 63.247.95.60
- 63.247.95.50: 2b-sports.com 2013-04-21
- 63.247.95.50: caldentalinsurance.com 2014-07-05
- 63.247.95.50: cameronbal-photography.com 2012-06-29
- 63.247.95.50: congbetham.com 2014-07-05
- 63.247.95.50: essentialintelligenceagency.com 2023-03-07
- 63.247.95.50: isabellavalentina.com 2014-07-05
- 63.247.95.50: jhraccounting.com.au 2021-05-03
- 63.247.95.50: missouribreaks294.com 2012-06-29
- 63.247.95.50: startorganize.com 2011-08-11
- 63.247.95.50: tifocus.net 2011-08-11
- 63.247.95.50: tifocus.org 2011-08-10
- 63.247.95.50: whitepartyorlando.com 2012-01-11
- 204.11.56.25 (ipinf.ru) viewdns.info/reverseip/?t=1&host=204.11.56.25 Virtual 2,999
- securitytrails.com/domain/intlnewsdaily.com/history/a empty on dates
opensourcenewstoday.com:
- viewdns.info/iphistory/?domain=opensourcenewstoday.com
- 68.178.232.100 United States AS-26496-GO-DADDY-COM-LLC 2011-11-13 virtual
- 64.16.193.48 Riyadh - Saudi Arabia Saudi Telecom Company JSC 2011-09-08. Tested viewdns.info range: 64.16.193.38 64.16.193.55. Ran out. viewdns.info/reverseip/?t=1&host=64.16.193.48 virtual 55, lots of porn
- securitytrails.com/domain/opensourcenewstoday.com/history/a
techwatchtoday.com:
- viewdns.info/iphistory/?domain=techwatchtoday.com
- 208.91.197.132 British Virgin Islands CONFLUENCE-NETWORK-INC 2013-11-29 virtual
- 66.11.225.226 United States TNWEB-LEW-001 2012-01-11 unknown. Checked 66.11.225.220 - 66.11.225.233
- dnshistory.org/historical-dns-records/a/techwatchtoday.com 2009-08-11 -> 2011-02-26 66.11.225.226 big shared host
- securitytrails.com/domain/techwatchtoday.com/history/a same
CIA 2010 covert communication websites ipinf.ru Updated 2025-07-16
alljohnny.com had a hit: ipinf.ru/domains/alljohnny.com/, and so Ciro started looking around... and a good number of other things have hits.Not all of them, definitely less data than viewdns.info.
But they do reverse IP, and they show which nearby reverse IPs have hits on the same page, for free, which is great!
Shame their ordering is purely alphabetical, doesn't properly order the IPs so it is a bit of a pain, but we can handle it.
OMG, Russians!!!
CIA 2010 covert communication websites Overview of Ciro Santilli's investigation Created 2025-05-07 Updated 2025-07-19
Ciro Santilli hard heard about the 2018 Yahoo article around 2020 while studying for his China campaign because the websites had been used to take down the Chinese CIA network in China. He even asked on Quora about it, but there were no publicly known domains at the time to serve as a starting point. Chris, Electrical Engineer and former Avionics Tech in the US Navy, even replied suggesting that obviously the CIA is so competent that it would never ever have its sites leaked like that:
Seriously a dumb question.
In 2023, one year after the Reuters article had been published, Ciro Santilli was killing some time on YouTube when he saw a curious video: Video 1. "Compromised Comms by Darknet Diaries (2023)". As soon as he understood what it was about and that it was likely related to the previously undisclosed websites that he was interested in, he went on to read the Reuters article that the podcast pointed him to.
Being a half-arsed web developer himself, Ciro knows that the attack surface of a website is about the size of Texas, and the potential for fingerprinting is off the charts with so many bits and pieces sticking out. And given that there were at least 885 of them, surely we should be able to find a few more than nine, right?
In particular, it is fun how these websites provide to anyone "live" examples of the USA spying on its own allies in the form of Wayback Machine archives.
Given all of this, Ciro knew he had to try and find some of the domains himself using the newly available information! It was an irresistible real-life capture the flag.
