Accounts controlled by Ciro Santilli Updated 2026-01-30
Ciro Santilli controls the following accounts.
With non-trivial activity:
- github.com/cirosantilli on GitHub
- stackoverflow.com/users/895245 on Stack Overflow
- www.linkedin.com/in/cirosantilli on LinkedIn
- www.youtube.com/c/CiroSantilli on YouTube
- Twitter: see Section "Ciro Santilli's Twitter accounts"
- archive.org/details/@cirosantilli2 on the Internet Archive. Was archive.org/details/@cirosantilli but got deleted due to an "admin error" and the old username cannot be restored![ref]
- en.wikipedia.org/wiki/User:Cirosantilli2 and commons.wikimedia.org/wiki/User:Cirosantilli2: Ciro tries to upload all educational CC content he creates to Wikimedia Commons as an extra backup and sometimes to use in Wikipedia pages
- www.facebook.com/cirosantilli/ Ciro accepts all friend requests there, but expect a few non-technical posts. Unless you look like a massive honeypot account, please send context in advance in that case.
- www.quora.com/profile/Ciro-Santilli
- www.reddit.com/user/cirosantilli/ is Ciro's Reddit account, mostly computer and China topics
- maps.app.goo.gl/npV35XTppSBTmNqC8: Google Maps. Ciro Santilli likes to make additions to certain niche topics that are missing, having reached Local Guide Level 6 as of 2024. He can't do as much as he'd like so as to not reveal his current city however.
Trivial or no activity:
- seqanswers.com/forums/member.php?u=90053
- answers.gazebosim.org/users/2289/cirosantilli/
- 4programmers.net/Profile/86786
- 500px.com/p/cirosantilli
- 9gag.com/u/cirosantilli
- addons.mozilla.org/en-US/firefox/user/cirosantilli/
- agoradesk.com/user/cirosantilli
- anaconda.org/cirosantilli
- androidforums.com/members/ciro-santilli.1918307
- app.element.io/#/user/@cirosantilli:matrix.org. Proof: matrix.to/#/!OisxJPszSYdWdwXrrL:matrix.org/$YbrChbGFvlgYiDM5E2OgWXSp0vy7ayLfGkCXftAUyTI?via=matrix.org
- archive.org/details/@ciro_santilli_ourbigbook created during the account deletion mess.
- ask.libreoffice.org/en/users/2352/cirosantilli/
- bbs.archlinux.org/profile.php?id=116270
- bitcointalk.org/index.php?action=profile
- brilliant.org/profile/ciro-il1uxz/
- bsky.app/profile/cirosantilli.bsky.social
- bugzilla.gnome.org/page.cgi?id=describeuser.html&login=ciro.santilli@gmail.com
- cirosantilli.blogspot.com/
- cirosantilli.itch.io
- cirosantilli.livejournal.com/profile
- cirosantilli.medium.com/ on Medium
- cirosantilli.substack.com/ and substack.com/@cirosantilli
- cirosantilli.wordpress.com/ on WordPress
- codeforces.com/profile/cirosantilli reverse proof codeforces.com/blog/entry/98393
- coderwall.com/Ciro%20Santilli Note that space on the username. Beauty.
- community.arm.com/people/cirosantilli
- community.atlassian.com/t5/user/viewprofilepage/user-id/680821
- community.fandom.com/wiki/User:Cirosantilli
- community.openai.com/u/cirosantilli
- community.plos.org/people/cirosantilli
- community.skype.com/t5/user/viewprofilepage/user-id/2646858
- community.zimbra.com/members/cirosantilli
- connect.mozilla.org/t5/user/viewprofilepage/user-id/46889
- del.icio.us/cirosantilli
- dev.to/cirosantilli
- developer.mbed.org/users/cirosantilli/
- devtalk.nvidia.com/member/2118846/
- droit-finances.commentcamarche.net/profile/user/cirosantilli
- en.gravatar.com/cirosantilli
- en.wikipedia.org/wiki/User:Ciro.santilli also belongs to Ciro, but he lost the password
- eternagame.org/web/player/260828/
- exercism.org/profiles/cirosantilli
- figshare.com/authors/Ciro_Santilli/656781
- forums.developer.nvidia.com/u/cirosantilli
- forum.osdev.org/memberlist.php?mode=viewprofile&u=16372
- forum.pine64.org/member.php?action=profile&uid=17386
- forum.videolan.org/memberlist.php?mode=viewprofile&u=173503
- forum.xda-developers.com/member.php?u=7116837
- forums.androidcentral.com/members/cirosantilli-2734491
- forums.lenovo.com/user/viewprofilepage/user-id/1561639
- forums.hardwarezone.com.sg/members/cirosantilli.875544/
- framasphere.org/people/78a975c0b6c40133a3032a0000053625 framasphere.org/posts/1519871
- freesound.org/people/cirosantilli
- gitlab.com/u/cirosantilli
- hackaday.io/cirosantilli
- hinative.com/en-US/profiles/5276462
- home.gamer.com.tw/homeindex.php?owner=cirosantilli but can't post anything publicly because cannot verify phone in many countries
- huggingface.co/cirosantilli
- identity.kde.org/index.php?r=people/view&uid=cirosantilli
- imgur.com/user/cirosantilli/about: Proof: imgur.com/gallery/mexv1Bk/comment/1734086983
- jsfiddle.net/user/cirosantilli/
- kiwifarms.net/members/cirosantilli.82011/
- knockout.chat/user/22882
- launchpad.net/~cirosantilli
- leanprover.zulipchat.com/#user/1019866
- leanpub.com/u/cirosantilli
- leetcode.com/cirosantilli/
- makandracards.com/ciro-santilli
- mastodon.social/@cirosantilli
- nanohub.org/members/146301/
- next-episode.net/user/cirosantilli/
- openclipart.org/artist/cirosantilli. TODO but not yet able to login after the "first upload". But it did get uploaded: openclipart.org/artist/cirosantilli.
