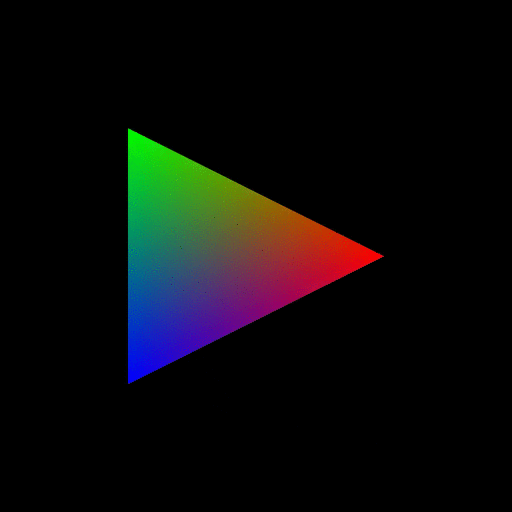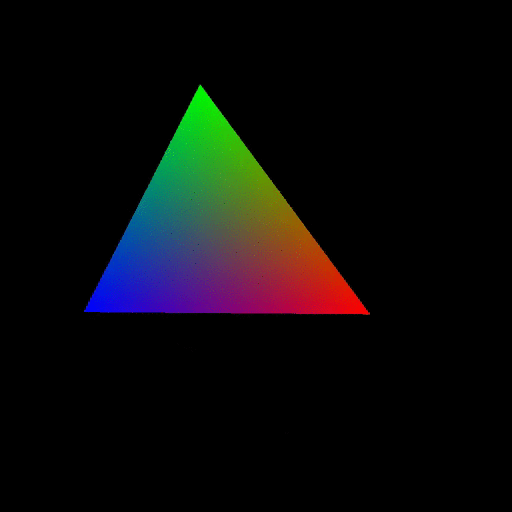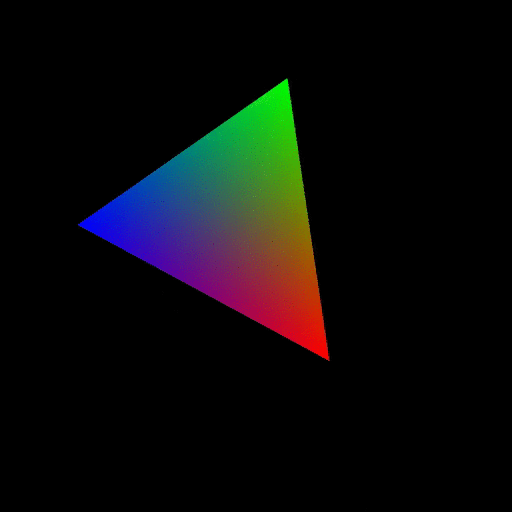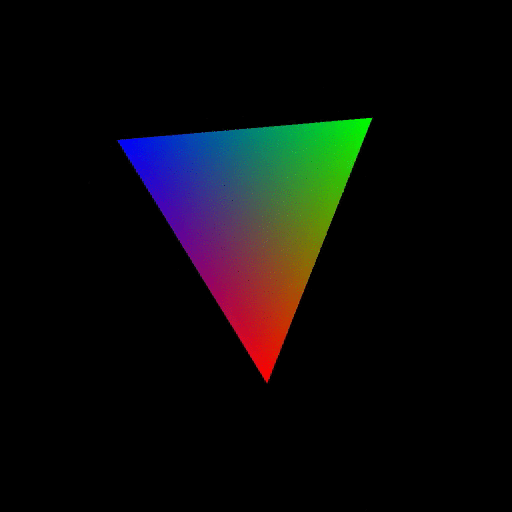The best articles by Ciro Santilli Updated 2025-07-16
These are the best articles ever authored by Ciro Santilli, most of them in the format of Stack Overflow answers.
Ciro posts update about new articles on his Twitter accounts.
Some random generally less technical in-tree essays will be present at: Section "Essays by Ciro Santilli".
- Trended on Hacker News:
- CIA 2010 covert communication websites on 2023-06-11. 190 points, a mild success.
