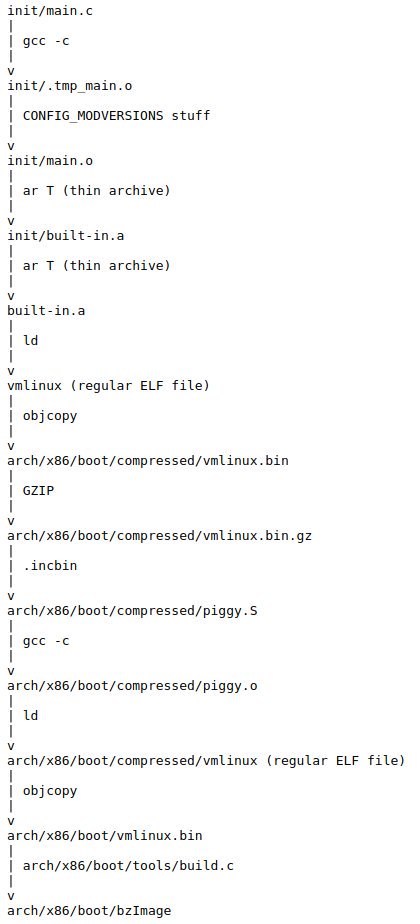
The best articles by Ciro Santilli Updated 2025-07-16
These are the best articles ever authored by Ciro Santilli, most of them in the format of Stack Overflow answers.
Ciro posts update about new articles on his Twitter accounts.
Some random generally less technical in-tree essays will be present at: Section "Essays by Ciro Santilli".
- Trended on Hacker News:
- CIA 2010 covert communication websites on 2023-06-11. 190 points, a mild success.
- x86 Bare Metal Examples on 2019-03-19. 513 points. The third time something related to that repo trends. Hacker news people really like that repo!
- again 2020-06-27 (archive). 200 points, repository traffic jumped from 25 daily unique visitors to 4.6k unique visitors on the day
- How to run a program without an operating system? on 2018-11-26 (archive). 394 points. Covers x86 and ARM
- ELF Hello World Tutorial on 2017-05-17 (archive). 334 points.
- x86 Paging Tutorial on 2017-03-02. Number 1 Google search result for "x86 Paging" in 2017-08. 142 points.
- x86 assembly
- What does "multicore" assembly language look like?
- What is the function of the push / pop instructions used on registers in x86 assembly? Going down to memory spills, register allocation and graph coloring.
- Linux kernel
- What do the flags in /proc/cpuinfo mean?
- How does kernel get an executable binary file running under linux?
- How to debug the Linux kernel with GDB and QEMU?
- Can the sys_execve() system call in the Linux kernel receive both absolute or relative paths?
- What is the difference between the kernel space and the user space?
- Is there any API for determining the physical address from virtual address in Linux?
- Why do people write the
#!/usr/bin/envpython shebang on the first line of a Python script? - How to solve "Kernel Panic - not syncing: VFS: Unable to mount root fs on unknown-block(0,0)"?
- Single program Linux distro
- QEMU
- gcc and Binutils:
- How do linkers and address relocation works?
- What is incremental linking or partial linking?
- GOLD (
-fuse-ld=gold) linker vs the traditional GNU ld and LLVM ldd - What is the -fPIE option for position-independent executables in GCC and ld? Concrete examples by running program through GDB twice, and an assembly hello world with absolute vs PC relative load.
- How many GCC optimization levels are there?
- Why does GCC create a shared object instead of an executable binary according to file?
- C/C++: almost all of those fall into "disassemble all the things" category. Ciro also does "standards dissection" and "a new version of the standard is out" answers, but those are boring:
- What does "static" mean in a C program?
- In C++ source, what is the effect of
extern "C"? - Char array vs Char Pointer in C
- How to compile glibc from source and use it?
- When should
static_cast,dynamic_cast,const_castandreinterpret_castbe used? - What exactly is
std::atomicin C++?. This answer was originally more appropriately entitled "Let's disassemble some stuff", and got three downvotes, so Ciro changed it to a more professional title, and it started getting upvotes. People judge books by their covers. notmain.o 0000000000000000 0000000000000017 W MyTemplate<int>::f(int) main.o 0000000000000000 0000000000000017 W MyTemplate<int>::f(int)Code 1.. From: What is explicit template instantiation in C++ and when to use it?nmoutputs showing that objects are redefined multiple times across files if you don't use template instantiation properly
- IEEE 754
- What is difference between quiet NaN and signaling NaN?
- In Java, what does NaN mean?
Without subnormals: +---+---+-------+---------------+-------------------------------+ exponent | ? | 0 | 1 | 2 | 3 | +---+---+-------+---------------+-------------------------------+ | | | | | | v v v v v v ----------------------------------------------------------------- floats * **** * * * * * * * * * * * * ----------------------------------------------------------------- ^ ^ ^ ^ ^ ^ | | | | | | 0 | 2^-126 2^-125 2^-124 2^-123 | 2^-127 With subnormals: +-------+-------+---------------+-------------------------------+ exponent | 0 | 1 | 2 | 3 | +-------+-------+---------------+-------------------------------+ | | | | | v v v v v ----------------------------------------------------------------- floats * * * * * * * * * * * * * * * * * ----------------------------------------------------------------- ^ ^ ^ ^ ^ ^ | | | | | | 0 | 2^-126 2^-125 2^-124 2^-123 | 2^-127Code 2.Visualization of subnormal floating point numbers vs what IEEE 754 would look like without them. From: What is a subnormal floating point number?
- Computer science
- Algorithms
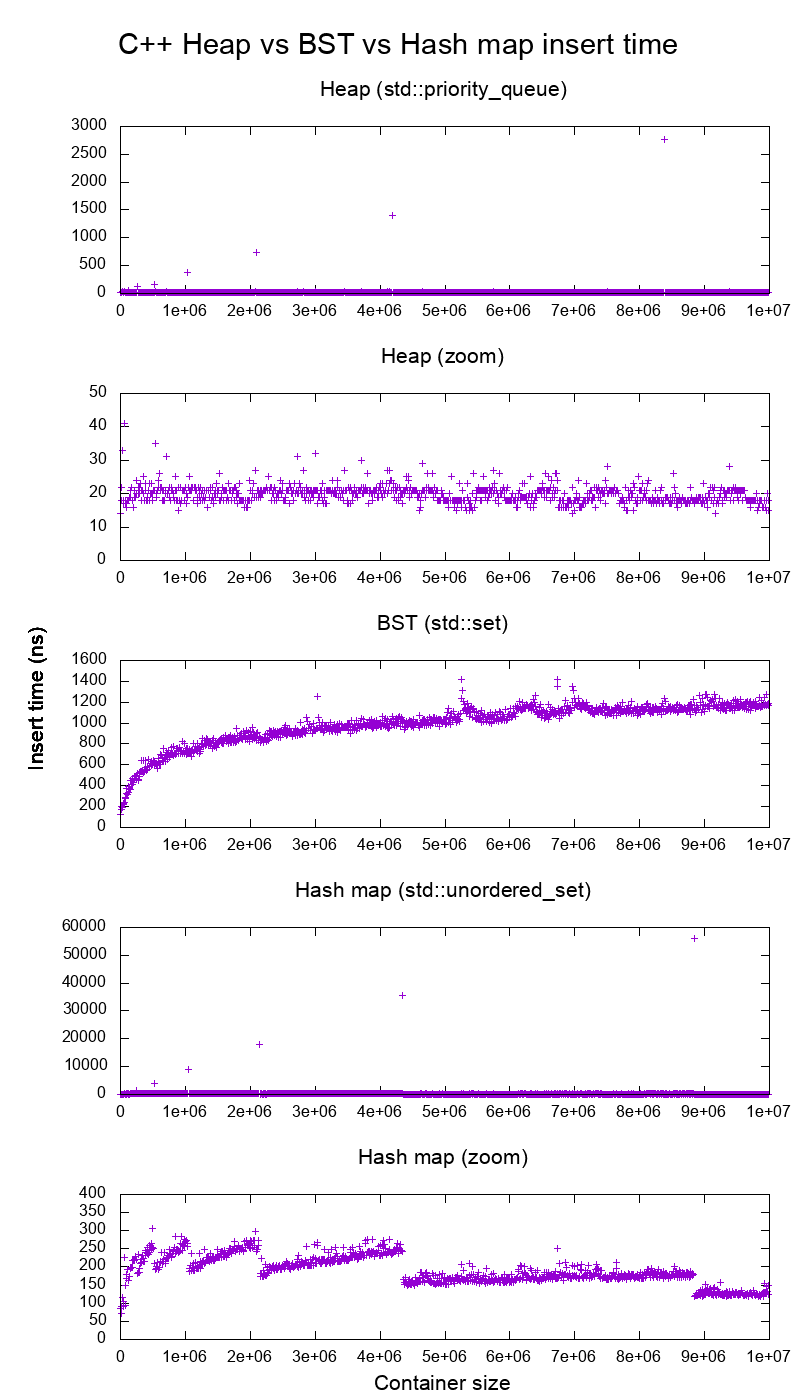
Figure 5. Average insertion time into heaps, binary search tree and hash maps of the C++ standard library. Source. From: Heap vs Binary Search Tree (BST)
- Is it necessary for NP problems to be decision problems?
- Polynomial time and exponential time. Answered focusing on the definition of "exponential time".
- What is the smallest Turing machine where it is unknown if it halts or not?. Answer focusing on "blank tape" initial condition only. Large parts of it are summarizing the Busy Beaver Challenge, but some additions were made.
- Algorithms
- Git
| 0 | 4 | 8 | C | |-------------|--------------|-------------|----------------| 0 | DIRC | Version | File count | ctime ...| 0 | ... | mtime | device | 2 | inode | mode | UID | GID | 2 | File size | Entry SHA-1 ...| 4 | ... | Flags | Index SHA-1 ...| 4 | ... |Code 3.ASCII art depicting the binary file format of the Git index file. From: What does the git index contain EXACTLY?tree {tree_sha} {parents} author {author_name} <{author_email}> {author_date_seconds} {author_date_timezone} committer {committer_name} <{committer_email}> {committer_date_seconds} {committer_date_timezone} {commit message}Code 4.Description of the Git commit object binary data structure. From: What is the file format of a git commit object data structure?- How do I clone a subdirectory only of a Git repository?
- Python
- Web technology
- OpenGL
Figure 7. OpenGL rendering output dumped to a GIF file. Source. From: How to use GLUT/OpenGL to render to a file?- What are shaders in OpenGL?
- Why do we use 4x4 matrices to transform things in 3D?