- opencollective.com/ciro-santilli
- open.spotify.com/user/cirosantilli
- orcid.org/0000-0003-2895-7763
- parler.com/profile/cirosantilli/posts
- paypal.me/cirosantilli. United Kingdom account.
- peerj.com/cirosantilli/
- profile.edx.org/u/ciro_santilli
- profiles.3dgames.com.ar/profiles/1002278
- protonmail.uservoice.com/users/6491333990-ciro-santilli
- pypi.org/user/cirosantilli/
- raidforums.com/User-cirosantilli
- rubygems.org/profiles/cirosantilli
- software.intel.com/en-us/user/1090688
- soundcloud.com/cirosantilli
- sourceforge.net/u/cirosantilli/profile/
- stackshare.io/cirosantilli
- steamcommunity.com/id/cirosantilli/
- subreply.com/cirosantilli
- support.discord.com/hc/en-us/profiles/427813342894 on the Discord forum
- support.mozilla.org/en-US/user/cirosantilli
- tabmixplus.org/forum/memberlist.php?mode=viewprofile&u=59846
- talk.commonmark.org/users/cirosantilli
- talk.jekyllrb.com/users/cirosantilli
- talks.cam.ac.uk/user/show/81142
- tatoeba.org/eng/user/profile/cirosantilli
- telegram.me/cirosantilli on Telegram
- trac.ffmpeg.org/wiki/Waveform?action=history username
cirosantilli - tuleap.net/users/cirosantilli
- tuleap.ring.cx/users/cirosantilli
- twittercommunity.com/users/cirosantilli/activity
- wefunder.com/cirosantilli
- wise.com/pay/me/cirod3. The name shows as "Ciro Duran Santilli" and that's correct.
- wiki.qemu.org/User:Cirosantilli
- www.airbnb.com/users/show/45794827
- www.behance.net/cirosantilli
- www.bibsonomy.org/user/cirosantilli
- www.biostars.org/u/50170/
- www.bountysource.com/people/25676-ciro-santilli
- www.bulletphysics.org/Bullet/phpBB3/memberlist.php?mode=viewprofile&u=11704
- www.codewars.com/users/cirosantilli
- www.codingame.com/profile/cddd0a711c22d97e8264361f7c8205567563841
- www.coursera.org/user/f65b08c191d792eb809fe2808d771ee7
- www.dailymotion.com/cirosantilli
- www.deviantart.com/cirosantilli
- www.digitalocean.com/community/users/cirosantilli
- www.ebay.com/usr/cirosantilli
- www.edaboard.com/member587087.html
- www.flickr.com/people/cirosantilli/. Account auto deleted tested as of 2025. Created: flickr.com/photos/202496646@N08/. Was something nicer, tried to change username to
cirosantilli2but got hat instead. Alsocirosantilliwas marked taken. What a bullshit website! Poor Canadians, sold off to Yahoo and let their baby be mutilated. - www.freecodecamp.org/fcc8f660b91-167c-4b04-a8da-5d50cdb46def
- www.f6s.com/cirosantilli
- www.f6s.com/cirosantilli1
- www.gitbook.com/@cirosantilli
- www.hackerrank.com/cirosantilli
- www.hackster.io/cirosantilli
- www.html5gamedevs.com/profile/30103-cirosantilli/
- www.imdb.com/user/ur59802249 on IMDb
- www.instagram.com/cirosantilli/ Impossible to disable their notifications without removing your email. So all their notifications go to trash.
- www.kaggle.com/cirosantilli
- www.lesswrong.com/users/ciro-santilli on LessWrong
- www.linux.org/members/ciro-santilli.62540/
- www.linuxquestions.org/questions/user/cirosantilli-688439/
- www.meetup.com/members/252568305/
- www.mentebinaria.com.br/profile/1987-ciro-santilli/
- www.metacritic.com/user/cirosantilli
- www.metaculus.com/accounts/profile/163587/
- www.mohu.rocks/people/cirosantilli
- www.mudhut.com/user/1995000
- www.myopportunity.com/en/profile/ciro-santilli
- www.npmjs.com/~cirosantilli
- www.opengl.org/discussion_boards/member.php/40269-cirosantilli
- www.openstreetmap.org/user/Ciro%20Santilli
- www.patreon.com/cirosantilli
- www.physicsforums.com/members/cirosantilli.422056/
- www.pixiv.net/en/users/64347194
- www.plurk.com/cirosantilli
- www.raspberrypi.org/forums/memberlist.php?mode=viewprofile&u=273389
- www.shadertoy.com/user/cirosantilli
- www.strava.com/athletes/47913768
- www.tastekid.com/ciro.santilli
- www.ted.com/profiles/5822760
- www.threads.com/@cirosantilli
- www.thestudentroom.co.uk/member.php?u=5930160
- www.tiktok.com/@cirosantilli2
- www.transifex.com/user/profile/cirosantilli
- www.tripadvisor.com/members/cirosantilli
- www.twitch.tv/cirosantilli
- www.whatdotheyknow.com/user/ciro_santilli/profile "Banned for spamming" as of 2024. One of those idiotic websites where you can't add a link to your homepage to your own profile page.
Lost or deleted:
- projecteuler.net/profile/cirosantilli.png Blocked 2025-10-01 due to their stupid policy that you can't give away answers within 12 hours of: github.com/lucky-bai/projecteuler-solutions/pull/94
Accounts in Chinese websites. These accounts might be banned or altered or offer other limitations, so Ciro only communicates briefly through them. All communication through those channels should obviously be assumed to be compromised:
- bbs.nibaedu.com/index.php?m=space&uid=70
- www.renren.com/338003848/profile
- www.tianya.cn/109285544 (can't post, no cell phone)
- hacpai.com/member/cirosantilli unable to login as of 2019-10-12, reason unclear, either ban or website too crappy.