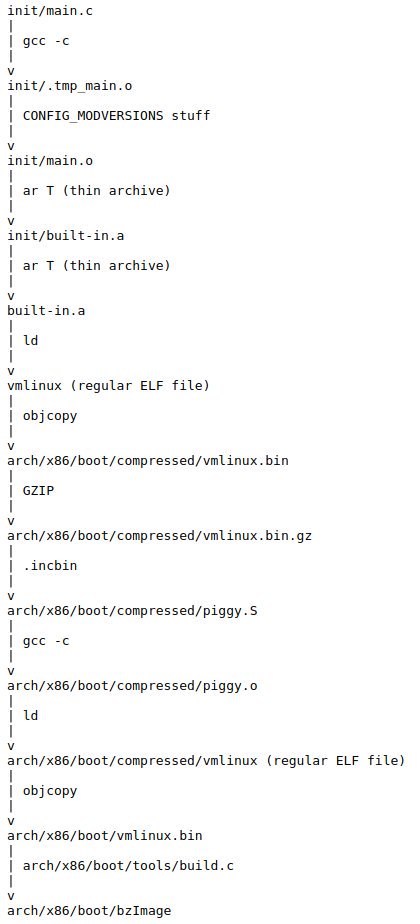
- x86 Bare Metal Examples on 2019-03-19. 513 points. The third time something related to that repo trends. Hacker news people really like that repo!
- again 2020-06-27 (archive). 200 points, repository traffic jumped from 25 daily unique visitors to 4.6k unique visitors on the day
- How to run a program without an operating system? on 2018-11-26 (archive). 394 points. Covers x86 and ARM
- ELF Hello World Tutorial on 2017-05-17 (archive). 334 points.
- x86 Paging Tutorial on 2017-03-02. Number 1 Google search result for "x86 Paging" in 2017-08. 142 points.
- x86 assembly
- What does "multicore" assembly language look like?
- What is the function of the push / pop instructions used on registers in x86 assembly? Going down to memory spills, register allocation and graph coloring.
- Linux kernel
- What do the flags in /proc/cpuinfo mean?
- How does kernel get an executable binary file running under linux?
- How to debug the Linux kernel with GDB and QEMU?
- Can the sys_execve() system call in the Linux kernel receive both absolute or relative paths?
- What is the difference between the kernel space and the user space?
- Is there any API for determining the physical address from virtual address in Linux?
- Why do people write the
#!/usr/bin/envpython shebang on the first line of a Python script? - How to solve "Kernel Panic - not syncing: VFS: Unable to mount root fs on unknown-block(0,0)"?
- Single program Linux distro
- QEMU
- gcc and Binutils:
- How do linkers and address relocation works?
- What is incremental linking or partial linking?
- GOLD (
-fuse-ld=gold) linker vs the traditional GNU ld and LLVM ldd - What is the -fPIE option for position-independent executables in GCC and ld? Concrete examples by running program through GDB twice, and an assembly hello world with absolute vs PC relative load.
- How many GCC optimization levels are there?
- Why does GCC create a shared object instead of an executable binary according to file?
- C/C++: almost all of those fall into "disassemble all the things" category. Ciro also does "standards dissection" and "a new version of the standard is out" answers, but those are boring:
- What does "static" mean in a C program?
- In C++ source, what is the effect of
extern "C"? - Char array vs Char Pointer in C
- How to compile glibc from source and use it?
- When should
static_cast,dynamic_cast,const_castandreinterpret_castbe used? - What exactly is
std::atomicin C++?. This answer was originally more appropriately entitled "Let's disassemble some stuff", and got three downvotes, so Ciro changed it to a more professional title, and it started getting upvotes. People judge books by their covers. notmain.o 0000000000000000 0000000000000017 W MyTemplate<int>::f(int) main.o 0000000000000000 0000000000000017 W MyTemplate<int>::f(int)Code 1.. From: What is explicit template instantiation in C++ and when to use it?nmoutputs showing that objects are redefined multiple times across files if you don't use template instantiation properly
- IEEE 754
- What is difference between quiet NaN and signaling NaN?
- In Java, what does NaN mean?
Without subnormals: +---+---+-------+---------------+-------------------------------+ exponent | ? | 0 | 1 | 2 | 3 | +---+---+-------+---------------+-------------------------------+ | | | | | | v v v v v v ----------------------------------------------------------------- floats * **** * * * * * * * * * * * * ----------------------------------------------------------------- ^ ^ ^ ^ ^ ^ | | | | | | 0 | 2^-126 2^-125 2^-124 2^-123 | 2^-127 With subnormals: +-------+-------+---------------+-------------------------------+ exponent | 0 | 1 | 2 | 3 | +-------+-------+---------------+-------------------------------+ | | | | | v v v v v ----------------------------------------------------------------- floats * * * * * * * * * * * * * * * * * ----------------------------------------------------------------- ^ ^ ^ ^ ^ ^ | | | | | | 0 | 2^-126 2^-125 2^-124 2^-123 | 2^-127Code 2.Visualization of subnormal floating point numbers vs what IEEE 754 would look like without them. From: What is a subnormal floating point number?