Figure 10. Sinusoidal circular wave heatmap generated with an OpenGL shader at 60 FPS on SDL. Source.
- Node.js
- Ruby on Rails
- POSIX
- What is POSIX? Huge classified overview of the most important things that POSIX specifies.
- Systems programming
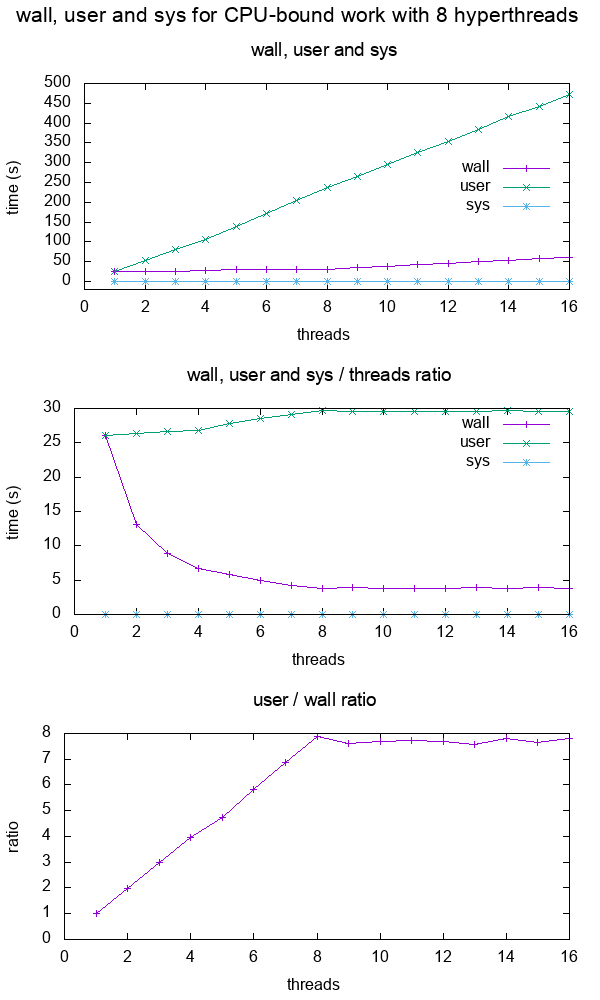
- What do the terms "CPU bound" and "I/O bound" mean?
Figure 12. Plot of "real", "user" and "sys" mean times of the output of time for CPU-bound workload with 8 threads. Source. From: What do 'real', 'user' and 'sys' mean in the output of time?+--------+ +------------+ +------+ | device |>---------------->| function 0 |>----->| BAR0 | | | | | +------+ | |>------------+ | | | | | | | +------+ ... ... | | |>----->| BAR1 | | | | | | +------+ | |>--------+ | | | +--------+ | | ... ... ... | | | | | | | | +------+ | | | |>----->| BAR5 | | | +------------+ +------+ | | | | | | +------------+ +------+ | +--->| function 1 |>----->| BAR0 | | | | +------+ | | | | | | +------+ | | |>----->| BAR1 | | | | +------+ | | | | ... ... ... | | | | | | +------+ | | |>----->| BAR5 | | +------------+ +------+ | | | ... | | | +------------+ +------+ +------->| function 7 |>----->| BAR0 | | | +------+ | | | | +------+ | |>----->| BAR1 | | | +------+ | | ... ... ... | | | | +------+ | |>----->| BAR5 | +------------+ +------+Code 5.Logical struture PCIe device, functions and BARs. From: What is the Base Address Register (BAR) in PCIe?
- Electronics
- Raspberry Pi
Figure 13. Raspberry Pi 2 directly connected to a laptop with an Ethernet cable. Image from answer to: How to hook up a Raspberry Pi via Ethernet to a laptop without a router?Figure 14. . Image from answer to: How to hook up a Raspberry Pi via Ethernet to a laptop without a router? Figure 15. . Image from answer to: How to emulate the Raspberry Pi 2 on QEMU? Figure 16. Bare metal LED blinker program running on a Raspberry Pi 2. Image from answer to: How to run a C program with no OS on the Raspberry Pi?
- Raspberry Pi
- Computer security
- Media
Video 2. Canon in D in C. Source.The original question was deleted, lol...: How to programmatically synthesize music?- How to resize a picture using ffmpeg's sws_scale()?
- Is there any decent speech recognition software for Linux? ran a few examples manually on
vosk-apiand compared to ground truth.
- Eclipse
- Computer hardware
- Scientific visualization software
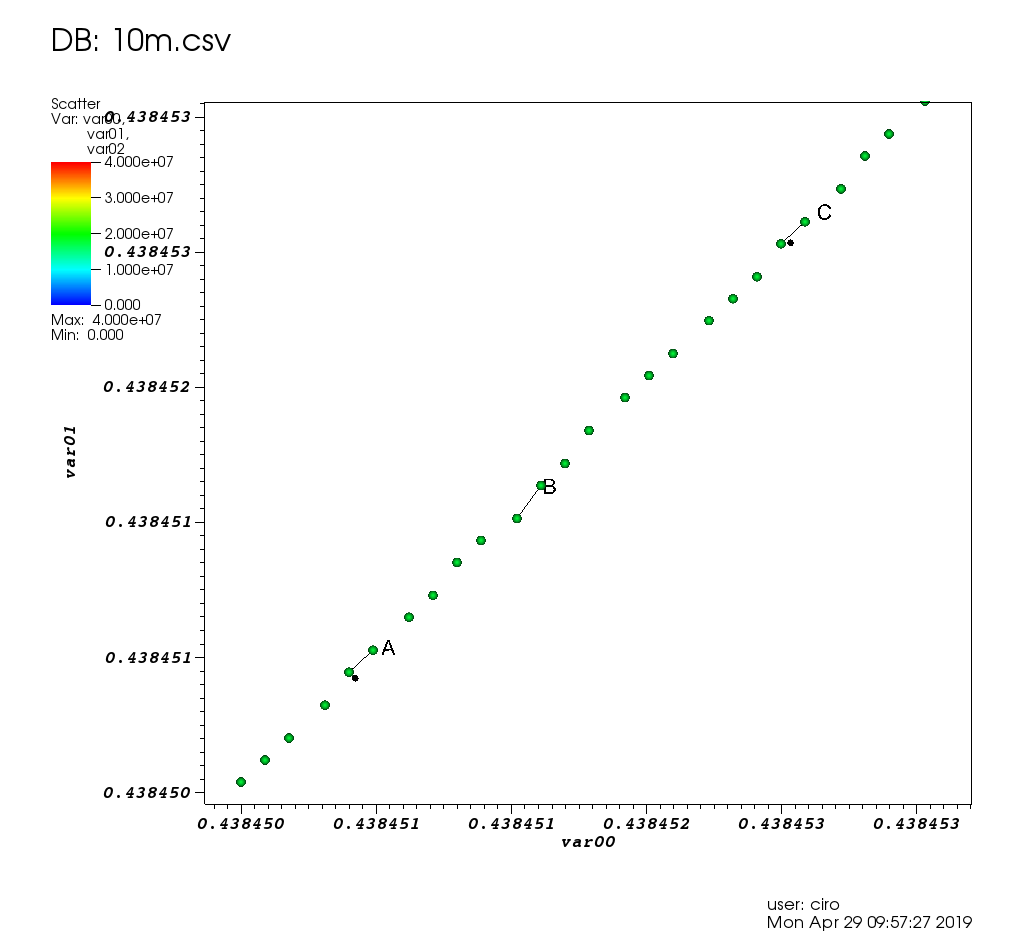
Figure 17. VisIt zoom in 10 million straight line plot with some manually marked points. Source. From: Section "Survey of open source interactive plotting software with a 10 million point scatter plot benchmark by Ciro Santilli"
- Numerical analysis
- Computational physics
- Register transfer level languages like Verilog and VHDL
- Verilog:
Figure 19. . See also: Section "Verilator interactive example"
- Verilog:
- Android
Video 4. Android screen showing live on an Ubuntu laptop through ADB. Source. From: How to see the Android screen live on an Ubuntu desktop through ADB?
- Debugging
- Program optimization
- What is tail call optimization?
Figure 21. . Source. The answer compares gprof, valgrind callgrind, perf and gperftools on a single simple executable.
- Data
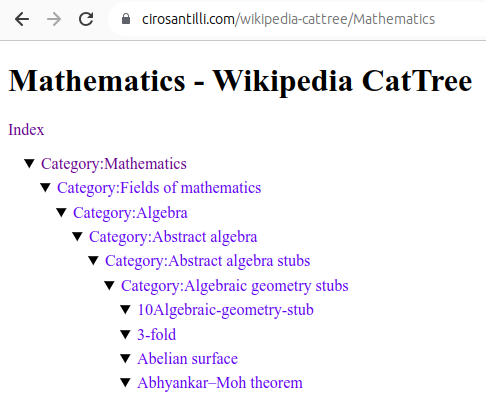
Figure 22. Mathematics dump of Wikipedia CatTree. Source. In this project, Ciro Santilli explored extracting the category and article tree out of the Wikipedia dumps.
- Mathematics
Figure 23. Diagram of the fundamental theorem on homomorphisms by Ciro Santilli (2020)Shows the relationship between group homomorphisms and normal subgroups.- Section "Formalization of mathematics": some early thoughts that could be expanded. Ciro almost had a stroke when he understood this stuff in his teens.
Figure 24. Simple example of the Discrete Fourier transform. Source. That was missing from Wikipedia page: en.wikipedia.org/wiki/Discrete_Fourier_transform!
- Network programming
- Physics
- What is the difference between plutonium and uranium?
Figure 25. Spacetime diagram illustrating how faster-than-light travel implies time travel. From: Does faster than light travel imply travelling back in time?
- Biology
Figure 26. Top view of an open Oxford Nanopore MinION. Source. From: Section "How to use an Oxford Nanopore MinION to extract DNA from river water and determine which bacteria live in it"Figure 27. Mass fractions in a minimal growth medium vs an amino acid cut in a simulation of the E. Coli Whole Cell Model by Covert Lab. Source. From: Section "E. Coli Whole Cell Model by Covert Lab"
- Quantum computing
- Section "Quantum computing is just matrix multiplication"
Figure 28. Visualization of the continuous deformation of states as we walk around the Bloch sphere represented as photon polarization arrows. From: Understanding the Bloch sphere.
- Bitcoin
- GIMP
Figure 29. GIMP screenshot part of how to combine two images side-by-side in GIMP?