- pincong.rocks/people/cirosantilli Lost account tested as of 2022-11 and likely much earlier. Last existing password not working, and there doesn't seem to be a reset password button. Creating cirosantilli2
- pincong.rocks/people/cirosantilli2
- tieba.baidu.com/home/main?id=5cd56369726f73616e74696c6c69c944
- v2ex.com/member/cirosantilli: Ciro was blocked and or account deleted on 2020-07-23: cirosantilli.com/china-dictatorship/v2ex
- v2ex.com/member/cirosantilli2: was created by someone else most likely and cannot be re-registered. Also blocked.
- v2ex.com/member/cirosantilli3: Ciro created this new account November 2023, let's see how long it lasts.
- www.zhihu.com/people/cirosantilli. Ciro was prevented from posting in 2018-06-25, and the account and all content mentioning him were taken down in 2019-11-03.
- www.weibo.com/p/1005055601627311: started requiring a cell phone to login in 2020, and Ciro didn't want to give his cell phone number to the CCP and didn't have the patience to manage a secondary phone number, so he is not logging in for now. The account was blocked in 2021: cirosantilli.com/china-dictatorship/ciro-santillis-weibo-block
Dead websites:
- www.citeulike.org/user/cirosantilli (2019-05)
CIA 2010 covert communication websites Timeline of public disclosures Created 2025-05-07 Updated 2025-07-26
The existence of the websites emerged in various stages, some of which may refer to this network or to other closely related communications failure since the published information is sometimes not clear enough.
May 21, 2011: various Iranian news outlets reported that:Iranian sources include:The news were picked up and repeated by Western outlets on the same day e.g.:At this point there were still no clear indications that the recruitment had been made with websites, however later revelations would later imply that.
30 individual suspected of spying for the US were arrested and 42 CIA operatives were identified in connection with the network.
- web.archive.org/web/20110729150642/http://www.presstv.ir/detail/180976.html "Iran dismantles US-linked spy network by Press TV (English, quoted above)
- web.archive.org/web/20110527084527/https://www.mehrnews.ir/NewsPrint.aspx?NewsID=1316973 "CIA spy network dismantled/30 American spies arrested" by Mehr news (Farsi)
- shiatv.net/video/dd6ee2d708a4a6cb2429 "Iran dismantles US-linked spy network" broadcast by IRIB, the main Iranian public broadcaster
- www.latimes.com/archives/blogs/babylon-beyond/story/2011-05-21/iran-intelligence-ministry-claims-to-arrest-30-alleged-cia-spies "Intelligence Ministry claims to arrest 30 alleged CIA spies" by the Los Angeles Times
Quite prophetically, this was on the same day that Christian radio broadcaster Harold Camping predicted that the world would come to an end.
December 2014: McClathy DC reported on "Intelligence, defense whistleblowers remain mired in broken system" that CIA contractor John A. Reidy had started raising concerns about the security of a communication systems used by the CIA and other sources mention that he started this in 2008[ref] The focus of the article is how he was then ignored and silenced for raising these concerns, which later turned out to be correct and leading to an intelligence catastrophe that started in 2010.[ref][ref] This appears to have come out after a heavily redacted appeal by Reidy against the CIA from October 2014 came into McClathy's possession.[ref] While Reidy's disclosures were responsible and don't give much away, given the little that they disclose it feels extremely likely that they were related to the same system we are interested in. Even heavily redacted, the few unredacted snippets of the appeal are pure gold and give a little bit of insight into the internal workings of the CIA. Some selections:
From January 2005 until January 2009, I worked as a government contractor at the CIA. I was assigned to [Directorate](ledger item 1) in the [Division] (ledger item 2). I served as a Uob) (ledger item 3) whose responsibility was to facilitate the dissemination of intelligence reporting to the Intelligence Community. I also served as a Oob 2) (ledger item 4) whose responsibility was to identify Human Intelligence (humint) targets of Interest for exploitation. I was assigned the telecommunications and information operations account.
As our efforts increased, we started to notice anomalies in our operations and conflicting intelligence reporting that indicated that several of our operations had been compromised. The indications ranged from [ redacted ] to sources abruptly and without reason ceasing all communications with us.
These warning signs were alarming due to the fact that our officers were approaching sources using [operational technique] (ledger item 16)
When our efforts began, ultimate operational authority rested with us. The other component provided the finances for the operation while we gave the operational guidance and the country specific knowledge.
knew we had a massive intelligence failure on our hands. All of our assets [ redacted ] were in jeopardy.
To give our compromise context, the U.S. communications infrastructure was under siege
All of this information was collected under the project cryptonym [cryptonym] (ledger item 52)
Meanwhile throughout 2010, I started to hear about catastrophic intelligence failures in the government office I formally worked for. More than one government employee reached out to me and notified me that the "nightmare scenario" I had described and tried to prevent had transpired. I was told that in upwards of 70% of our operations had been compromised.
it is not just a potential compromise in one country, It effects every country
May 2017: Mazzetti et al. reported for the New York Times at "Killing C.I.A. Informants, China Crippled U.S. Spying Operations" that:and that:
The Chinese government systematically dismantled C.I.A. spying operations in the country starting in 2010, killing or imprisoning more than a dozen sources over two years and crippling intelligence gathering there for years afterward.
January 2018: Pete Williams reported for NCB News at Alleged CIA China turncoat Lee may have compromised U.S. spies in Russia too that it was China that told Russia about the communications system:and that some theorize that former CIA agent Jerry Chun Shing Lee had betrayed Chinese spies, which some theorize may have been how China became aware of the communication network:According to Ex-C.I.A. Officer Sentenced to 19 Years in Chinese Espionage Conspiracy from November 2019 Lee was sentenced to 19 years in prison:
It was a shocking blow to an American spy agency that prides itself on its field operations. There was also a devastating human cost: Some 20 CIA sources were executed by the Chinese government, two former officials said — a higher number of dead than initially reported by NBC News and the New York Times. Then an unknown number of Russian assets also disappeared, sources say.