- Computer science
- Algorithms
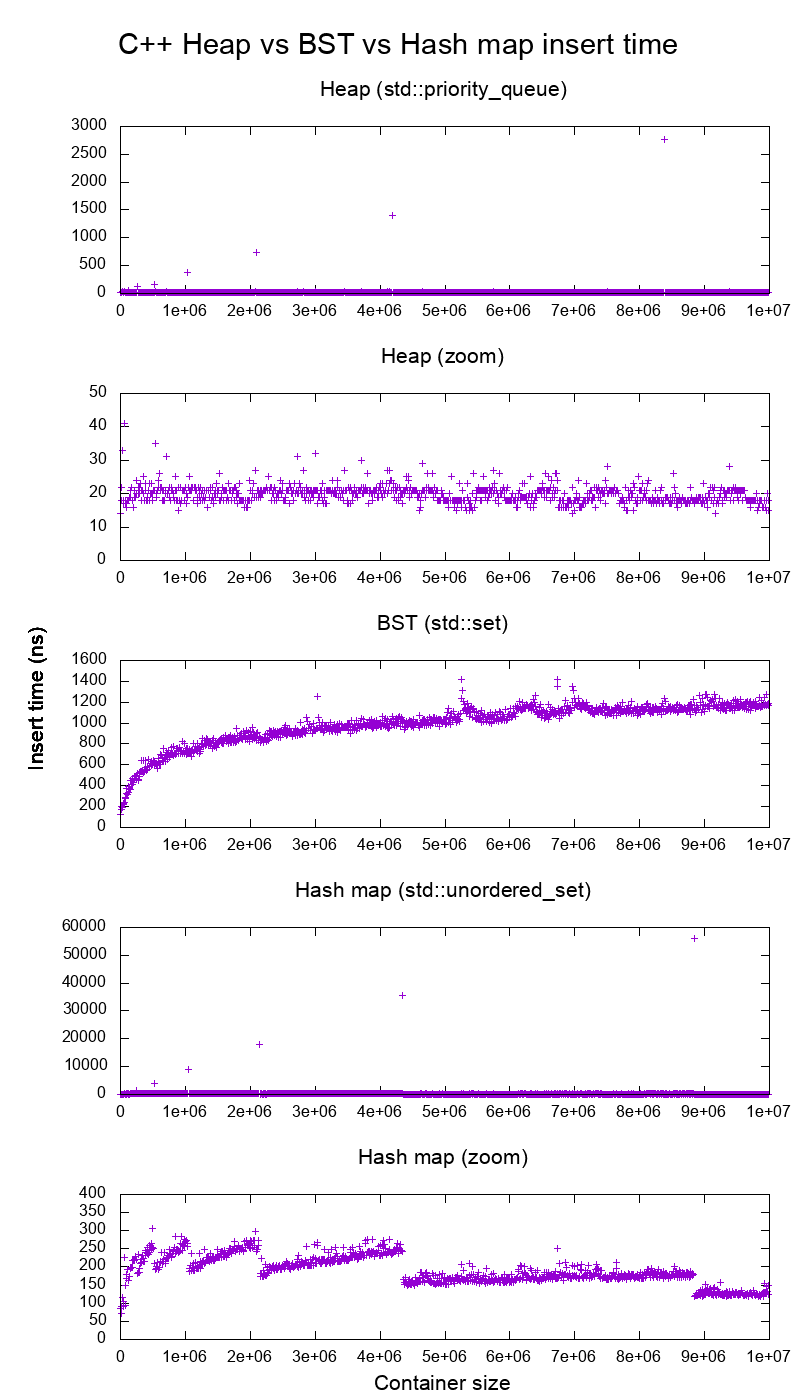
Figure 5. Average insertion time into heaps, binary search tree and hash maps of the C++ standard library. Source. From: Heap vs Binary Search Tree (BST)
- Is it necessary for NP problems to be decision problems?
- Polynomial time and exponential time. Answered focusing on the definition of "exponential time".