- Home DIY
Figure 30. Total_Blackout_Cassette_Roller_Blind_With_Curtains.Source. From: Section "How to blackout your window without drilling"
- China
async (JavaScript) Updated 2025-07-16async is all present in JavaScript for two reasons:- you make network requests all the time
- JavaScript is single threaded, so if you are waiting for a network request, the UI freezes, see remarks on the deprecation of synchronous HTTP request at: developer.mozilla.org/en-US/docs/Web/API/XMLHttpRequest/Synchronous_and_Asynchronous_Requests
However, it is also Hell: how to convert
async to sync in JavaScript. CIA 2010 covert communication websites Communication mechanism Updated 2025-07-16
There are four main types of communication mechanisms found:These have short single word names with some meaning linked to their website.
- There is also one known instance where a .zip extension was used! web.archive.org/web/20131101104829*/http://plugged-into-news.net/weatherbug.zip as:
<applet codebase="/web/20101229222144oe_/http://plugged-into-news.net/" archive="/web/20101229222144oe_/http://plugged-into-news.net/weatherbug.zip"JAR is the most common comms, and one of the most distinctive, making it a great fingerprint. - JavaScript file. There are two subtypes:
- JavaScript with SHAs. Rare. Likely older. Way more fingerprintable.
- JavaScript without SHAs. They have all been obfuscated slightly different and compressed. But the file sizes are all very similar from 8kB to 10kB, and they all look similar, so visually it is very easy to detect a match with good likelyhood.
- Adobe Flash swf file. In all instances found so far, the name of the SWF matches the name of the second level domain exactly, e.g.:While this is somewhat of a fingerprint, it is worth noting that is was a relatively commonly used pattern. But it is also the rarest of the mechanisms. This is a at a dissonance with the rest of the web, which circa 2010 already had way more SWF than JAR apparently.
http://tee-shot.net/tee-shot.swfSome of the SWF websites have archives for empty/servletpages:which makes us think that it is a part of the SWF system../bailsnboots.com/20110201234509/servlet/teammate/index.html ./currentcommunique.com/20110130162713/servlet/summer/index.html ./mynepalnews.com/20110204095758/servlet/SnoopServlet/index.html ./mynepalnews.com/20110204095403/servlet/release/index.html ./www.hassannews.net/20101230175421/servlet/jordan/index.html ./zerosandonesnews.com/20110209084339/servlet/technews/index.html - CGI comms
Because the communication mechanisms are so crucial, they tend to be less varied, and serve as very good fingerprints. It is not ludicrous, e.g. identical files, but one look at a few and you will know the others.
CIA 2010 covert communication websites feedsdemexicoyelmundo.com JavaScript reverse engineering Updated 2025-07-16
The JavaScript of each website appears to be quite small and similarly sized. They are all minimized, but have reordered things around a bit.
For example consider: web.archive.org/web/20110202190932/http://feedsdemexicoyelmundo.com/mundo.js
First we have to know that the Wayback Machine adds some stuff before and after the original code. The actual code there starts at:and ends in:
ap={fg:['MSXML2.XMLHTTPck++;};return fu;};Further analysis would be needed.
CIA 2010 covert communication websites iraniangoals.com JavaScript reverse engineering Updated 2025-07-16
Some reverse engineering was done at: twitter.com/hackerfantastic/status/1575505438111571969?lang=en.
Notably, the password is hardcoded and its hash is stored in the JavaScript itself. The result is then submitted back via a POST request to
/cgi-bin/goal.cgi.TODO: how is the SHA calculated? Appears to be manual.
CIA 2010 covert communication websites Overview of Ciro Santilli's investigation Created 2025-05-07 Updated 2025-07-19
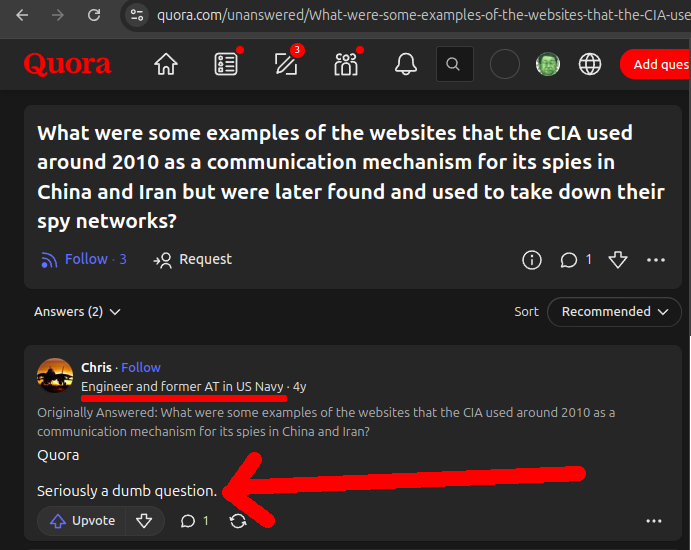
Ciro Santilli hard heard about the 2018 Yahoo article around 2020 while studying for his China campaign because the websites had been used to take down the Chinese CIA network in China. He even asked on Quora about it, but there were no publicly known domains at the time to serve as a starting point. Chris, Electrical Engineer and former Avionics Tech in the US Navy, even replied suggesting that obviously the CIA is so competent that it would never ever have its sites leaked like that:
Seriously a dumb question.
In 2023, one year after the Reuters article had been published, Ciro Santilli was killing some time on YouTube when he saw a curious video: Video 1. "Compromised Comms by Darknet Diaries (2023)". As soon as he understood what it was about and that it was likely related to the previously undisclosed websites that he was interested in, he went on to read the Reuters article that the podcast pointed him to.
Being a half-arsed web developer himself, Ciro knows that the attack surface of a website is about the size of Texas, and the potential for fingerprinting is off the charts with so many bits and pieces sticking out. And given that there were at least 885 of them, surely we should be able to find a few more than nine, right?
In particular, it is fun how these websites provide to anyone "live" examples of the USA spying on its own allies in the form of Wayback Machine archives.
Given all of this, Ciro knew he had to try and find some of the domains himself using the newly available information! It was an irresistible real-life capture the flag.
Chris, get fucked.
It was the YouTube suggestion for this video that made Ciro Santilli aware of the Reuters article almost one year after its publication, which kickstarted his research on the topic.
Full podcast transcript: darknetdiaries.com/transcript/75/
Ciro Santilli pinged the Podcast's host Jack Rhysider on Twitter and he ACK'ed which is cool, though he was skeptical about the strength of the fingerprints found, and didn't reply when clarification was offered. Perhaps the material is just not impactful enough for him to produce any new content based on it. Or also perhaps it comes too close to sources and methods for his own good as a presumably American citizen.
The first step was to try and obtain the domain names of all nine websites that Reuters had highlighted as they had only given two domains explicitly.
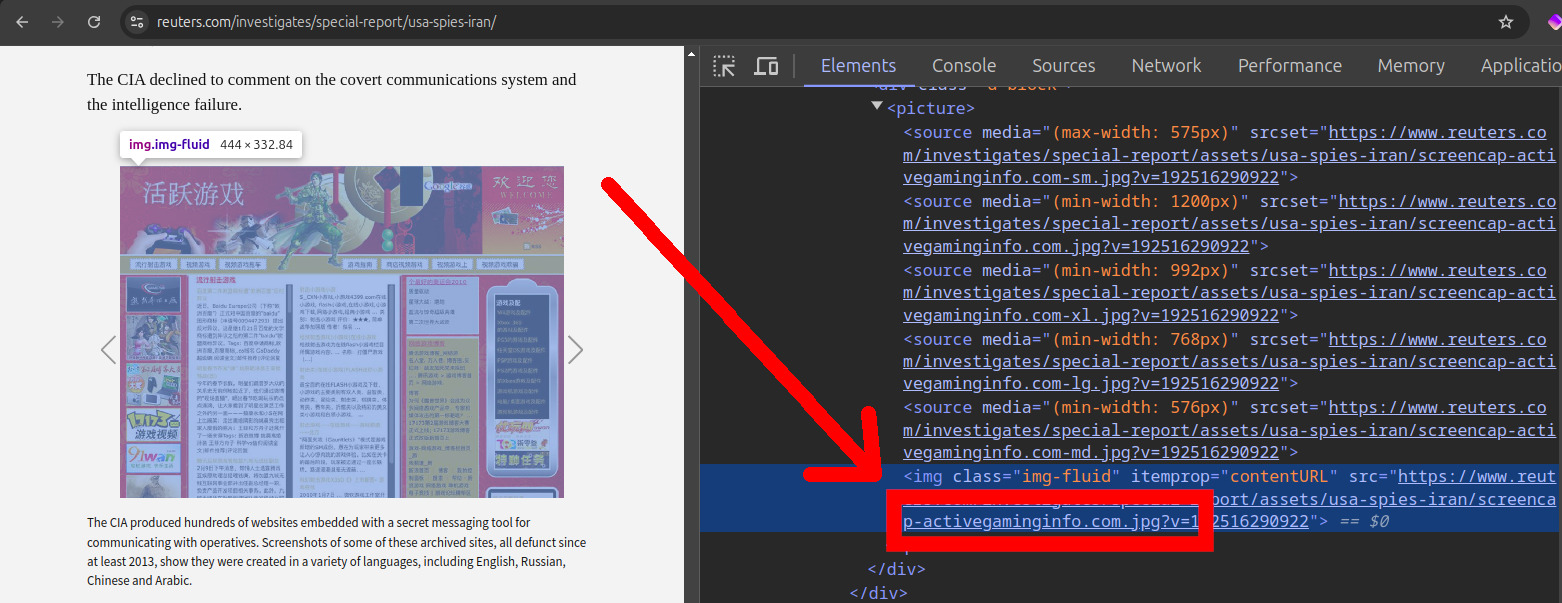
Thankfully however, either by carelessness or intentionally, this was easy to do by inspecting the address of the screenshots provided. For example, one of the URLs was:which corresponds to
https://www.reuters.com/investigates/special-report/assets/usa-spies-iran/screencap-activegaminginfo.com.jpg?v=192516290922activegaminginfo.com.Inspecting the Reuters article HTML source code
. Source. The Reuters article only gave one URL explicitly: iraniangoals.com. But most others could be found by inspecting the HTML of the screenshots provided, except for the Carson website.Once we had this, we were then able to inspect the websites on the Wayback Machine to better understand possible fingerprints such as their communication mechanism.