Soon after the task force concluded the Chinese had penetrated covcom, it got an even more troubling report: That after a joint training session between Chinese and Russian intelligence officers, the Russians "came back saying we got good info on covcom," as the former official put it
FBI agents began to suspect Lee after they received a tip that he had passed information to Chinese intelligence officers while working for a Japanese tobacco company in Hong Kong, sources said, a detail first reported Thursday by the New York Times. They also found it suspicious when Lee took a job at an auction house in Hong Kong that was co-owned by a senior Communist Party official, sources said. He eventually ended up working for Christie's, the international auction house.When agents searched Lee's hotel rooms in 2012, they found notebooks with the names of covert CIA sources, according to court documents.But not all of the agent arrests and deaths could be linked to information possessed by Lee, who left the CIA in 2007, the former officials said.
The former officer, Jerry Chun Shing Lee, 55, pleaded guilty in May to conspiring with Chinese intelligence agents starting in 2010, after he left the agency. Prosecutors detailed a long financial paper trail that they said showed that Mr. Lee received more than $840,000 for his work.
But F.B.I. agents who investigated whether he was the culprit passed on an opportunity to arrest him in the United States in 2013, allowing him to travel back to Hong Kong even after finding classified information in his luggage. F.B.I. agents had also covertly entered a hotel room Mr. Lee occupied in 2012, finding handwritten notes detailing the names and numbers of at least eight C.I.A. sources that he had handled in his capacity as a case officer.
Jerry Chun Shing Lee in blue tie at the unveiling of Leonardo da Vinci's 'Salvator Mundi' painting at the Christie's showroom in Hong Kong on Oct. 13, 2017
. Source. August 2018: Zach Dorfman reported for Foreign Policy at "Botched CIA Communications System Helped Blow Cover of Chinese Agents" that:and:Although no clear mention of websites is made in that article, the fact that there were "links" back to the CIA website strongly suggests that the communication was done through websites.
It was considered one of the CIA’s worst failures in decades: Over a two-year period starting in late 2010, Chinese authorities systematically dismantled the agency’s network of agents across the country, executing dozens of suspected U.S. spies. But since then, a question has loomed over the entire debacle. How were the Chinese able to roll up the network?
U.S. intelligence officers were also able to identify digital links between the covert communications system and the U.S. government itself, according to one former official—links the Chinese agencies almost certainly found as well. These digital links would have made it relatively easy for China to deduce that the covert communications system was being used by the CIA. In fact, some of these links pointed back to parts of the CIA’s own website, according to the former official.
The report also reveals that there was a temporary "interim system" that new sources would use while they were being vetted, but that it used the same style of system as the main system. It would be cool if we managed to identify which sites are interim or not somehow:
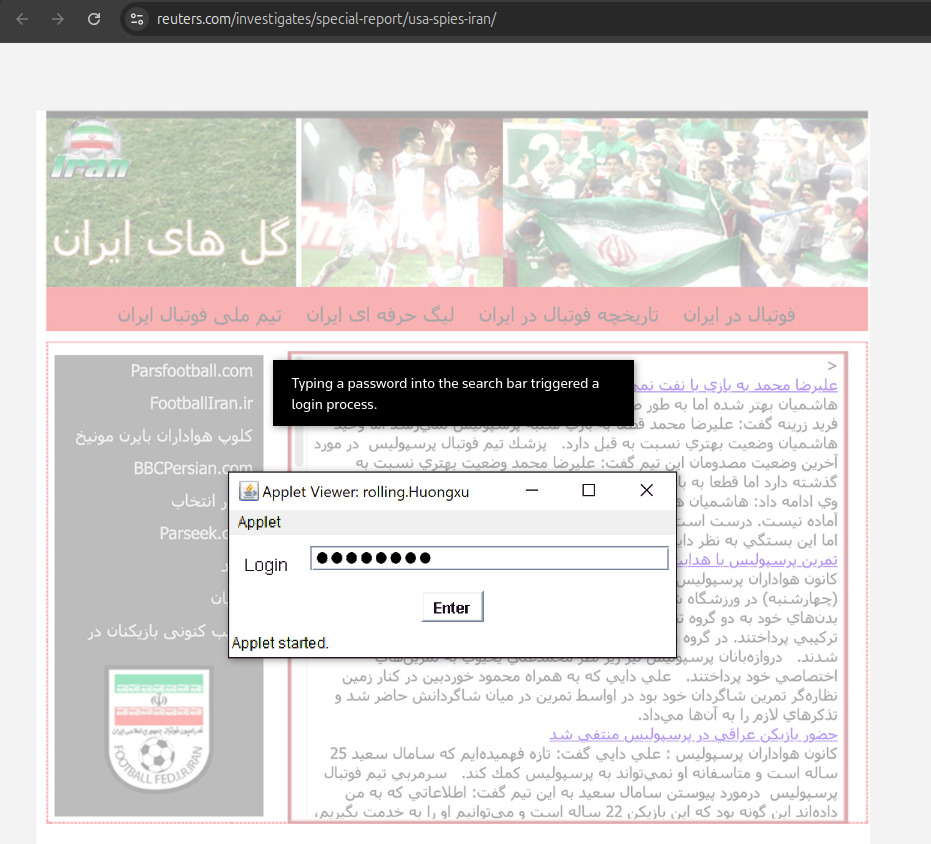
When CIA officers begin working with a new source, they often use an interim covert communications system—in case the person turns out to be a double agent.The communications system used in China during this period was internet-based and accessible from laptop or desktop computers, two of the former officials said.This interim, or “throwaway,” system, an encrypted digital program, allows for remote communication between an intelligence officer and a source, but it is also separated from the main communications system used with vetted sources, reducing the risk if an asset goes bad.