- What is the smallest Turing machine where it is unknown if it halts or not?. Answer focusing on "blank tape" initial condition only. Large parts of it are summarizing the Busy Beaver Challenge, but some additions were made.
- Algorithms
- Git
| 0 | 4 | 8 | C | |-------------|--------------|-------------|----------------| 0 | DIRC | Version | File count | ctime ...| 0 | ... | mtime | device | 2 | inode | mode | UID | GID | 2 | File size | Entry SHA-1 ...| 4 | ... | Flags | Index SHA-1 ...| 4 | ... |Code 3.ASCII art depicting the binary file format of the Git index file. From: What does the git index contain EXACTLY?tree {tree_sha} {parents} author {author_name} <{author_email}> {author_date_seconds} {author_date_timezone} committer {committer_name} <{committer_email}> {committer_date_seconds} {committer_date_timezone} {commit message}Code 4.Description of the Git commit object binary data structure. From: What is the file format of a git commit object data structure?- How do I clone a subdirectory only of a Git repository?
- Python
- Web technology
- OpenGL
Figure 7. OpenGL rendering output dumped to a GIF file. Source. From: How to use GLUT/OpenGL to render to a file?- What are shaders in OpenGL?
- Why do we use 4x4 matrices to transform things in 3D?
Figure 10. Sinusoidal circular wave heatmap generated with an OpenGL shader at 60 FPS on SDL. Source.
- Node.js
- Ruby on Rails
- POSIX
- What is POSIX? Huge classified overview of the most important things that POSIX specifies.
- Systems programming
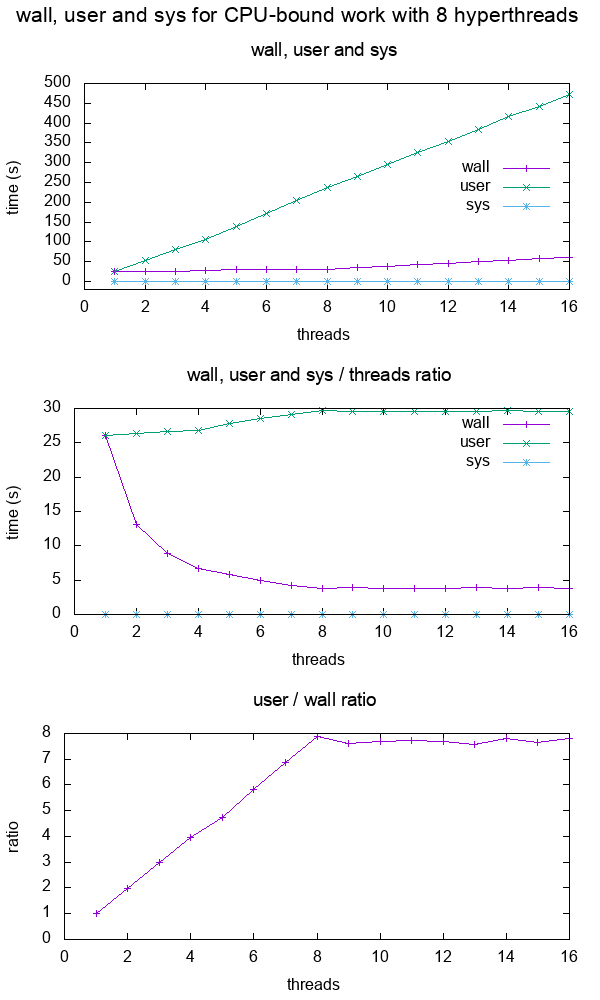
- What do the terms "CPU bound" and "I/O bound" mean?
Figure 12. Plot of "real", "user" and "sys" mean times of the output of time for CPU-bound workload with 8 threads. Source. From: What do 'real', 'user' and 'sys' mean in the output of time?+--------+ +------------+ +------+ | device |>---------------->| function 0 |>----->| BAR0 | | | | | +------+ | |>------------+ | | | | | | | +------+ ... ... | | |>----->| BAR1 | | | | | | +------+ | |>--------+ | | | +--------+ | | ... ... ... | | | | | | | | +------+ | | | |>----->| BAR5 | | | +------------+ +------+ | | | | | | +------------+ +------+ | +--->| function 1 |>----->| BAR0 | | | | +------+ | | | | | | +------+ | | |>----->| BAR1 | | | | +------+ | | | | ... ... ... | | | | | | +------+ | | |>----->| BAR5 | | +------------+ +------+ | | | ... | | | +------------+ +------+ +------->| function 7 |>----->| BAR0 | | | +------+ | | | | +------+ | |>----->| BAR1 | | | +------+ | | ... ... ... | | | | +------+ | |>----->| BAR5 | +------------+ +------+Code 5.Logical struture PCIe device, functions and BARs. From: What is the Base Address Register (BAR) in PCIe?