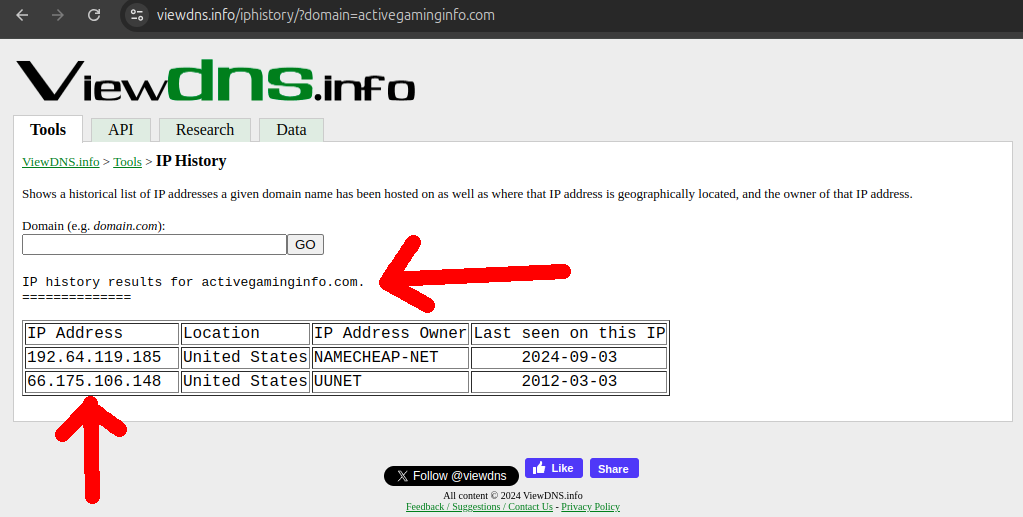
The next step was to use our knowledge of the sequential IP flaw to look for more neighbor websites to the nine we knew of.
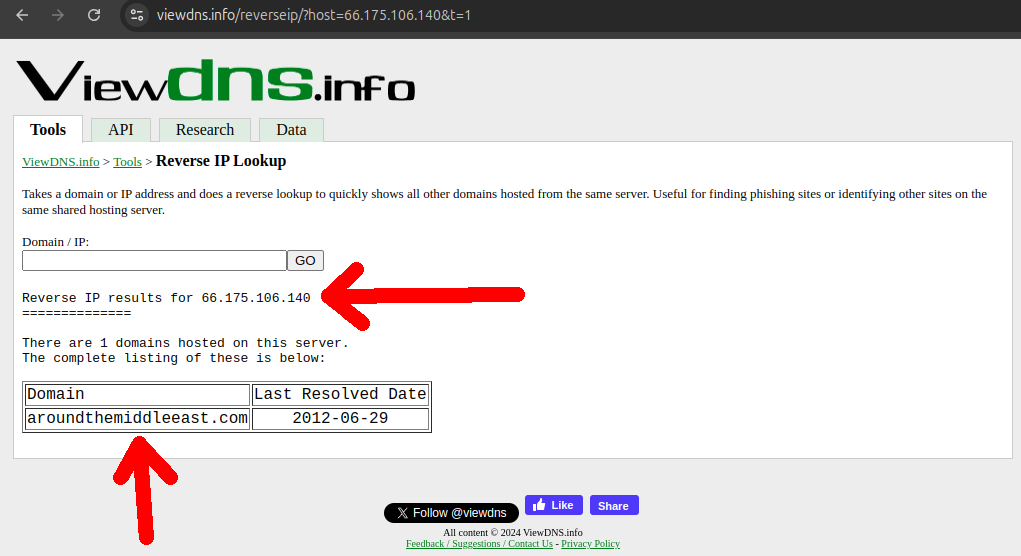
This was not so easy to do because the websites are down and so it requires historical data. But for our luck we found viewdns.info which allowed for 200 free historical queries (and they seem to have since removed this hard limit and moved to only throttling), leading to the discovery or some or our own new domains!
This gave us a larger website sample size in the order of the tens, which allowed us to better grasp more of the possible different styles of website and have a much better idea of what a good fingerprint would look like.
The next major and difficult step would be to find new IP ranges.
This was and still is a hacky heuristic process for us, but we've had the most success with the following methods:
- step 1) get huge lists of historic domain names. The two most valuable sources so far have been:
- step 2) filter the domain lists down somehow to a more manageable number of domains. The most successful heuristics have been:
- for 2013 DNS Census which has IPs, check that they are the only domain in a given IP, which was the case for the majority of CIA websites, but was already not so common for legitimate websites
- they have the word
newson the domain name, given that so many of the websites were fake news aggregators
- step 3) search on Wayback machine if any of those filtered domains contain URL's that could be those of a communication mechanism. In particular, we've used a small army of Tor bots to overcome the Wayback Machine's IP throttling and greatly increase our checking capacity
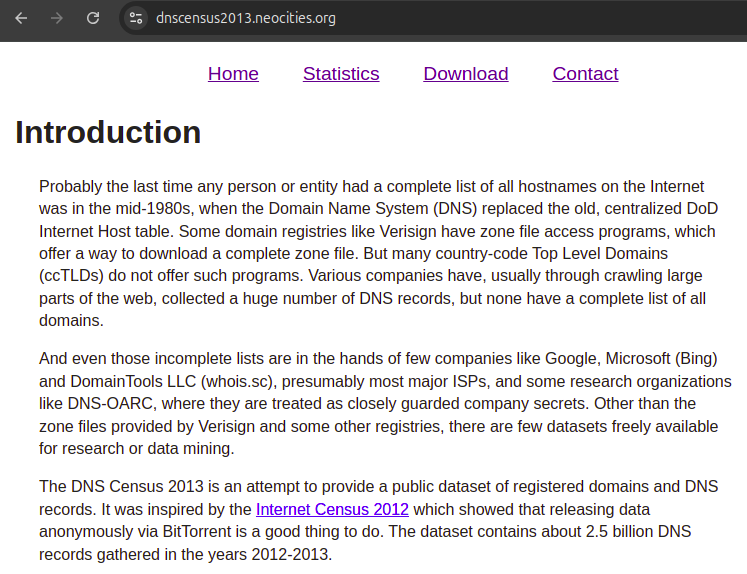
DNS Census 2013 website
. Source. This source provided valuable historical domain to IP data. It was likely extracted with an illegal botnet. Data excerpt from the CSVs:amazon.com,2012-02-01T21:33:36,72.21.194.1
amazon.com,2012-02-01T21:33:36,72.21.211.176
amazon.com,2013-10-02T19:03:39,72.21.194.212
amazon.com,2013-10-02T19:03:39,72.21.215.232
amazon.com.au,2012-02-10T08:03:38,207.171.166.22
amazon.com.au,2012-02-10T08:03:38,72.21.206.80
google.com,2012-01-28T05:33:40,74.125.159.103
google.com,2012-01-28T05:33:40,74.125.159.104
google.com,2013-10-02T19:02:35,74.125.239.41
google.com,2013-10-02T19:02:35,74.125.239.46The four communication mechanisms used by the CIA websites
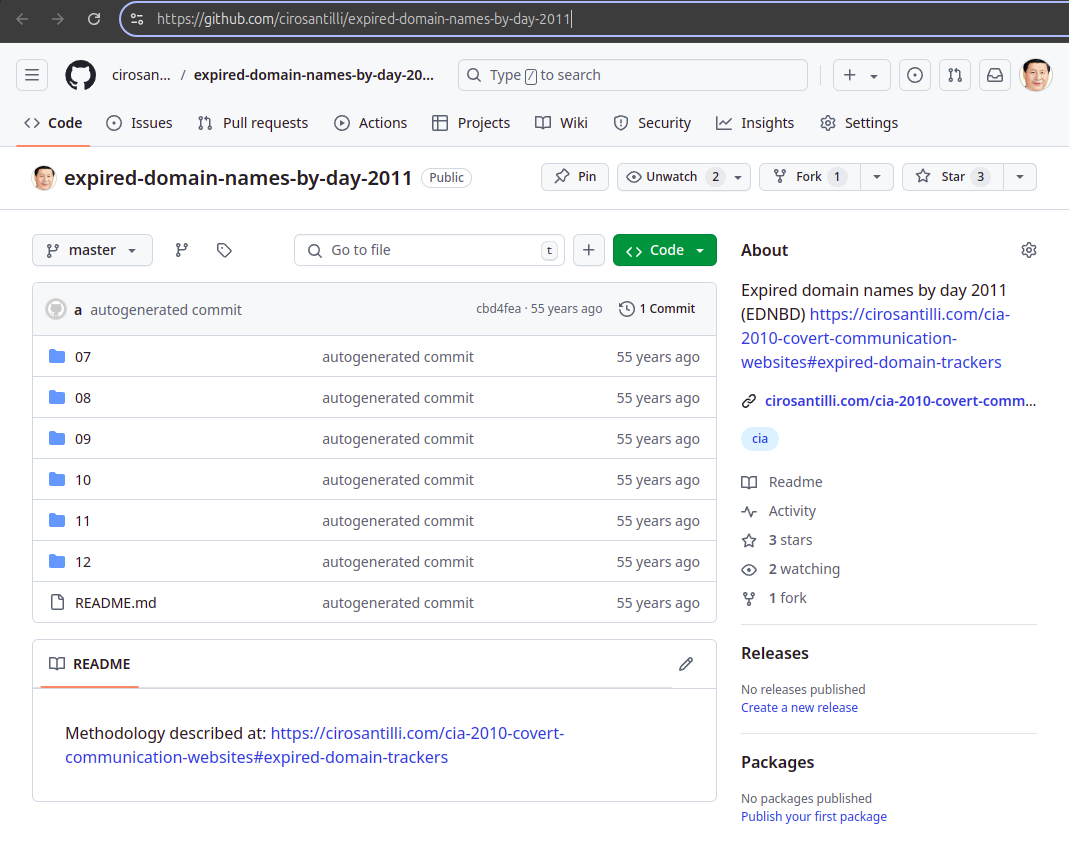
. Java Applets, Adobe Flash, JavaScript and HTTPSExpired domain names by day 2011
. Source. The scraping of expired domain trackers to Github was one of the positive outcomes of this project. CIA 2010 covert communication websites Reverse engineering Updated 2025-07-16
In this section we document the outcomes of more detailed inspection of both the communication mechanisms (JavaScript, JAR, swf) and HTML that might help to better fingerprint the websites.
CIA 2010 covert communication websites The Reuters websites Updated 2025-07-16
But by looking at the URLs of the screenshots they provided from other websites we can easily uncover all others that had screenshots, except for the Johnny Carson one, which is just generically named. E.g. the image for the Chinese one is www.reuters.com/investigates/special-report/assets/usa-spies-iran/screencap-activegaminginfo.com.jpg?v=192516290922 which leads us to domain activegaminginfo.com.
Oleg Shakirov later discovered that the Carson one had its domain written right on the screenshot, as part of a watermark present on the original website itself. Therefore the URLs of all the websites were in one way or another essentially given on the article.
