The algorithm is completely analogous to Diffie-Hellman key exchange in that you efficiently raise a number to a power times and send the result over while keeping as private key.
The only difference is that a different group is used: instead of using the cyclic group, we use the elliptic curve group of an elliptic curve over a finite field.
Elliptic curves by Computerphile (2018)
Source. youtu.be/NF1pwjL9-DE?t=143 shows the continuous group well, but then fails to explain the discrete part.Variant of Diffie-Hellman key exchange based on elliptic curve cryptography.
- 2023 vimalabs.github.io/ VIMA: General Robot Manipulation with Multimodal Prompts
It doesn't need to be a bipedal robot. We can let Boston Dynamics worry about that walking balance crap.
It could very well instead be on wheels like arm on tracks.
Or something more like a factory with arms on rails as per:
- Transcendence (2014)
- youtu.be/MtVvzJIhTmc?t=112 from Video "Rotrics DexArm is available NOW! by Rotrics (2020)" where they have a sliding rail
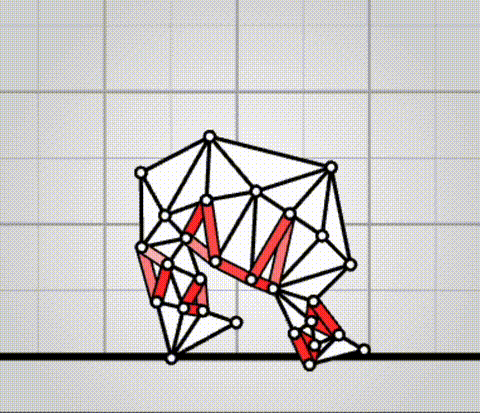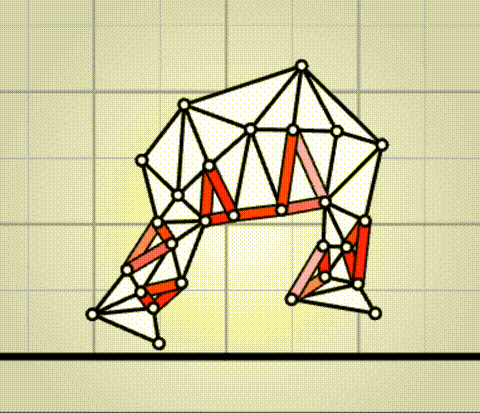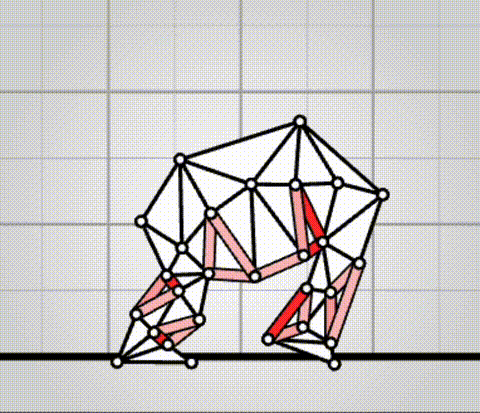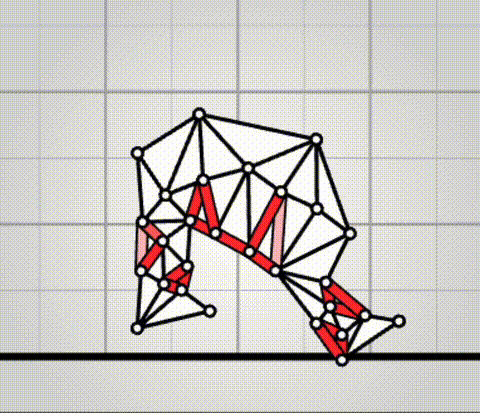
Algovivo demo
. github.com/juniorrojas/algovivo: A JavaScript + WebAssembly implementation of an energy-based formulation for soft-bodied virtual creatures.Our Final Invention - Artificial General Intelligence by Sciencephile the AI (2023)
. Source. AGI via simulation section.Ciro Santilli defines an "AI game" as:
a game that is used to train AI, in particular one that was designed with this use case in mind, and usually with the intent of achieving AGI, i.e. the game has to somehow represent a digital world with enough analogy to the real world so that the AGI algorithms developed there could also work on the real world
Most games played by AI historically so far as of 2020 have been AI for games designed for humans: Human game used for AI training.