- Electronics
- Raspberry Pi
Figure 13. Raspberry Pi 2 directly connected to a laptop with an Ethernet cable. Image from answer to: How to hook up a Raspberry Pi via Ethernet to a laptop without a router?Figure 14. . Image from answer to: How to hook up a Raspberry Pi via Ethernet to a laptop without a router? Figure 15. . Image from answer to: How to emulate the Raspberry Pi 2 on QEMU? Figure 16. Bare metal LED blinker program running on a Raspberry Pi 2. Image from answer to: How to run a C program with no OS on the Raspberry Pi?
- Raspberry Pi
- Computer security
- Media
Video 2. Canon in D in C. Source.The original question was deleted, lol...: How to programmatically synthesize music?- How to resize a picture using ffmpeg's sws_scale()?
- Is there any decent speech recognition software for Linux? ran a few examples manually on
vosk-apiand compared to ground truth.
- Eclipse
- Computer hardware
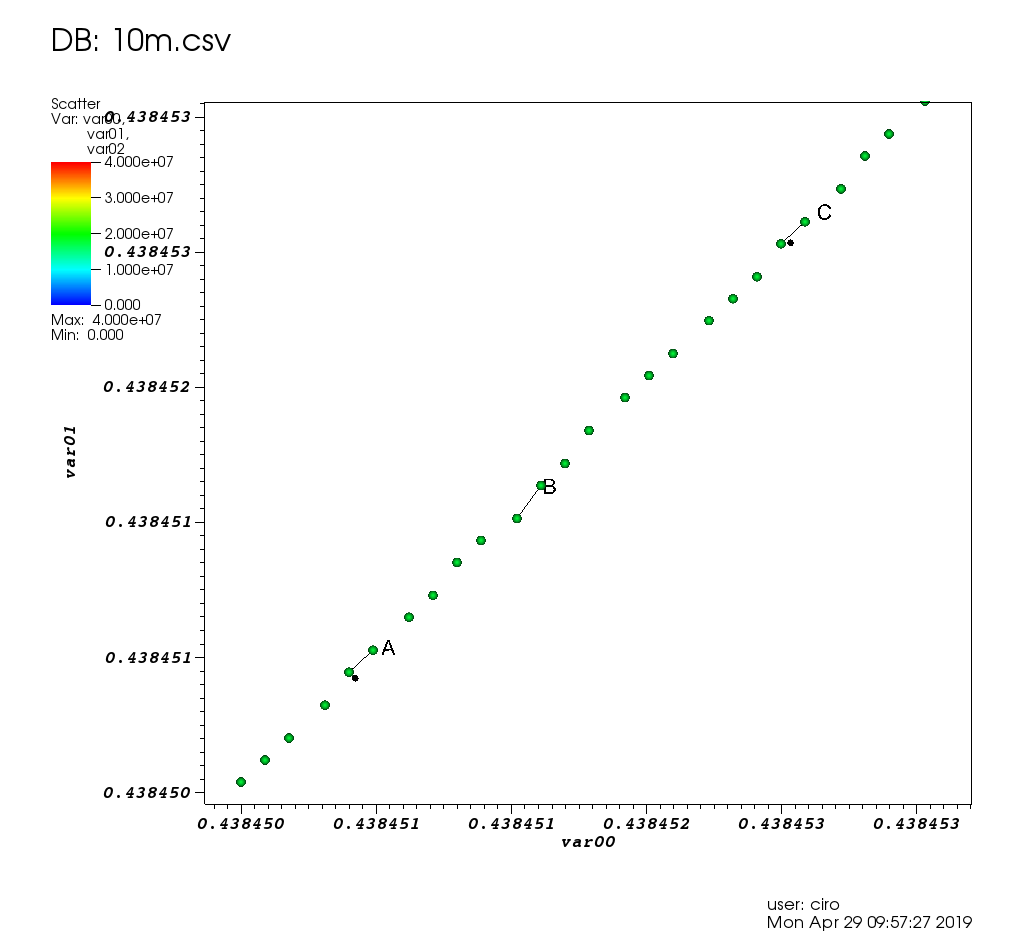
- Scientific visualization software
Figure 17. VisIt zoom in 10 million straight line plot with some manually marked points. Source. From: Section "Survey of open source interactive plotting software with a 10 million point scatter plot benchmark by Ciro Santilli"
- Numerical analysis
- Computational physics
- Register transfer level languages like Verilog and VHDL
- Verilog:
Figure 19. . See also: Section "Verilator interactive example"
- Verilog:
- Android
Video 4. Android screen showing live on an Ubuntu laptop through ADB. Source. From: How to see the Android screen live on an Ubuntu desktop through ADB?