The full list of domains from screenshots is:
- 2011 archive: web.archive.org/web/20110208113503/http://activegaminginfo.com/. Contains mentions of 2010.
- As of 2023, it seemed to be an actual legit photography website by German (amateur?) photographer Klaus Wägele. Archive: web.archive.org/web/20230323102504/https://www.capture-nature.com/Ciro Santilli actually sent him a message to let him know about the CIA thing in case he didn't, and he replied that he wasn't aware of it.
- 2011 archive: web.archive.org/web/20110201164741/https://www.headlines2day.com/. Dated "Copyright 2009".
fitness-dawg.com: English fitness website.2021 archive: web.archive.org/web/20110207104044/http://fitness-dawg.com/.rastadirect.net: English Rastafari culture website.- 2011 archive: web.archive.org/web/20110203021315/http://fightwithoutrules.com/. Contains mentions of 2009 news.
- 2004 archive: web.archive.org/web/20040113025122/http://alljohnny.com/.
CIA 2010 covert communication websites Timeline of public disclosures Created 2025-05-07 Updated 2025-07-26
The existence of the websites emerged in various stages, some of which may refer to this network or to other closely related communications failure since the published information is sometimes not clear enough.
May 21, 2011: various Iranian news outlets reported that:Iranian sources include:The news were picked up and repeated by Western outlets on the same day e.g.:At this point there were still no clear indications that the recruitment had been made with websites, however later revelations would later imply that.
30 individual suspected of spying for the US were arrested and 42 CIA operatives were identified in connection with the network.
- web.archive.org/web/20110729150642/http://www.presstv.ir/detail/180976.html "Iran dismantles US-linked spy network by Press TV (English, quoted above)
- web.archive.org/web/20110527084527/https://www.mehrnews.ir/NewsPrint.aspx?NewsID=1316973 "CIA spy network dismantled/30 American spies arrested" by Mehr news (Farsi)
- shiatv.net/video/dd6ee2d708a4a6cb2429 "Iran dismantles US-linked spy network" broadcast by IRIB, the main Iranian public broadcaster
- www.latimes.com/archives/blogs/babylon-beyond/story/2011-05-21/iran-intelligence-ministry-claims-to-arrest-30-alleged-cia-spies "Intelligence Ministry claims to arrest 30 alleged CIA spies" by the Los Angeles Times
Quite prophetically, this was on the same day that Christian radio broadcaster Harold Camping predicted that the world would come to an end.
December 2014: McClathy DC reported on "Intelligence, defense whistleblowers remain mired in broken system" that CIA contractor John A. Reidy had started raising concerns about the security of a communication systems used by the CIA and other sources mention that he started this in 2008[ref] The focus of the article is how he was then ignored and silenced for raising these concerns, which later turned out to be correct and leading to an intelligence catastrophe that started in 2010.[ref][ref] This appears to have come out after a heavily redacted appeal by Reidy against the CIA from October 2014 came into McClathy's possession.[ref] While Reidy's disclosures were responsible and don't give much away, given the little that they disclose it feels extremely likely that they were related to the same system we are interested in. Even heavily redacted, the few unredacted snippets of the appeal are pure gold and give a little bit of insight into the internal workings of the CIA. Some selections:
From January 2005 until January 2009, I worked as a government contractor at the CIA. I was assigned to [Directorate](ledger item 1) in the [Division] (ledger item 2). I served as a Uob) (ledger item 3) whose responsibility was to facilitate the dissemination of intelligence reporting to the Intelligence Community. I also served as a Oob 2) (ledger item 4) whose responsibility was to identify Human Intelligence (humint) targets of Interest for exploitation. I was assigned the telecommunications and information operations account.
As our efforts increased, we started to notice anomalies in our operations and conflicting intelligence reporting that indicated that several of our operations had been compromised. The indications ranged from [ redacted ] to sources abruptly and without reason ceasing all communications with us.
These warning signs were alarming due to the fact that our officers were approaching sources using [operational technique] (ledger item 16)
When our efforts began, ultimate operational authority rested with us. The other component provided the finances for the operation while we gave the operational guidance and the country specific knowledge.
knew we had a massive intelligence failure on our hands. All of our assets [ redacted ] were in jeopardy.
To give our compromise context, the U.S. communications infrastructure was under siege
All of this information was collected under the project cryptonym [cryptonym] (ledger item 52)
Meanwhile throughout 2010, I started to hear about catastrophic intelligence failures in the government office I formally worked for. More than one government employee reached out to me and notified me that the "nightmare scenario" I had described and tried to prevent had transpired. I was told that in upwards of 70% of our operations had been compromised.
it is not just a potential compromise in one country, It effects every country
May 2017: Mazzetti et al. reported for the New York Times at "Killing C.I.A. Informants, China Crippled U.S. Spying Operations" that:and that:
The Chinese government systematically dismantled C.I.A. spying operations in the country starting in 2010, killing or imprisoning more than a dozen sources over two years and crippling intelligence gathering there for years afterward.
January 2018: Pete Williams reported for NCB News at Alleged CIA China turncoat Lee may have compromised U.S. spies in Russia too that it was China that told Russia about the communications system:and that some theorize that former CIA agent Jerry Chun Shing Lee had betrayed Chinese spies, which some theorize may have been how China became aware of the communication network:According to Ex-C.I.A. Officer Sentenced to 19 Years in Chinese Espionage Conspiracy from November 2019 Lee was sentenced to 19 years in prison:
It was a shocking blow to an American spy agency that prides itself on its field operations. There was also a devastating human cost: Some 20 CIA sources were executed by the Chinese government, two former officials said — a higher number of dead than initially reported by NBC News and the New York Times. Then an unknown number of Russian assets also disappeared, sources say.
Soon after the task force concluded the Chinese had penetrated covcom, it got an even more troubling report: That after a joint training session between Chinese and Russian intelligence officers, the Russians "came back saying we got good info on covcom," as the former official put it
FBI agents began to suspect Lee after they received a tip that he had passed information to Chinese intelligence officers while working for a Japanese tobacco company in Hong Kong, sources said, a detail first reported Thursday by the New York Times. They also found it suspicious when Lee took a job at an auction house in Hong Kong that was co-owned by a senior Communist Party official, sources said. He eventually ended up working for Christie's, the international auction house.When agents searched Lee's hotel rooms in 2012, they found notebooks with the names of covert CIA sources, according to court documents.But not all of the agent arrests and deaths could be linked to information possessed by Lee, who left the CIA in 2007, the former officials said.
The former officer, Jerry Chun Shing Lee, 55, pleaded guilty in May to conspiring with Chinese intelligence agents starting in 2010, after he left the agency. Prosecutors detailed a long financial paper trail that they said showed that Mr. Lee received more than $840,000 for his work.
But F.B.I. agents who investigated whether he was the culprit passed on an opportunity to arrest him in the United States in 2013, allowing him to travel back to Hong Kong even after finding classified information in his luggage. F.B.I. agents had also covertly entered a hotel room Mr. Lee occupied in 2012, finding handwritten notes detailing the names and numbers of at least eight C.I.A. sources that he had handled in his capacity as a case officer.
Jerry Chun Shing Lee in blue tie at the unveiling of Leonardo da Vinci's 'Salvator Mundi' painting at the Christie's showroom in Hong Kong on Oct. 13, 2017
. Source. August 2018: Zach Dorfman reported for Foreign Policy at "Botched CIA Communications System Helped Blow Cover of Chinese Agents" that:and:Although no clear mention of websites is made in that article, the fact that there were "links" back to the CIA website strongly suggests that the communication was done through websites.
It was considered one of the CIA’s worst failures in decades: Over a two-year period starting in late 2010, Chinese authorities systematically dismantled the agency’s network of agents across the country, executing dozens of suspected U.S. spies. But since then, a question has loomed over the entire debacle. How were the Chinese able to roll up the network?
U.S. intelligence officers were also able to identify digital links between the covert communications system and the U.S. government itself, according to one former official—links the Chinese agencies almost certainly found as well. These digital links would have made it relatively easy for China to deduce that the covert communications system was being used by the CIA. In fact, some of these links pointed back to parts of the CIA’s own website, according to the former official.
The report also reveals that there was a temporary "interim system" that new sources would use while they were being vetted, but that it used the same style of system as the main system. It would be cool if we managed to identify which sites are interim or not somehow:
When CIA officers begin working with a new source, they often use an interim covert communications system—in case the person turns out to be a double agent.The communications system used in China during this period was internet-based and accessible from laptop or desktop computers, two of the former officials said.This interim, or “throwaway,” system, an encrypted digital program, allows for remote communication between an intelligence officer and a source, but it is also separated from the main communications system used with vetted sources, reducing the risk if an asset goes bad.
November 2018: Zach Dorfman and Jenna McLaughlin reported for Yahoo News the first clear report that the communication system was made up of websites at: "The CIA's communications suffered a catastrophic compromise. It started in Iran.":
In 2013, hundreds of CIA officers — many working nonstop for weeks — scrambled to contain a disaster of global proportions: a compromise of the agency’s internet-based covert communications system used to interact with its informants in dark corners around the world. Teams of CIA experts worked feverishly to take down and reconfigure the websites secretly used for these communications
The usage of of Google dorking is then mentioned:It seems to us that this would have been very difficult on the generically themed websites that we have found so far. This suggests the existence of a separate recruitment website network, perhaps the one reported in 2011 by Iran offering VISAs. It would be plausible that such network could link back to the CIA and other government websites. Recruited agents would only then later use the comms network to send information back. The target countries may have first found the recruitment network, and then injected double agents into it, who later came to know about the comms network. TODO: it would be awesome to find some of those recruitment websites!
In fact, the Iranians used Google to identify the website the CIA was using to communicate with agents.
Another very interesting mention is the platform had been over extended beyond its original domain application, which is in part why things went so catastrophically bad:
Former U.S. officials said the internet-based platform, which was first used in war zones in the Middle East, was not built to withstand the sophisticated counterintelligence efforts of a state actor like China or Iran. “It was never meant to be used long term for people to talk to sources,” said one former official. “The issue was that it was working well for too long, with too many people. But it was an elementary system.”
December 2018: a followup Yahoo News article "At the CIA, a fix to communications system that left trail of dead agents remains elusive" gives an interesting internal organizational overview of the failed operation:Much as in the case of Reidy, it is partly because of such internal dissatisfaction that so much has come out to the press, as agents feel that they have nowhere else to turn to.
Ciro Santilli conjectures that this fiasco was the motivation behind the creation of the Directorate of Digital Innovation.