Ciro Santilli took a stab at an AI game: Ciro's 2D reinforcement learning games, but he didn't sink too much/enough into that project.
Bibliography:
github.com/deepmind/lab/tree/master/game_scripts/levels/contributed/dmlab30 has some good games with video demos on YouTube, though for some weird reason they are unlisted.
TODO get one of the games running. Instructions: github.com/deepmind/lab/blob/master/docs/users/build.md. This may helpgithub.com/deepmind/lab/issues/242: "Complete installation script for Ubuntu 20.04".
It is interesting how much overlap some of those have with Ciro's 2D reinforcement learning games
- analyticsindiamag.com/5-open-source-recommender-systems-you-should-try-for-your-next-project/ 5 Open-Source Recommender Systems You Should Try For Your Next Project (2019)
He quit Mozilla in 2016 to try and commercialize an
rr extension called Pernosco.But as of 2022, he advertised himself as part of "Google Research", so maybe that went under, sample source: archive.ph/o9622. TODO when did he start? There's apparently an unrelated homonym: www.linkedin.com/in/rob-ocallahan/
He's apparently very religious, and very New Zelandish, twitter.com/rocallahan auto-describes:Terry A. Davis and D. Richard Hipp come to mind. One is tempted to speculate a correlation even, the proportion amongst systems programmers feels so much higher than in other areas of programming! Maybe it is because you have to be a God to do it in the first place.
Christian. Repatriate Kiwi.
Robert O'Callahan interview by Toby Ho (2022)
Source. Pinned article: Introduction to the OurBigBook Project
Welcome to the OurBigBook Project! Our goal is to create the perfect publishing platform for STEM subjects, and get university-level students to write the best free STEM tutorials ever.
Everyone is welcome to create an account and play with the site: ourbigbook.com/go/register. We belive that students themselves can write amazing tutorials, but teachers are welcome too. You can write about anything you want, it doesn't have to be STEM or even educational. Silly test content is very welcome and you won't be penalized in any way. Just keep it legal!
Intro to OurBigBook
. Source. We have two killer features:
- topics: topics group articles by different users with the same title, e.g. here is the topic for the "Fundamental Theorem of Calculus" ourbigbook.com/go/topic/fundamental-theorem-of-calculusArticles of different users are sorted by upvote within each article page. This feature is a bit like:
- a Wikipedia where each user can have their own version of each article
- a Q&A website like Stack Overflow, where multiple people can give their views on a given topic, and the best ones are sorted by upvote. Except you don't need to wait for someone to ask first, and any topic goes, no matter how narrow or broad
This feature makes it possible for readers to find better explanations of any topic created by other writers. And it allows writers to create an explanation in a place that readers might actually find it.Figure 1. Screenshot of the "Derivative" topic page. View it live at: ourbigbook.com/go/topic/derivativeVideo 2. OurBigBook Web topics demo. Source. - local editing: you can store all your personal knowledge base content locally in a plaintext markup format that can be edited locally and published either:This way you can be sure that even if OurBigBook.com were to go down one day (which we have no plans to do as it is quite cheap to host!), your content will still be perfectly readable as a static site.
- to OurBigBook.com to get awesome multi-user features like topics and likes
- as HTML files to a static website, which you can host yourself for free on many external providers like GitHub Pages, and remain in full control
Figure 3. Visual Studio Code extension installation.Figure 4. Visual Studio Code extension tree navigation.Figure 5. Web editor. You can also edit articles on the Web editor without installing anything locally.Video 3. Edit locally and publish demo. Source. This shows editing OurBigBook Markup and publishing it using the Visual Studio Code extension.Video 4. OurBigBook Visual Studio Code extension editing and navigation demo. Source. - Infinitely deep tables of contents:
All our software is open source and hosted at: github.com/ourbigbook/ourbigbook
Further documentation can be found at: docs.ourbigbook.com
Feel free to reach our to us for any help or suggestions: docs.ourbigbook.com/#contact