Chris, get fucked.
It was the YouTube suggestion for this video that made Ciro Santilli aware of the Reuters article almost one year after its publication, which kickstarted his research on the topic.
Full podcast transcript: darknetdiaries.com/transcript/75/
Ciro Santilli pinged the Podcast's host Jack Rhysider on Twitter and he ACK'ed which is cool, though he was skeptical about the strength of the fingerprints found, and didn't reply when clarification was offered. Perhaps the material is just not impactful enough for him to produce any new content based on it. Or also perhaps it comes too close to sources and methods for his own good as a presumably American citizen.
The first step was to try and obtain the domain names of all nine websites that Reuters had highlighted as they had only given two domains explicitly.
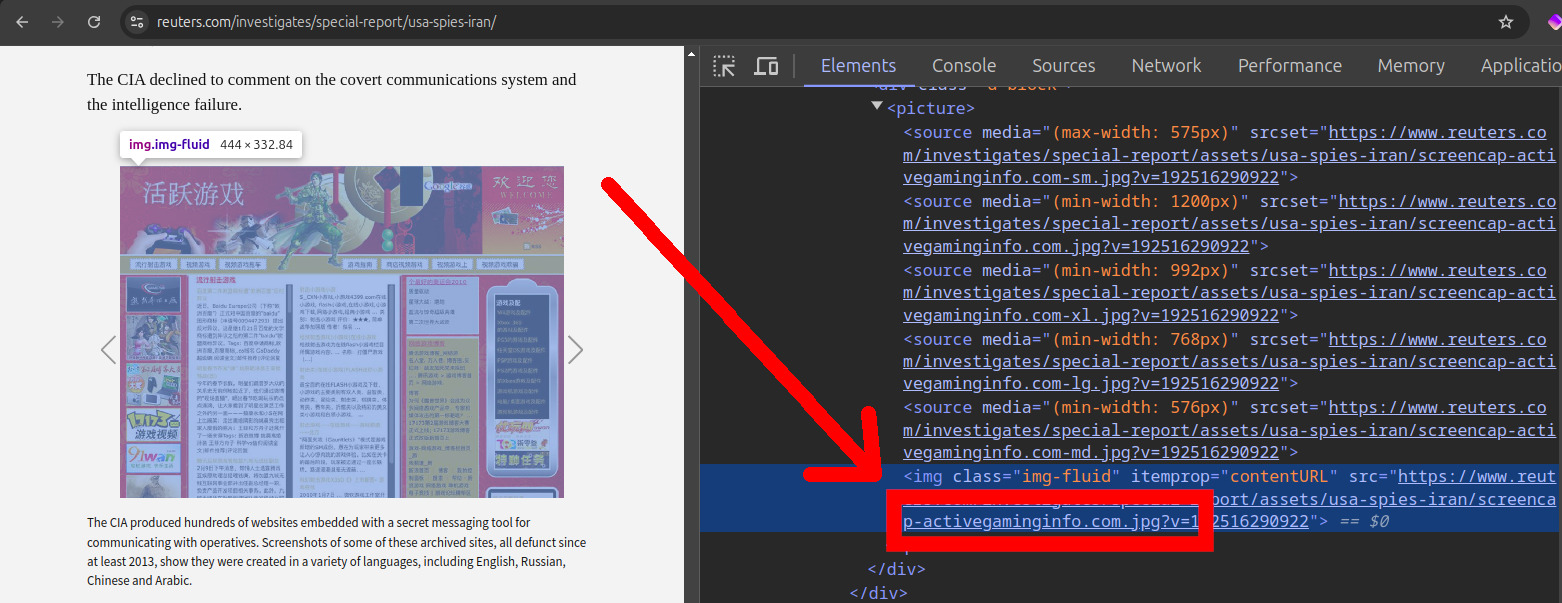
Thankfully however, either by carelessness or intentionally, this was easy to do by inspecting the address of the screenshots provided. For example, one of the URLs was:which corresponds to
https://www.reuters.com/investigates/special-report/assets/usa-spies-iran/screencap-activegaminginfo.com.jpg?v=192516290922activegaminginfo.com.Inspecting the Reuters article HTML source code
. Source. The Reuters article only gave one URL explicitly: iraniangoals.com. But most others could be found by inspecting the HTML of the screenshots provided, except for the Carson website.Once we had this, we were then able to inspect the websites on the Wayback Machine to better understand possible fingerprints such as their communication mechanism.