November 2018: Zach Dorfman and Jenna McLaughlin reported for Yahoo News the first clear report that the communication system was made up of websites at: "The CIA's communications suffered a catastrophic compromise. It started in Iran.":
In 2013, hundreds of CIA officers — many working nonstop for weeks — scrambled to contain a disaster of global proportions: a compromise of the agency’s internet-based covert communications system used to interact with its informants in dark corners around the world. Teams of CIA experts worked feverishly to take down and reconfigure the websites secretly used for these communications
The usage of of Google dorking is then mentioned:It seems to us that this would have been very difficult on the generically themed websites that we have found so far. This suggests the existence of a separate recruitment website network, perhaps the one reported in 2011 by Iran offering VISAs. It would be plausible that such network could link back to the CIA and other government websites. Recruited agents would only then later use the comms network to send information back. The target countries may have first found the recruitment network, and then injected double agents into it, who later came to know about the comms network. TODO: it would be awesome to find some of those recruitment websites!
In fact, the Iranians used Google to identify the website the CIA was using to communicate with agents.
Another very interesting mention is the platform had been over extended beyond its original domain application, which is in part why things went so catastrophically bad:
Former U.S. officials said the internet-based platform, which was first used in war zones in the Middle East, was not built to withstand the sophisticated counterintelligence efforts of a state actor like China or Iran. “It was never meant to be used long term for people to talk to sources,” said one former official. “The issue was that it was working well for too long, with too many people. But it was an elementary system.”
December 2018: a followup Yahoo News article "At the CIA, a fix to communications system that left trail of dead agents remains elusive" gives an interesting internal organizational overview of the failed operation:Much as in the case of Reidy, it is partly because of such internal dissatisfaction that so much has come out to the press, as agents feel that they have nowhere else to turn to.
Ciro Santilli conjectures that this fiasco was the motivation behind the creation of the Directorate of Digital Innovation.
As a result, many who are directly responsible for working with sources on the ground within the CIA’s Directorate of Operations are furious
The fiascos in Iran and China continue to be sticking points between the Directorate of Operations and the CIA’s Directorate of Science and Technology (DS&T) — the technical scientists. “There is a disconnect between the two directorates,” said one former CIA official. “I’m not sure that will be fixed anytime soon.”
Entire careers in the CIA’s Office of Technical Service — the part of DS&T directly responsible for developing covert communications systems — were built on these internet-based systems, said a former senior official. Raising concerns about them was “like calling someone’s baby ugly,” said this person.
Ciro Santilli conjectures that this fiasco was the motivation behind the creation of the Directorate of Digital Innovation.
That article also gives a cute insight into the OPSEC guidelines for the assets that used the websites:
CIA agents using the system were supposed to conduct “electronic surveillance detection routes” — that is, to bounce around on various sites on the internet before accessing the system, in order to cover their tracks — but often failed to do so, creating potentially suspicious patterns of internet usage, said this person.
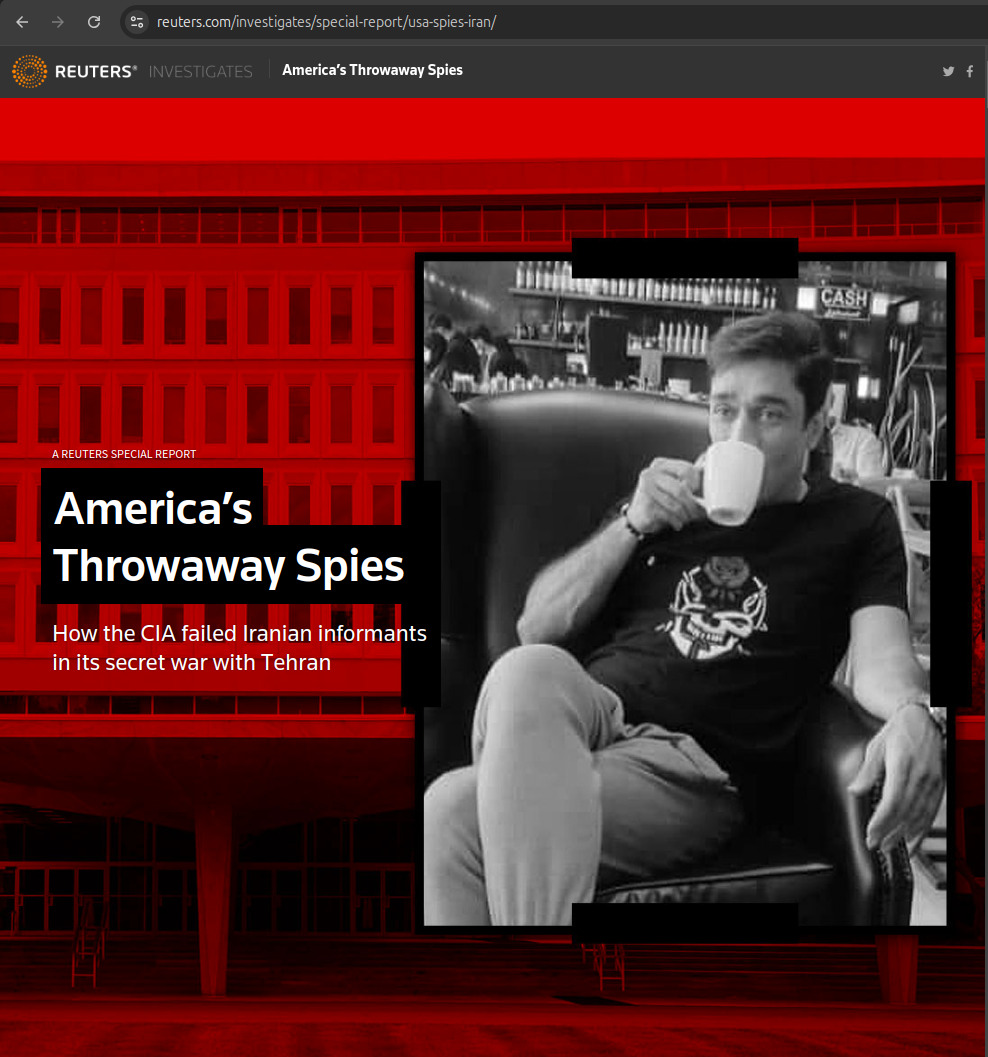
29 September 2022: Reuters reported nine specific websites of the network at "America's Throwaway Spies", henceforth known only as "the Reuters article" in this article.