As a result, many who are directly responsible for working with sources on the ground within the CIA’s Directorate of Operations are furious
The fiascos in Iran and China continue to be sticking points between the Directorate of Operations and the CIA’s Directorate of Science and Technology (DS&T) — the technical scientists. “There is a disconnect between the two directorates,” said one former CIA official. “I’m not sure that will be fixed anytime soon.”
Entire careers in the CIA’s Office of Technical Service — the part of DS&T directly responsible for developing covert communications systems — were built on these internet-based systems, said a former senior official. Raising concerns about them was “like calling someone’s baby ugly,” said this person.
Ciro Santilli conjectures that this fiasco was the motivation behind the creation of the Directorate of Digital Innovation.
That article also gives a cute insight into the OPSEC guidelines for the assets that used the websites:
CIA agents using the system were supposed to conduct “electronic surveillance detection routes” — that is, to bounce around on various sites on the internet before accessing the system, in order to cover their tracks — but often failed to do so, creating potentially suspicious patterns of internet usage, said this person.
29 September 2022: Reuters reported nine specific websites of the network at "America's Throwaway Spies", henceforth known only as "the Reuters article" in this article.
The most important thing that this article gave were screenshots of nine websites, including the domain names of two of them: iraniangoals.com and iraniangoalkicks.com:The "350-plus" number is a bit random, given that their own analysts stated a much higher 885 in their report.
In addition, some sites bore strikingly similar names. For example, while Hosseini was communicating with the CIA through Iraniangoals.com, a site named Iraniangoalkicks.com was built for another informant. At least two dozen of the 350-plus sites produced by the CIA appeared to be messaging platforms for Iranian operatives, the analysts found.
The article also reveals the critical flaw of the system; the usage of sequential IPs:
Online records they analyzed reveal the hosting space for these front websites was often purchased in bulk by the dozen, often from the same internet providers, on the same server space. The result was that numerical identifiers, or IP addresses, for many of these websites were sequential, much like houses on the same street.
It also mentions that other countries besides Iran and Chine were also likely targeted:
This vulnerability went far beyond Iran. Written in various languages, the websites appeared to be a conduit for CIA communications with operatives in at least 20 countries, among them China, Brazil, Russia, Thailand and Ghana, the analysts found.
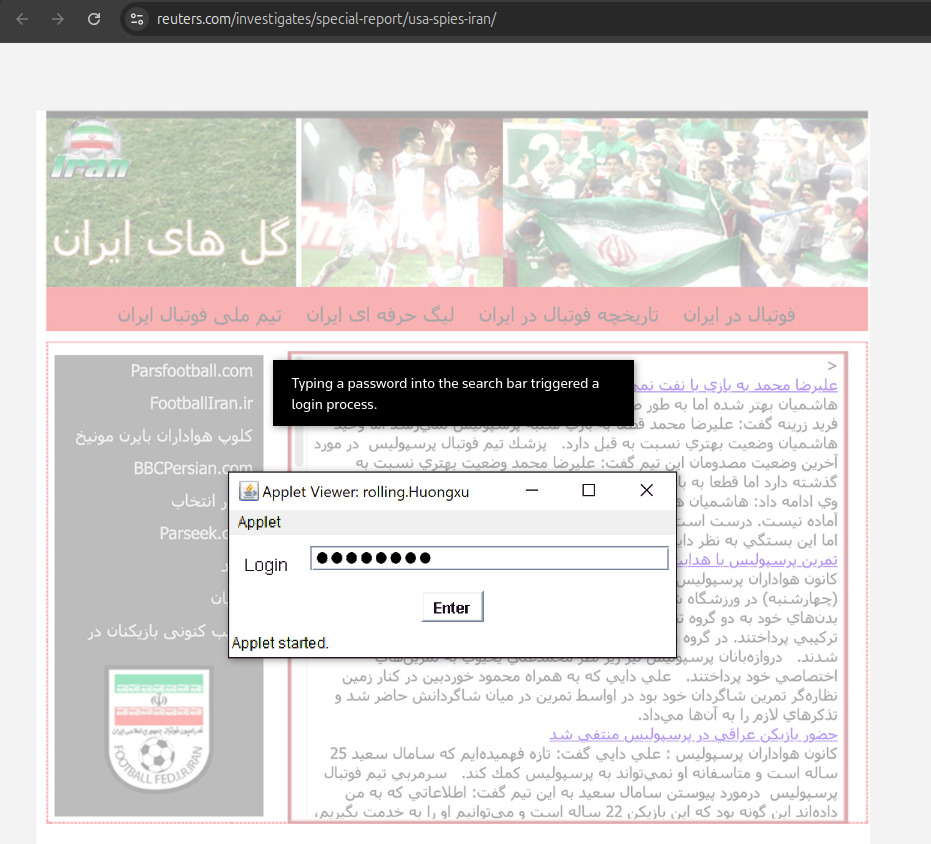
Reuters reconstruction of what the iraniangoals.com applet would have looked like
. Source. 29 September 2022: on the same day that Reuters published their report, Citizenlab, which Reuters used as analysts for the article, also simultaneously published their more technical account of things at "Statement on the fatal flaws found in a defunct CIA covert communications system".
One of the most important information given in that report is the large number of sites found, 885, and the fact that they are available on Wayback Machine:The million dollar question is "which website did they use" and "how much does it cost if anything" since our investigation has so far had to piece together a few different hacky sources but didn't spend any money. And a lot of money could be poured into this, e.g. DomainTools which might contain one of the largest historical databases, , seems to start at 15k USD / 1000 queries. One way to try and deduce which website they used is to look through their other research, e.g.:
Using only a single website, as well as publicly available material such as historical internet scanning results and the Internet Archive's Wayback Machine, we identified a network of 885 websites and have high confidence that the United States (US) Central Intelligence Agency (CIA) used these sites for covert communication.
- citizenlab.ca/2021/07/hooking-candiru-another-mercenary-spyware-vendor-comes-into-focus/ uses Censys, and it notably has historical data:Censys employee Silas Cutler AKA p1nk believes that Censys data does not reach that far back, since the company was only founded in 2017[ref].
- citizenlab.ca/2016/08/million-dollar-dissident-iphone-zero-day-nso-group-uae/ mentions scans.io/
- citizenlab.ca/2020/12/running-in-circles-uncovering-the-clients-of-cyberespionage-firm-circles/ mentions: www.shodan.io/
The article mentioned the different types of communication mechanisms found:
The websites included similar Java, JavaScript, Adobe Flash, and CGI artifacts that implemented or apparently loaded covert communications apps. In addition, blocks of sequential IP addresses registered to apparently fictitious US companies were used to host some of the websites. All of these flaws would have facilitated discovery by hostile parties.
They also give the dates range in which the system was active, which is very helpful for better targeting our searches:
And then a bomb, they claim to have found information regarding specific officers:This basically implies that they must have eitherWe have so for not yet found any such clear references to real individuals.
Nevertheless, a subset of the websites are linked to individuals who may be former and possibly still active intelligence community employees or assets:Given that we cannot rule out ongoing risks to CIA employees or assets, we are not publishing full technical details regarding our process of mapping out the network at this time. As a first step, we intend to conduct a limited disclosure to US Government oversight bodies.
- Several are currently abroad
- Another left mainland China in the time frame of the Chinese crackdown
- Another was subsequently employed by the US State Department
- Another now works at a foreign intelligence contractor
- found some communication layer level identifier, e.g. domain name registration HTTPS certificate certificate because it is impossible to believe that real agent names would have been present on the website content itself!
- or they may be instead talking about a separate recruitment network which offered the VISAs which we conjecture might have existed but currently have no examples of, and which might conceivably contain real embassy contacts
October 2022 Zach Dorfman, author of the 2018 Yahoo News and Foreign Policy articles gave some good anecdotes he had heard from his sources after the Reuters expose in his personal blog post On Agent Compromise in the Field, giving a more personal account of some of the events that took place:
Now, an important caveat: I have known dedicated former CIA officials who have spoken of the care, respect, and obligation they felt toward their sources, and the lengths they would go to assist them. For many case officers — that is, the CIA's primary corps of spy handlers — this is a core part of their professional identity.During the roll-up in China, for instance, a former U.S. official told me about a CIA officer who, aware that something was going terribly wrong there, organized final, assuredly dangerous, in-person meetings with agency sources. This distraught CIA officer essentially shoved wads of cash into sources' hands. This CIA officer warned them of the unfolding disaster and begged them to leave the country as fast as they could. Another source told me a story about a CIA official who, while being debriefed in Langley about the asset roll-up — and the slapdash COVCOM system — broke down in tears upon hearing that sources’ lives had been destroyed because of such obvious dereliction, of which they were previously unaware.
But I don’t want to oversell this point, either. By its nature, the world of espionage is steeped in the sordid aspects of human experience, exploiting people’s vulnerabilities for narrow informational gain. [...]Indeed, many former CIA officials have a decidedly pragmatic and amoral conception of their profession. Bad things happen when you spy, or recruit others to do so. [...] I had a conversation once with a former senior CIA official with experience in Iran issues who had an almost naturalistic view of recurring asset losses there over the years: for him, it was a built-in, cyclical feature of the work and environment, like the denuding of deciduous forests every fall.
Closing questions as off-topic Updated 2025-07-16
There's no point.
The question remains there, but people lose the ability to help the asker.
Reputation is meaningless regardless, since JavaScript gurus will always have 1000x more readers than low level junkies.
The deeper problem: the existence of multiple separate websites instead of just using the tags on a single website.
Examples:
Computational quantum mechanics Created 2025-04-18 Updated 2025-07-16
- www.youtube.com/watch?v=1Z9wo2CzJO8 "Schrodinger equation solved numerically in 3D" by Tetsuya Matsuno. 3D hydrogen atom, code may be hidden in some paper, maybe
- www.youtube.com/playlist?list=PLdCdV2GBGyXM0j66zrpDy2aMXr6cgrBJA "Computational Quantum Mechanics" by Let's Code Physics. Uses a 1D trinket.io.
- www.youtube.com/watch?v=BBt8EugN03Q Simulating Quantum Systems [Split Operator Method] by LeiosOS (2018)
- www.youtube.com/watch?v=86x0_-JGlGQ Simulating the Quantum World on a Classical Computer by Garnet Chan (2016) discusses how modeling only local entanglement can make certain simulations feasible
Simulation of the time-dependent Schrodinger equation (JavaScript Animation) by Coding Physics (2019)
Source. Source code: github.com/CodingPhysics/Schroedinger. One dimensional potentials, non-interacting particles. The code is clean, graphics based on github.com/processing/p5.js, and all maths from scratch. Source organization and comments are typical of numerical code, the anonymous author is was likely a Fortran user in the past.