The next step was to use our knowledge of the sequential IP flaw to look for more neighbor websites to the nine we knew of.
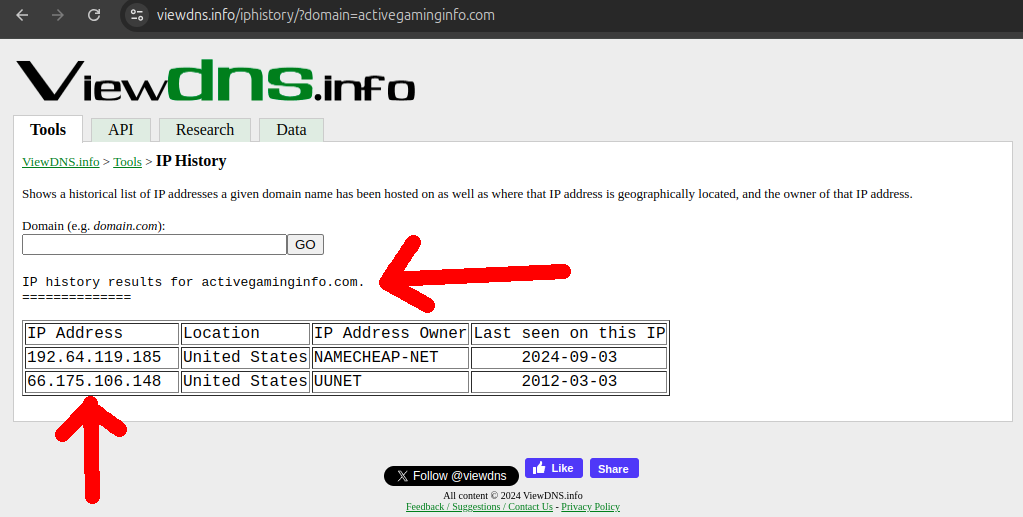
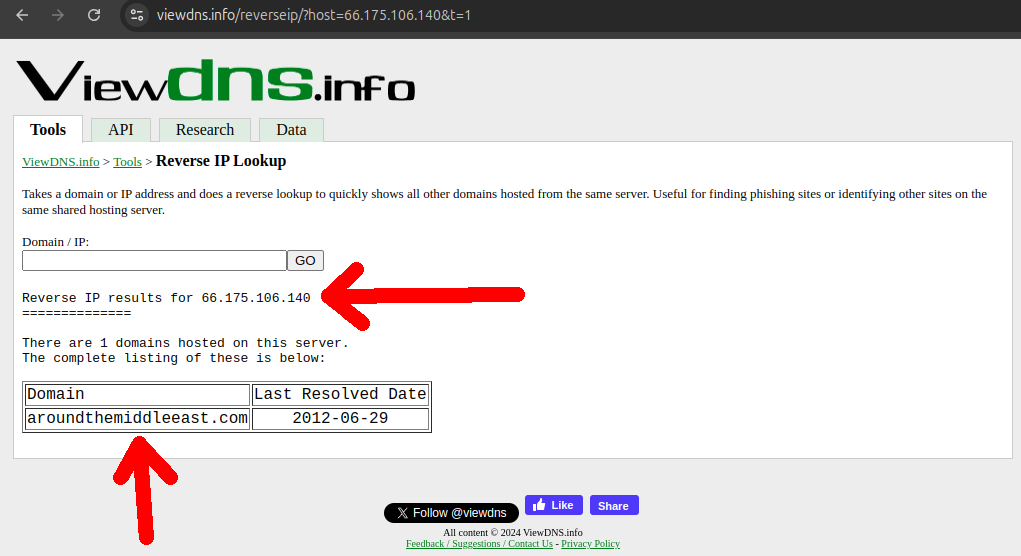
This was not so easy to do because the websites are down and so it requires historical data. But for our luck we found viewdns.info which allowed for 200 free historical queries (and they seem to have since removed this hard limit and moved to only throttling), leading to the discovery or some or our own new domains!