The most important thing that this article gave were screenshots of nine websites, including the domain names of two of them: iraniangoals.com and iraniangoalkicks.com:The "350-plus" number is a bit random, given that their own analysts stated a much higher 885 in their report.
In addition, some sites bore strikingly similar names. For example, while Hosseini was communicating with the CIA through Iraniangoals.com, a site named Iraniangoalkicks.com was built for another informant. At least two dozen of the 350-plus sites produced by the CIA appeared to be messaging platforms for Iranian operatives, the analysts found.
The article also reveals the critical flaw of the system; the usage of sequential IPs:
Online records they analyzed reveal the hosting space for these front websites was often purchased in bulk by the dozen, often from the same internet providers, on the same server space. The result was that numerical identifiers, or IP addresses, for many of these websites were sequential, much like houses on the same street.
It also mentions that other countries besides Iran and Chine were also likely targeted:
This vulnerability went far beyond Iran. Written in various languages, the websites appeared to be a conduit for CIA communications with operatives in at least 20 countries, among them China, Brazil, Russia, Thailand and Ghana, the analysts found.
Reuters reconstruction of what the iraniangoals.com applet would have looked like
. Source. 29 September 2022: on the same day that Reuters published their report, Citizenlab, which Reuters used as analysts for the article, also simultaneously published their more technical account of things at "Statement on the fatal flaws found in a defunct CIA covert communications system".
One of the most important information given in that report is the large number of sites found, 885, and the fact that they are available on Wayback Machine:The million dollar question is "which website did they use" and "how much does it cost if anything" since our investigation has so far had to piece together a few different hacky sources but didn't spend any money. And a lot of money could be poured into this, e.g. DomainTools which might contain one of the largest historical databases, , seems to start at 15k USD / 1000 queries. One way to try and deduce which website they used is to look through their other research, e.g.:
Using only a single website, as well as publicly available material such as historical internet scanning results and the Internet Archive's Wayback Machine, we identified a network of 885 websites and have high confidence that the United States (US) Central Intelligence Agency (CIA) used these sites for covert communication.
- citizenlab.ca/2021/07/hooking-candiru-another-mercenary-spyware-vendor-comes-into-focus/ uses Censys, and it notably has historical data:Censys employee Silas Cutler AKA p1nk believes that Censys data does not reach that far back, since the company was only founded in 2017[ref].
- citizenlab.ca/2016/08/million-dollar-dissident-iphone-zero-day-nso-group-uae/ mentions scans.io/
- citizenlab.ca/2020/12/running-in-circles-uncovering-the-clients-of-cyberespionage-firm-circles/ mentions: www.shodan.io/
The article mentioned the different types of communication mechanisms found:
The websites included similar Java, JavaScript, Adobe Flash, and CGI artifacts that implemented or apparently loaded covert communications apps. In addition, blocks of sequential IP addresses registered to apparently fictitious US companies were used to host some of the websites. All of these flaws would have facilitated discovery by hostile parties.
They also give the dates range in which the system was active, which is very helpful for better targeting our searches:
And then a bomb, they claim to have found information regarding specific officers:This basically implies that they must have eitherWe have so for not yet found any such clear references to real individuals.
Nevertheless, a subset of the websites are linked to individuals who may be former and possibly still active intelligence community employees or assets:Given that we cannot rule out ongoing risks to CIA employees or assets, we are not publishing full technical details regarding our process of mapping out the network at this time. As a first step, we intend to conduct a limited disclosure to US Government oversight bodies.
- Several are currently abroad
- Another left mainland China in the time frame of the Chinese crackdown
- Another was subsequently employed by the US State Department
- Another now works at a foreign intelligence contractor
- found some communication layer level identifier, e.g. domain name registration HTTPS certificate certificate because it is impossible to believe that real agent names would have been present on the website content itself!
- or they may be instead talking about a separate recruitment network which offered the VISAs which we conjecture might have existed but currently have no examples of, and which might conceivably contain real embassy contacts
October 2022 Zach Dorfman, author of the 2018 Yahoo News and Foreign Policy articles gave some good anecdotes he had heard from his sources after the Reuters expose in his personal blog post On Agent Compromise in the Field, giving a more personal account of some of the events that took place:
Now, an important caveat: I have known dedicated former CIA officials who have spoken of the care, respect, and obligation they felt toward their sources, and the lengths they would go to assist them. For many case officers — that is, the CIA's primary corps of spy handlers — this is a core part of their professional identity.During the roll-up in China, for instance, a former U.S. official told me about a CIA officer who, aware that something was going terribly wrong there, organized final, assuredly dangerous, in-person meetings with agency sources. This distraught CIA officer essentially shoved wads of cash into sources' hands. This CIA officer warned them of the unfolding disaster and begged them to leave the country as fast as they could. Another source told me a story about a CIA official who, while being debriefed in Langley about the asset roll-up — and the slapdash COVCOM system — broke down in tears upon hearing that sources’ lives had been destroyed because of such obvious dereliction, of which they were previously unaware.
But I don’t want to oversell this point, either. By its nature, the world of espionage is steeped in the sordid aspects of human experience, exploiting people’s vulnerabilities for narrow informational gain. [...]Indeed, many former CIA officials have a decidedly pragmatic and amoral conception of their profession. Bad things happen when you spy, or recruit others to do so. [...] I had a conversation once with a former senior CIA official with experience in Iran issues who had an almost naturalistic view of recurring asset losses there over the years: for him, it was a built-in, cyclical feature of the work and environment, like the denuding of deciduous forests every fall.