A potential change patch in
sketch.js:- potential: x => 2E+4*Math.pow((4*x - 1)*(4*x - 3),2),
+ potential: x => 4*Math.pow(x - 0.5, 2),Quantum Mechanics 5b - Schrödinger Equation II by ViaScience (2013)
Source. 2D non-interacting particle in a box, description says using Scilab and points to source. Has a double slit simulation.Shiemaa&Vincent.jpgMessage:TODO identify Shiemaa and Vincent.
tx 36d0d77acd760f0aa549b6b314f0c1e9690baa6bcc2d0f07ea9f3167f4a5ec99, block 318836 (2014-09-03)Cost: ~0.002 BTC ~ $0.77 at the time.
Several other interesting uploads were also made around block 318836 (September 2014):
RedRaven.jpgbitfossil.org/e17b83234402d85f3a18207eec11bc5c4397f88aa880aae4fb7d15802806a971/index.htmEarth3Archive.jpgbitfossil.org/ae8d3b46b934bedc363e11abe8c8607171994470957c286274f699a0b3a9bbd7/index.htmSkyEarth5Archive.jpgbitfossil.org/ae8d3b46b934bedc363e11abe8c8607171994470957c286274f699a0b3a9bbd7/index.htm
BikeLady.jpgBike Lady by Allen Lee Vandever. tx 2c4b9497af8c0c0eb9383357b40c3de33dba0b4f481099a32719f2b9036da8e7, block 319927 (2014-09-10)
This seems to be a novel work uploaded by its creator artist Allen Vandever according to EMBII.[ref].
Arecibo_message.svgArecibo message on tx c6d2e535cd2ba4659e954a61198c66fd98c60f6475cf8ff92a404f3fe3a16c4b, block 337874 (2015-01-07)
An "artificially" colored visualization of the Arecibo message ripped from Wikipedia: en.wikipedia.org/wiki/File:Arecibo_message.svg (with attribution).
The cool thing about this image is that it highlights the striking parallels between the encoding of the Arecibo message with crypto graffiti, because in both cases people were creating undocumented new ways of communicating with strangers on a new medium in those early blockchain days.
The associated message contains the Arecibo message as ASCII 0's and 1's. When properly cut at the newlines, they draw the message as ASCII art, as the original Arecibo encoding intends, here's a version with the 0's replaced by spaces to make it more readabale:
1 1 1 1
1 1 1 1 1
1 1 1 1 1 11 1
1 1 1 1 1 1 1 1 1 1
11
11 1
11 1
1 1 1
11111
11 111 11 11
1 11 1
11 1 11 11 11 1
11111 11111 11111 11111
1 1
1 1
11111 11111
11 11 111 11
1 1 1
11 1 11 111 11 1
11111 11111 11111 11111
1 11 1
11
1 11 1
11111 11 11111
11
1 1 1
1 11 1
11 11 1
11 1 11
11 11
11 1 11
11 11 1
1 1 1
1 11 1
1 11 1
1 1 1
1 1 1
1 11
11 11
1 111 1 11
1 1
1 11111
1 1 111 1 1 11 11
1 111 1 111111
1 111 111 11 111
1 1 111 11
1 1 1 111111
1 1 1 11
1 11 11
111 1
111 1 1 1 1 1 1 1 1
111 1 1 1 1
1 1
11111
111111111
111 111
11 11
11 1 1 11
11 11 11 11
1 1 1 1 1 1
1 1 1 1 1 1
1 1 1 1
1 1 1
1 1
1 1 1
1111 11111 1 1111He sleeps in a temple.jpgDr_Craig_Wright.jpg
. Source. Associated message:
The image is present e.g. at: www.kitguru.net/channel/jon-martindale/australian-man-claims-he-is-satoshi-nakamoto-bitcoin-creator/ It was inscribed about two months after Craig publicly claimed that he is Satoshi.
This is a relatively unusual AtomSea & EMBII upload as it does not have the common toplevel transaction, everything, text + image fits into a single transaction. This is perhaps why the image is relatively low resolution to have a smaller size.
YellowRobot.jpgYellow Robot on tx 67b2facfd8160d4fa11b02829b6387d07537b57a7a24f19b029b2a5ae7b81830, block 450516 (2017-01-29)
The associated message reads:This is one of Ciro's favorite AtomSea & EMBII uploads. This is the cutest thing ever, and perfectly encapsules the "medium as an artform" approach to blockchain art. More Chiharu stalking at: ILoveYouMore.jpg.
Chiharu and I found this little yellow robot while exploring Chicago. It will be covered by tar or eventually removed but this tribute will remain. N 41.880778 E -87.629210
At twitter.com/EMBII4U/status/1615389973343268871 EMBII announced that he would be giving off shares of that image on a Bitcoin-based NFT sale system he's making called Sup!?, and in December 2023 gave 2/300 shares to Ciro Santilli. Amen. The transaction list can be seen on the web UI at: p2fk.io/GetObjectByAddress/1KUyhHLrK1ckY8W7Qu31h6gFkXoihWHMzi?mainnet=true&verbose=true It had unfortunately never sold as of 2025, the only activity was EMBII giving off some shares and two listings of 1/300 for 1 BTC. Poor EMBII!
Other possibly novel EMBII street photography:
- bitfossil.com/f2efd446475ad58a3ea808cc0f05a63c55cece9fced70d84799a1ffce5d307e4/index.htm "I will not Stop until the Finite becomes the Infinite."
Audio:
alien.wavblock 318638 bitfossil.org/a3a24d6ea01ce481a50346818b8977220687f3ba385838fe8894ce61c9718bbc/OneGiantLeapForMankind.mp3at tx 4f5b25fa8021c67235423930580e69121aa0d2c2bb779f75139bf442f8dc7297 EMBII-indexed at 743f3286b00fc96c13db4b16d5aead8a1e059fee9ce775b1761be9be5bdc2501 and then indexed at: 0427ec598df38b7d7dc75721316c0bbdec54de4871e11aff8ea64f3717c07efbThe toplevel index does appear on Bitfossil: bitfossil.org/0427ec598df38b7d7dc75721316c0bbdec54de4871e11aff8ea64f3717c07efb/index.htm but the audio is not there as it was for Spock below, maybe a bug on upload/Bitfossil?Spock_Live_Long_And_Prosper.mp3block 345858 bitfossil.org/1bc87dbff1ff5831287f62ac7cf95579794e4386688479bab66174963f9a4a0c/index.htm. Audio of Mr. Spock saying the Vulcan salute.OuterSpace.mp3block 409471 bitfossil.org/c14c1bd862bab6269052bf0a2cda7a35940d7a2d9c3415d4fb8fb8dcb9394fae/ "Outer Space by embii 4MB Large file storage test Apertus 0.3.5-beta" OMG, I don't want to calculate how much it cost to upload this, it will make me sad.At twitter.com/EMBII4U/status/1655969645927563266 EMBII mentions that this inscription, made by him, is the largest inscription he knows of.TODO song composer/performer?- bitfossil.com/c2b170ff450f4529dfbd784e0cf5cdddaca494e67a243dd846c0a9450a5558af/ (2021-03-13) contains
Seikilos.mid, a MIDI file
Interesting text:
- block 273522 bitfossil.org/70fd289901bae0409f27237506c330588d917716944c6359a8711b0ad6b4ce76/index.htm pi to 1000+ decimal digits:
- bitfossil.org/8522787e7e49f3f3b6a9f9e86bc30336d26a3acbaecc93809d2e8b4bb1c4d611/ "Antarctic Ice Cores Revised 800KYr CO2 Data" evidence for global warming
- bitfossil.org/ffa6893a70bcde9b940df9823e0f597f0b6cff964c78473c77db838655e1aeb5/ en.wikipedia.org/wiki/Laudato_si', global warming related
HTML pages:
- block 335290 bitfossil.org/0166db6053f1969c28de8b1f9a8fa4ec890cc4bdfee7602757993b306bb7f295/ JavaScript animated timer clock counting down until the start of the next year
- block 340379 bitfossil.org/062990d54045a9c316110fb713009d1313b2f64c4b216d66891c7284d6c1ca0e/ links to bitfossil.org/062990d54045a9c316110fb713009d1313b2f64c4b216d66891c7284d6c1ca0e/bong-ball.html and has a working JavaScript Pong
- block 328445
tom-signature.jpgbitfossil.org/daa050bf8ac22752e40412c9265b4533f68ab8e6ed26d2db1eeee6710e7d9e4b/index.htm Unrendered HTML of:Likely an obituary for: Thomas L. Magliozzi. Images show fine though.- www.cartalk.com/content/tom-and-rays-bios-photos-2
- www.cartalk.com/content/rant-and-rave-36 "The New Theory of Learning" which agrees perfectly with backward design
- block 401648 bitfossil.com/31c5e5336512568e4a1deb4bbf0e57c3565c32094c0e1a118c48e7929ab49e35/bong-ball.html another one! This one is full-screen, and does not have JavaScript
alerts :-) - block 401657 bitfossil.org/03cb74f270d498302d4dd9cbe82c090d801c8840ab6cb26b71d862489b981db8/ has a JavaScript Pac-Man
Cool data embedded in the Bitcoin blockchain Ordinal ASCII art inscription Updated 2025-07-16
It was obtained by casually scrolling down the list of the largest text ordinal inscription on less until patience ran out.
Some of them are dedicated ASCII art inscriptions, others are just small highlights to other more important text like code.
Although tere is some element of commercialism in some those inscriptions, a bit like what is rampant in the images, some of them are honestly just cool and possibly novel.
Ordinal ruleset inscription collections:
- Humongous surfers. These are very large ASCII arts, by far the largest on the chain. Being so large allows for shades of gray to be encoded on the average luminosith of individual letters:
- tx 0f29dab68e9898f9349ef4508908f7df48dc56577cfd94ff173dd2c1b29ad7a3 (240,300 bytes): surfer girl
Figure 1. Surfer girl. Screenshot of the ordinals.com/inscription/0f29dab68e9898f9349ef4508908f7df48dc56577cfd94ff173dd2c1b29ad7a3i0 Ordinal ASCII art inscription as seen on Chromium 85. - tx b256c850f8cab037d387d3db70643b79f5848565181b341de6c44f86307db9e7
- tx d0e090aeeb289e19b8c9ad71c00daa28367e9afc4593c89513e4f96abcda8ea5
- tx fb754df7b17c7b76a6508b5d4e29f89d55ada38cf1f75ca4d797c58f45b73cd1
- tx a7e6697781513bdeddada7c32b6200fb8499624664ba056f8318541b63f68c36
- tx 0f29dab68e9898f9349ef4508908f7df48dc56577cfd94ff173dd2c1b29ad7a3 (240,300 bytes): surfer girl
- Michael Jackson Unicode art. Uses Unicode Braille characters. Marked "First Onchain Collection" and "Legends @ BTC" . Pretty cool design, the textures are quite cool and suggest glittering flying seat. Though if those ever sell, someone is going to get sued to Hell by MJ's estate!