- Debugging
- Program optimization
- What is tail call optimization?
Figure 21. . Source. The answer compares gprof, valgrind callgrind, perf and gperftools on a single simple executable.
- Data
Figure 22. Mathematics dump of Wikipedia CatTree. Source. In this project, Ciro Santilli explored extracting the category and article tree out of the Wikipedia dumps.
- Mathematics
Figure 23. Diagram of the fundamental theorem on homomorphisms by Ciro Santilli (2020)Shows the relationship between group homomorphisms and normal subgroups.- Section "Formalization of mathematics": some early thoughts that could be expanded. Ciro almost had a stroke when he understood this stuff in his teens.
Figure 24. Simple example of the Discrete Fourier transform. Source. That was missing from Wikipedia page: en.wikipedia.org/wiki/Discrete_Fourier_transform!
- Network programming
- Physics
- What is the difference between plutonium and uranium?
Figure 25. Spacetime diagram illustrating how faster-than-light travel implies time travel. From: Does faster than light travel imply travelling back in time?
- Biology
Figure 26. Top view of an open Oxford Nanopore MinION. Source. From: Section "How to use an Oxford Nanopore MinION to extract DNA from river water and determine which bacteria live in it"Figure 27. Mass fractions in a minimal growth medium vs an amino acid cut in a simulation of the E. Coli Whole Cell Model by Covert Lab. Source. From: Section "E. Coli Whole Cell Model by Covert Lab"
- Quantum computing
- Section "Quantum computing is just matrix multiplication"
Figure 28. Visualization of the continuous deformation of states as we walk around the Bloch sphere represented as photon polarization arrows. From: Understanding the Bloch sphere.
- Bitcoin
- GIMP
Figure 29. GIMP screenshot part of how to combine two images side-by-side in GIMP?
- Home DIY
Figure 30. Total_Blackout_Cassette_Roller_Blind_With_Curtains.Source. From: Section "How to blackout your window without drilling"
- China
Hide top bar on Ubuntu Updated 2025-07-16
Or likely more generally, on GNOME desktop, which is the default desktop environment as of Ubuntu 22.10.
Silk Road (marketplace) Updated 2025-11-05
Ciro Santilli has become slightly obsessed with this story, and the main mastermind Ross Ulbricht.
The best article available so far is: www.theregister.co.uk/2019/01/29/how_i_caught_silk_road_mastermind (archive) which summarizes what one of the investigators said in a 2019 French computer security conference.
The key living posts are:
- stackoverflow.com/questions/15445285/how-can-i-connect-to-a-tor-hidden-service-using-curl-in-php (archive) which was originally asked under the real name, and then the username was changed to "Frosty", which matches one of the server's logins after the laptop was captured
- altoid early Silk Road mention: bitcointalk.org/?topic=175.70;wap2 (archive)
The big question is of course how libertarian free market ideologically motivated the website was, and how purely criminal greed it was.
The magnitude of the early operational security mistakes does make Ciro think that Ross did it "because he could" and "for the lolz" in a real world Breaking Bad way.
The entry in Ross' diary does resonate a lot with Ciro and any entrepreneur, full diary at: www.wired.com/2015/01/heres-secret-silk-road-journal-laptop-ross-ulbricht/ (archive).
[i]n 2011," [I believe I will be] "creating a year of prosperity and power beyond what I have ever experienced before,Silk Road is going to become a phenomenon and at least one person will tell me about it, unknowing that I was its creator."
Having this kind of feeling, is the greatest thing any human can have, and what motivates all great things.
Capitalizing in illegal things though is a cheat, big things take longer than a few years to reach, but reaching them is that much more satisfying as well.