Discovery Of The Elements by Mary Elvira Weeks Created 2024-09-15 Updated 2025-07-16
6th edition (1956) on the Internet Archive: archive.org/details/discoveryoftheel002045mbp
Enrico Fermi: physicist by Emilio Segrè (1970) Updated 2025-07-16
Biography of Enrico Fermi by fellow physicist, free rent on the on the Internet Archive: archive.org/details/enricofermiphysi0000segr
Internet Archive Open Library Updated 2025-07-16
Previously called "Lending Library" it seems: help.archive.org/hc/en-us/articles/360016554912-Borrowing-From-The-Lending-Library
You can borrow online books from them for a few hours/days: help.archive.org/hc/en-us/articles/360016554912-Borrowing-From-The-Lending-Library This is the most amazing thing ever made!!! You can even link to specific pages, e.g. archive.org/details/supermenstory00murr/page/80/mode/2up
They seem to a have a separate URL with the same content as well for some reason: openlibrary.org/, classic messy Internet Archive style.
Bastards are suing them www.theverge.com/2020/6/1/21277036/internet-archive-publishers-lawsuit-open-library-ebook-lending: Hachette, Penguin Random House, Wiley, and HarperCollins
It is quite hard to decide if an upload is from the official legal lending library, or just some illegal upload, e.g.:so the URLs are basically the same style. Some legality indicators:
- archive.org/details/TheGoogleStory likely illegal
- archive.org/details/isbn_9780385342728 likely legal
Access-restricted-item: true- present in the collection: archive.org/details/internetarchivebooks?tab=about
Inward Bound by Abraham Pais (1988) Updated 2025-07-16
The book unfortunately does not cover the history of quantum mechanics very, the author specifically says that this will not be covered, the focus is more on particles/forces. But there are still some mentions.
Les Atomes by Jean Perrin (1913) Updated 2025-07-16
Subtle is the Lord by Abraham Pais (1982) mentions that this has a good summary of the atomic theory evidence that was present at the time, and which had become basically indisputable at or soon after that date.
On Wikimedia Commons since it is now public domain in most countries: commons.wikimedia.org/w/index.php?title=File:Perrin,_Jean_-_Les_Atomes,_F%C3%A9lix_Alcan,_1913.djvu
An English translation from 1916 by English chemist Dalziel Llewellyn Hammick on the Internet Archive, also on the public domain: archive.org/details/atoms00hammgoog
OurBigBook.com Motivation Updated 2025-07-16
Many subjects have changed very little in the last hundred years, and so it is mind-blowing that people have to pay for books that teach them!
Since Ciro Santilli was young, he has been bewildered by the natural sciences and mathematics due to his bad memory.
The beauty of those subjects has always felt like intense sunlight in a fresh morning to Ciro. Sometimes it gets covered by clouds and obscured by less important things, but it always comes back again and again, weaker or stronger with its warmth, guiding Ciro's life path.
As a result, he has always suffered a lot at school: his grades were good, but he wasn't really learning those beautiful things that he wanted to learn!
First, before university, school organization had only one goal: put you into the best universities, to make a poster out of you and get publicity, so that more parents will be willing to pay them money to put their kids into good university.
Ciro once asked a chemistry teacher some "deeper question" after course was over, related to the superficial vision of the topic they were learning to get grades in university entry exams. The teacher replied something like:Ciro feels that this was one of the greatest compliments he has ever received in his life. This teacher, understood him. Funny how some things stick, while all the rest fades.
You remind me of a friend of mine. He always wanted to understand the deeper reason for things. He now works at NASA.
Another interesting anecdote is how Ciro Santilli's mother recalls that she always found out about exams in the same way: when the phone started ringing as Ciro's friends started asking for help with the subjects just before the exam. Sometimes it was already too hopelessly late, but Ciro almost always tried. Nothing shows how much better you are than someone than teaching them.
Then, after entering university, although things got way better because were are able to learn things that are borderline useful.
Ciro still felt a strong emotion of nostalgia when after university his mother asked if she could throw away his high school books, and Ciro started tearing them all down for recycling. Such is life.
University teachers were still to a large extent researchers who didn't want to, know how to and above all have enough time and institutional freedom to teach things properly and make you see their beauty, some good relate articles:
The very fact that you had very little choice of what to learn so that a large group can get a "Diploma", makes it impossible for people to deeply learn what the really want.
This is especially true because Ciro was in Brazil, a third world country, where the opportunities are comparatively extremely limited to the first world.
Also extremely frustrating is how you might have to wait for years to get to the subject you really want. For example, on a physics course, quantum mechanics is normally only taught on the third year! While there is value to knowing the pre-requisites, holding people back for years is just too sad, and Ciro much prefers backward design. And just like the university entry exams, this creates an entry barrier situation where you might in the end find that "hey, that's not what I wanted to learn after all", see also: students must have a flexible choice of what to learn.
We've created a system where people just wait, and wait, and wait, never really doing what they really want. They wait through school to get into university. They wait through university to get to masters. They wait through masters to get to PhD. They wait through PhD to become a PI. And for the minuscule fraction of those that make it, they become fund proposal writers. And if you make any wrong choice along the, it's all over, you can't continue anymore, the cost would be too great. So you just become software engineer or a consultant. Is this the society that we really want?
And all of this is considering that he was very lucky to not be in a poor family, and was already in some of the best educational institutions locally available already, and had comparatively awesome teachers, without which he wouldn't be where he is today if he hadn't had such advantages in the first place.
But no matter how awesome one teacher is, no single person can overcome a system so large and broken. Without technological innovation that is.
The key problem all along the way is the Society's/Government's belief that everyone has to learn the same things, and that grades in exams mean anything.