This gave us a larger website sample size in the order of the tens, which allowed us to better grasp more of the possible different styles of website and have a much better idea of what a good fingerprint would look like.
The next major and difficult step would be to find new IP ranges.
This was and still is a hacky heuristic process for us, but we've had the most success with the following methods:
- step 1) get huge lists of historic domain names. The two most valuable sources so far have been:
- step 2) filter the domain lists down somehow to a more manageable number of domains. The most successful heuristics have been:
- for 2013 DNS Census which has IPs, check that they are the only domain in a given IP, which was the case for the majority of CIA websites, but was already not so common for legitimate websites
- they have the word
newson the domain name, given that so many of the websites were fake news aggregators
- step 3) search on Wayback machine if any of those filtered domains contain URL's that could be those of a communication mechanism. In particular, we've used a small army of Tor bots to overcome the Wayback Machine's IP throttling and greatly increase our checking capacity
DNS Census 2013 website
. Source. This source provided valuable historical domain to IP data. It was likely extracted with an illegal botnet. Data excerpt from the CSVs:amazon.com,2012-02-01T21:33:36,72.21.194.1
amazon.com,2012-02-01T21:33:36,72.21.211.176
amazon.com,2013-10-02T19:03:39,72.21.194.212
amazon.com,2013-10-02T19:03:39,72.21.215.232
amazon.com.au,2012-02-10T08:03:38,207.171.166.22
amazon.com.au,2012-02-10T08:03:38,72.21.206.80
google.com,2012-01-28T05:33:40,74.125.159.103
google.com,2012-01-28T05:33:40,74.125.159.104
google.com,2013-10-02T19:02:35,74.125.239.41
google.com,2013-10-02T19:02:35,74.125.239.46The four communication mechanisms used by the CIA websites
. Java Applets, Adobe Flash, JavaScript and HTTPSExpired domain names by day 2011
. Source. The scraping of expired domain trackers to Github was one of the positive outcomes of this project. CIA 2010 covert communication websites Possible hits Created 2025-04-05 Updated 2025-07-16
Likely hits possible but whose archives is too broken to be easily certain. If:were to ever be found, these would be considered hits.
- nearby IP hits
- proper reverse engineering of their comms if any, or any other page fingerprints
- 216.97.231.56 nouvelles-d-aujourdhuis.com. 2011. Stylistically perfect, but no nearby IP hits. domainsbyproxy.com. Maybe looking into HTML would help confirm:But wrong IP? likely CGI comms variant under the signup page: web.archive.org/web/20090405045548/http://nouvelles-d-aujourdhuis.com/members.html.
rss-items
Tested viewdns.info range: 216.97.231.46 - 216.97.231.66. Not a single reverse IP hit in there.viewdns.info also assigns it 50.63.202.46, GoDaddy.com, LLC, 2013-11-08 in addition to 216.97.231.56, Canada, IPXO LLC, 2013-09-06. This is very near other iranfootballsource.com flukes, so likely useless.securitytrails.com also gives it one earlier IP 209.200.240.250 last seen 2008-09-20: securitytrails.com/domain/nouvelles-d-aujourdhuis.com/history/a Hydra Communications Ltd before 216.97.231.56 "ASU doctor" first seen 2008-09-20 (15 years)> Tested viewdns.info range: 209.200.240.240 - 209.200.240.260 empty at the time of interest.Marked copyright 2006, so mega early.
africainnews.com
- no archives of the HTML. dawhois.com/www/africainnews.com.html somewhat in-style but unclear.
- SWF. A reverse engineering of the SWF should be able to confirm.