Other interesting quotes:which Ciro also feels, see don't be a pussy, and:
Everyone knows I am working on a bitcoin exchange. I always thought honesty was the best policy and now I didn't know what to do. I should have just told everyone I am a freelance programmer or something, but I had to tell half truths. It felt wrong to lie completely so I tried to tell the truth without revealing the bad part, but now I am in a jam. Everyone knows too much. Dammit.
Also very worth reading is the San Francisco flat mate account: www.vice.com/en_us/article/ae3q8g/my-roommate-the-darknet-drug-lord (archive).
The murder for hire allegations are also interesting: mashable.com/2013/10/03/silk-road-hits, he paid 80k dollars to undercover DEA agents!
Except for the fact that Ross was an 80 million Dollar drug lord, those accounts sound exactly like what you would expect from any other nerdy startup founder! The:
- "just do it" strategy effectively going to a minimal viable product (manual transaction management!), while making many mistakes along the way, including hiring mistakes and successes when scaling is needed
- the hardship of self bootstrapping your own social network (here with some kilos of mushrooms)
- the variety of periods, from relatively calm, to hair pulling stress during big changes
It is also amusing to see very concretely the obvious fact that the FBI can get a subpoena for all accounts you ever had, e.g. they knew his laptop model from Amazon and brought a corresponding power cable to the arrest! If you are going to be a cyber criminal, don't use your real name, ever!
Should justice be blind? Maybe. But it does hurt for mere non-blind men to see it sometimes. Especially when drug liberalization is involved.
Symmetric encryption Created 2024-10-12 Updated 2025-07-16
Symmetric encryption is a type of encryption where you use a password (also known as a "key") to encrypt your data, and then the same password to decrypt the data.
For example, this is the type of encryption that is used for encrypting the data in our smartphones and laptops with disk encryption.
This way, if your laptop gets stolen, the thief is not able to see your private photos without knowing your password, even though they are able to read every byte of your disk.
The downside is that that you have to type your password every time you want to login. This leads people to want to use shorter passwords, which in turn are more prone to password cracking.
The other main type of encryption is public-key cryptography.
The advantage of public-key cryptography is that it allows you to send secret messages to other people even an the attacker is able to capture the encrypted messages. This is for example what you want to do when sending a personal message to a friend over the Internet. Such encryption is especially crucial when using wireless communication such as Wi-Fi, where anyone nearby can capture the signals you send and receive, and would be able to read all your data if it weren't encrypted.
Easily sending encrypted messages over the Internet is not possible with symmetric encryption because for your friend to decrypt the message in that system, you'd need to send them the password, which the attacker would also be able to eavesdrop and then decrypt the message that follows using it. The problem of sharing a password with another person online is called key exchange.
Advanced Encryption Standard (AES) is one of the most popular families of symmetric encryption algorithms.
OpenSSL is a popular open source implementation of symmetric and public-key cryptography. A simple example of using OpenSSL for symmetric encryption from the command-line is:This asks for a password, which we set as contains:Then to decrypt:once again asks for your password and given the correct password produces a file This was tested on Ubuntu 24.04, OpenSSL 3.0.13. See also: How to use OpenSSL to encrypt/decrypt files? on Stack Overflow.
echo 'Hello World!' > message.txt
openssl aes-256-cbc -a -salt -pbkdf2 -in message.txt -out message.txt.encasdfqwer, and then produces a file message.txt.enc containing garbled text such that:hd message.txt.enc00000000 55 32 46 73 64 47 56 6b 58 31 38 58 48 65 2f 30 |U2FsdGVkX18XHe/0|
00000010 70 56 42 2b 70 45 6c 55 59 38 2b 54 38 7a 4e 34 |pVB+pElUY8+T8zN4|
00000020 4e 37 6d 52 2f 73 6d 4d 62 64 30 3d 0a |N7mR/smMbd0=.|
0000002dopenssl aes-256-cbc -d -a -pbkdf2 -in message.txt.enc -out message.new.txtmessage.new.txt containing the original message:Hello World!There is no provably secure symmetric-key algorithm besides the one-time pad, which has the serious drawback of requiring the key to be as long as the message. This means that we believe that most encryption algorithms are secure because it is a hugely valuable target and no one has managed to crack them yet. But we don't have a mathematical proof that they are actually secure, so they could in theory be broken by new algorithms one day.