Even if you wanted to really learn natural sciences and had the time available, it is just too hard to find good resources to properly learn it. Even attending university courses are hit and miss between amazing and mediocre teachers.
If you go into a large book shop, the science section is tiny, and useless popular science books dominate it without precise experiment descriptions. And then, the only few "serious" books are a huge list of formulas without any experimental motivation.
And if you are lucky to have access to an university library that has open doors, most books are likely to be old and boring as well. Googling for PDFs from university courses is the best bet.
Around 2012 however, he finally saw the light, and started his path to Ciro Santilli's Open Source Enlightenment. University was not needed anymore. He could learn whatever he wanted. A vision was born.
To make things worse, for a long time he was tired of seeing poor people begging on the streets every day and not doing anything about it. He thought:which like everything else is likely derived subconsciously from something else, here Schindler's list possibly adapted quote from the Talmud:
He who teaches one thousand, saves one million.
So, by the time he left University, instead of pursuing a PhD in theoretical Mathematics or Physics just for the beauty of it as he had once considered, he had new plans.
We needed a new educational system. One that would allow people to fulfill their potential and desires, and truly improve society as a result, both in rich and poor countries.
And he found out that programming and applied mathematics could also be fun, so he might as well have some fun while doing this! ;-)
So he started Booktree in 2014, a GitLab fork, worked on it for an year, noticed the approach was dumb, and a few years later started building this new version. The repo github.com/booktree/booktree is a small snapshot of Ciro's 2014 brain on the area, there were quite a few similar projects at the time, and most have died.
Ciro is basically a librarian at heart, and wants to be the next:
- Jimmy Wales
- Brewster Kahle
- Tim Berners Lee
- Tim O'Reilly, who once brilliantly described O'Reilly Media as "a lifestyle business that got out of control" [ref]
- Aaron Swartz. Minus suicide hopefully.
"Jimmy Wales: How a ragtag band created Wikipedia" 2005 TED talk
. Source. Original source: www.ted.com/talks/jimmy_wales_the_birth_of_wikipedia. QED and the men who made it: Dyson, Feynman, Schwinger, and Tomonaga by Silvan Schweber (1994) Updated 2025-07-16
Available for free online rent on the Internet Archive: archive.org/details/qedmenwhomadeitd0000schw
Quantization as an Eigenvalue Problem Updated 2025-07-16
This paper appears to calculate the Schrödinger equation solution for the hydrogen atom.
TODO is this the original paper on the Schrödinger equation?
Published on Annalen der Physik in 1926.
Open access in German at: onlinelibrary.wiley.com/doi/10.1002/andp.19263840404 which gives volume 384, Issue 4, Pages 361-376. Kudos to Wiley for that. E.g. Nature did not have similar policies as of 2023.
This paper may have fallen into the public domain in the US in 2022! On the Internet Archive we can see scans of the journal that contains it at: ia903403.us.archive.org/29/items/sim_annalen-der-physik_1926_79_contents/sim_annalen-der-physik_1926_79_contents.pdf. Ciro Santilli extracted just the paper to: commons.wikimedia.org/w/index.php?title=File%3AQuantisierung_als_Eigenwertproblem.pdf. It is not as well processed as the Wiley one, but it is of 100% guaranteed clean public domain provenance! TODO: hmmm, it may be public domain in the USA but not Germany, where 70 years after author deaths rules, and Schrodinger died in 1961, so it may be up to 2031 in that country... messy stuff. There's also the question of wether copyright is was tranferred to AdP at publication or not.
Robert Noyce: The Man Behind the Microchip by Leslie Berlin (2006) Updated 2025-07-16
Borrow from the Internet Archive for free: archive.org/details/manbehindmicroc000berl/page/n445/mode/2up
The Supermen: The Story of Seymour Cray by Charles J. Murray (1997) Updated 2025-07-16
Initial chapters put good clarity on the formation of the military-industrial complex. Being backed by the military, especially just after World War II, was in itself enough credibility to start and foster a company.
Amazing how Control Data Corporation raised capital IPO style as a startup without a product. The dude was selling shares at dinner parties in his home.
Very interesting mention on page 70 of how Israel bought CDC's UNIVAC 1103 which Cray contributed greatly to design, and everyone knew that it was to make thermonuclear weapons, since that was what the big American labs like this mention should be added to: en.wikipedia.org/wiki/Nuclear_weapons_and_Israel but that's Extended Protected... the horrors of Wikipedia.
Another interesting insight is how "unintegrated" computers were back then. They were literally building computers out of individual vacuum tubes, then individual semiconducting transistors, a gate at a time. Then things got more and more integrated as time went. That is why the now outdated word "microprocessor" existed. When processors start to fit into a single integrated circuit, they were truly micro compared to the monstrosities that existed previously.
Also, because integration was so weak initially, it was important to more manually consider the length of wire signals had to travel, and try to put components closer together to reduce the critical path to be able to increase clock speeds. These constraints are also of course present in modern computer design, but they were just so much more visible in those days.
The book does unfortunately not give much detail in Crays personal life as mentioned on this book review: www.goodreads.com/review/show/1277733185?book_show_action=true. His childhood section is brief, and his wedding is described in one paragraph, and divorce in one sentence. Part of this is because he was very private about his family most likely note how Wikipedia had missed his first wedding, and likely misattribute children to the second wedding; en.wikipedia.org/wiki/Talk:Seymour_Cray section "Weddings and Children".
Crays work philosophy is is highlighted many times in the book, and it is something worthy to have in mind:
Cray's final downfall was when he opted to try to use a promising but hard to work with material gallium arsenide instead of silicon as his way to try and speed up computers, see also: gallium arsenide vs silicon. Also, he went against the extremely current of the late 80's early 90's pointing rather towards using massively parallel systems based on silicon off-the-shelf Intel processors, a current that had DARPA support, and which by far the path that won very dramatically as of 2020, see: Intel supercomputer market share.