- web.archive.org/web/20111007194814/http://africainnews.com/robots.txt
- dnshistory.org/historical-dns-records/a/africainnews.com
- 2009-12-29 -> 2010-07-28 72.167.232.43. Tested viewdns.info range: 72.167.232.33 - 72.167.232.53. Several virtual hosts there. viewdns.info/reverseip/?t=1&host=72.167.232.43 medium virtual haven't bothered to explore much
- 2011-10-14 -> 2011-10-14 68.178.232.100 virtual
- 2012-08-12 -> 2012-08-12 97.74.42.79. Tested viewdns.info range: 97.74.42.69 - 97.74.42.89
- 97.74.42.74: landtex.net 2023-03-22
- 97.74.42.76: solidasshonky.com 2023-03-07
- 97.74.42.77: solidasshonky.com 2023-03-07
- 97.74.42.78: blakebrothers.co 2018-05-05
- 97.74.42.78: learningjbe.com 2023-02-02
- 97.74.42.78: solidasshonky.com 2023-03-07
- 97.74.42.78: sourceuae.com 2023-03-07
- 97.74.42.78: superiorfoodservicesales.com 2017-09-10
- 97.74.42.79: large virtual
- 97.74.42.80: waiasialtd.com 2016-10-17
- viewdns.info/iphistory/?domain=africainnews.com
- 50.63.202.92 United States AS-26496-GO-DADDY-COM-LLC 2013-06-30. Likely large virtual.
- 97.74.42.79 United States AS-26496-GO-DADDY-COM-LLC 2013-05-20. tested.
- 68.178.232.100 United States AS-26496-GO-DADDY-COM-LLC 2012-06-29 virtual
- 68.178.232.99 United States AS-26496-GO-DADDY-COM-LLC 2011-11-13
- 68.178.232.100 United States AS-26496-GO-DADDY-COM-LLC 2011-10-09 virtual
- 72.167.232.43 United States GO-DADDY-COM-LLC 2011-09-08. Tested.
globalsentinelsite.com. dawhois.com/www/globalsentinelsite.com.html empty. Copyright 2011 on top and 2008 on bottom. Unusually wide, has a few sections, but somewhat shallow. Copyright 2008. JAR JAR. a.rss-item
- dnshistory.org/historical-dns-records/a/globalsentinelsite.com 2010-02-13 -> 2010-08-04 74.124.210.249 unknown
- viewdns.info/iphistory/?domain=globalsentinelsite.com
- 74.124.210.249 United States INMOTION 2011-11-13 unknown viewdns.info/reverseip/?host=74.124.210.249&t=1 has 347 hits
- JAR file structure:with:
./META-INF/MANIFEST.MF ./META-INF/WORLD.DSA ./META-INF/WORLD.SF ./global ./global/applet ./global/applet/A.class ./global/applet/Aa.class ./resource/resources.binManifest-Version: 1.0 Created-By: 1.4.2_15-b02 (Sun Microsystems Inc.) Ant-Version: Apache Ant 1.6.5 Name: global/applet/Bs.class SHA1-Digest: R1qrWUT6kYTLKa6TSmyWbBhLQSw= Name: global/applet/Ay.class SHA1-Digest: L0xOVdhBzEcmW8czjERAVH+tNyI=
todaysolar.com. This might just be legit, but keeping it around just in case.
- 2011
- JAR
- dnshistory.org/historical-dns-records/a/todaysolar.com 2009-08-11 -> 2011-03-01 74.208.62.112 unknown
- viewdns.info/iphistory/?domain=todaysolar.com 74.208.62.112 United States PROFITBRICKS-USA 2012-11-12
CIA 2010 covert communication websites securitytrails.com Updated 2025-07-16
They appear to piece together data from various sources. This is the most complete historical domain -> IP database we have so far. They don't have hugely more data than viewdns.info, but many times do offer something new. It feels like the key difference is that their data goes further back in the critical time period a bit.
TODO do they have historical reverse IP? The fact that they don't seem to have it suggests that they are just making historical reverse IP requests to a third party via some API?
E.g. searching
thefilmcentre.com under historical data at securitytrails.com/domain/thefilmcentre.com/history/al gives the correct IP 62.22.60.55.Account creation blacklists common email providers such as gmail to force users to use a "corporate" email address. But using random domains like
ciro@cirosantilli.com works fine.Their data seems to date back to 2008 for our searches.