- 1/12 tx 7e6c5f8ebb41604c79f2af60bb7af623c42b32afe4d7571ba81d7b9b44d33a2d
- 2/12 tx 8ac99472b865d01f8724ba23b6f79ca56d30b44fae0eb509984237b722b812c3
- 5/12 tx 74c94ceba91cf59de2740bcfa5bc2fdb3ea0d4499e73a12100ed365d25ae9061
- 7/12 tx 0360a10e67365ab8cc4e32f199c71cabf4fb6a08ca9773dd1d13d7f7936dcf99
- 8/12 tx 4814880f931db8aa59e1c2aba2c227e83d928d297cbe91978458b6d83e38ddfc
- 9/12 tx 909228c88176b65f5705ade5fa059030d4c646cacd171737af03ac965047fa82
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⠀⠀⡀⠀⠄⠀⠀⠄⠀⠠⠀⠀⠂⠀⠄⠂⣀⠄⠂⠠⠐⠀⡀⠂⠐⠠⠈⠄⠂⠡⠐⠈⠄⠡⠈⠄⠡⠈⠄⠡⠈⠄⠡⠈⠄⠡⠈⠄⠡⠈⠄⠡⡈⠄⡃⠌⡐⠡⡈⠄⡁⢂⠡⠐⠀⢂⠀⠂⠀⠄⠀⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠐⠀⠀⠂⠈⠀⠀⠄⠀⢀⠠⠐⠀⠠⠐⠀⠀⢁⢠⣼⣶⡶⠛⠛⢋⠀⠂⠁⠄⠈⣄⣦⣁⣂⠡⢀⠡⠈⠄⠡⠈⠄⠡⠈⠄⠡⠈⠄⠡⠈⠄⠡⠈⠄⠡⠈⢄⠡⢐⡈⠔⡈⠤⠑⡀⠆⡐⢀⠂⠌⡐⠀⠄⠂⠁⠠⠀⠀⠀⠂⠀⢀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⡀⠄⠀⠁⠀⡀⠀⠂⠀⠐⠀⠠⠀⠠⠀⠀⢀⠂⠀⠄⠈⣠⣶⣿⣏⠖⠂⠁⡐⢀⠠⢁⠈⠄⣱⢏⡲⢭⡛⠿⠷⠶⢥⣈⠄⠡⠈⠄⠡⢈⠐⠡⢈⠐⠡⠈⠄⠡⠈⠄⡁⢂⠌⠄⡒⠌⡐⠡⢃⠌⡐⢀⠂⠌⡐⠠⢈⠀⠂⡁⢀⠂⠁⡀⠐⠈⠀⠀⢀⠀⠐⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠄⠀⢀⠀⠈⠀⡀⠄⠀⠄⠐⠈⠀⠀⠄⠂⣰⣿⣿⠫⠁⠀⠂⢱⠀⡀⠀⢀⡈⠼⣇⢯⡒⠥⢚⠡⠀⠀⠀⠈⠑⠶⣥⣈⠔⡈⠄⣁⠂⠌⠄⠡⢈⠂⢡⠈⡐⠄⠌⡒⢨⠐⡡⠑⡌⠰⠈⠤⢈⠐⠠⠁⠄⠂⡁⠠⠀⡀⠂⠀⠄⠐⠀⠠⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⠀⠠⠀⠀⠀⠂⠀⠈⠀⠀⠠⠀⠀⠠⠀⠀⡀⠠⠀⠂⠁⠚⠄⡆⢸⣿⡟⡃⠄⡂⠁⠠⠈⠳⣶⣄⡠⣸⡝⢶⢢⡑⠊⠄⡑⢢⡀⠀⠀⠀⠀⠉⠿⡆⠐⡈⠄⡈⠔⡈⠐⠂⢌⠀⠆⡐⠨⠐⠤⢁⠆⢡⠑⡈⠅⡑⠂⡄⠊⠄⠡⢈⠐⢀⠂⢁⠀⠂⠁⡀⠂⠀⠄⠀⠠⠀⠐⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠠⠀⠀⠐⠀⠁⢀⠀⠄⠐⢀⠠⢀⠐⡀⠦⠐⡀⠀⠁⠄⠋⠉⠴⢁⠈⡙⠇⠀⠂⠁⠈⠛⢿⣷⡿⣜⢢⠙⠄⠂⠀⠠⠙⠦⠀⠀⠀⠠⠀⠄⢃⡐⡐⠠⠂⠄⢃⢁⠂⠌⡐⠠⣁⠩⠐⡌⠰⡁⢎⠰⡁⠆⢡⠀⠅⣈⠐⠠⠈⠄⢂⠠⠀⢁⠀⠄⠐⠀⠠⠐⠀⠀⠀⠀⢀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⡀⠀⠠⠀⠐⠀⡀⠄⠡⠈⠐⠂⢈⠂⠑⠐⠨⡀⠀⠀⠉⠁⠈⠀⠀⠠⠐⠀⠘⡄⠂⢀⠐⠈⢠⣀⠀⠀⠀⠉⠻⢿⣷⣭⡄⠀⠀⠀⢀⠀⠀⠀⠁⠀⠌⡐⢢⣾⣿⣷⡇⠌⣀⠂⠌⡐⠠⠡⠄⢂⠱⢈⠆⠱⣈⠒⠤⢉⠄⢊⡐⠠⠈⠄⠡⢈⠠⠀⠌⢀⠠⠀⠂⠀⠄⠀⠄⠂⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠠⠀⠀⡀⠀⠈⢀⠠⠀⠄⠀⠀⠁⠀⠁⡀⡀⠀⡄⠀⢈⠁⠆⠀⡁⠀⡌⢆⠟⠛⠃⠀⠀⠀⢀⠐⢀⠀⠙⠻⣿⣶⣄⠀⠀⠀⠐⠈⢀⠐⠠⠄⣩⣿⣿⣿⠩⠐⠠⢈⡐⠠⠑⡠⠉⡄⠢⣁⠊⢅⠢⡉⢆⠡⢊⠤⠐⠡⠈⠄⡁⢂⠐⢈⠠⠀⡀⠂⠁⠠⠀⠂⢀⠀⠠⠐⠀⠀⠠⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠐⠀⠁⠀⠀⠐⢈⠀⠀⠂⠀⠄⠀⢠⠀⡀⠀⠀⠐⠂⢁⢀⠐⠠⠀⠄⠀⠈⢀⠀⠄⠐⠤⠑⢈⠈⠄⠚⠧⠀⠡⠀⢀⠀⠄⠀⠀⢀⠈⡙⢿⣻⣤⡀⠂⠈⠀⠌⡐⠐⡀⢋⠉⢃⠰⠉⢄⠡⠠⠑⡠⢁⠒⡈⠔⡠⢉⠢⠑⡌⢢⠑⡌⠄⢃⠌⡐⢂⠐⠠⠈⠄⠂⠐⡀⠄⠁⠠⠐⠀⡀⠠⠀⠀⠀⢀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠠⠀⠀⠠⠀⠀⢀⠀⠈⠀⠀⠀⠄⠀⠀⡀⠀⢀⠀⠀⠆⠠⠈⠀⠀⠀⠠⠀⢊⠴⢂⠡⢀⠠⠐⡈⠔⡈⠀⠀⠠⠐⣀⠁⠄⠀⠀⠈⠐⠀⠠⢀⡐⡈⠄⡁⠯⣽⣆⠀⠁⢂⡐⠡⠴⠋⠀⢀⠂⡉⠄⢂⡁⠆⡁⢂⠂⡅⠢⢑⠢⢁⠣⡘⢄⠣⡐⢉⠄⢂⡐⠠⠈⠄⠡⢈⠀⠡⠀⡐⠈⢀⠐⠀⢀⠀⠄⠈⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⠀⠠⠀⠀⠀⠂⠁⢀⠠⠀⢀⠈⠀⠀⠂⠄⠀⠀⠀⠀⠀⠀⠀⠂⠀⠀⠀⠒⣡⠒⠡⠒⠠⠄⠀⠠⠀⠀⠄⣬⠃⠀⠠⠁⠀⠄⡁⢦⠼⣰⣥⠖⠀⡀⠙⠳⡀⠀⢆⢁⠂⠡⠐⠤⢈⠐⡈⠤⠐⡐⡈⠄⢒⡀⠣⠌⡰⠁⢆⠱⡈⠆⡑⢨⠈⠤⠀⡅⠈⠄⡁⠂⠌⠐⡀⠄⠂⠀⠄⠈⠀⢀⠠⠀⠀⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠐⠀⠀⠀⠀⠀⠀⠀⡀⠁⠀⢀⠀⠀⠡⠀⡐⠀⠈⡀⠀⠀⠀⠐⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠂⠂⠀⠁⠀⠀⠀⠀⢠⣈⡇⠀⠠⠐⠠⢁⠢⣉⠆⡉⠴⣁⣈⡙⠜⠃⠄⡁⢂⠘⠆⣈⠡⠀⠐⢂⠡⠐⢂⠡⢐⠠⠉⡄⠰⢁⠊⠔⣉⠢⡑⢌⢂⠱⡀⢊⠄⡡⠠⢁⠂⠄⠡⠈⠄⠐⡀⠌⠀⠂⢀⠁⠀⢀⠠⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠂⠀⠀⡀⠁⠀⠈⠀⢀⠀⠐⠀⠀⡀⠀⠡⢀⠑⡀⠠⠁⠈⡀⠂⡀⠐⠠⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠐⠒⣠⣽⣿⠃⠀⠁⢂⠱⣂⠑⡌⡐⣍⢲⣀⡉⠉⠀⠁⠂⠴⡲⣌⠐⡀⠆⠀⠈⡄⢂⡉⠄⢊⠄⠂⠥⠐⣁⠊⢌⠒⡠⢃⠜⡠⢊⠤⢑⠠⠒⠠⢁⠂⠌⠠⠁⠌⡀⠡⢀⠐⠈⠀⠄⢀⠈⠀⠀⡀⠀⠈⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⡀⠀⠀⠀⠠⠐⠀⠀⢀⠠⠐⠀⠀⠀⠄⠠⠐⠠⠠⠁⠀⠰⢀⠑⠀⠂⠀⠀⠀⠀⠀⠀⠀⠀⠀⠠⠀⠈⢠⡜⣽⣿⣯⢡⠀⠈⠠⠑⠤⢣⠐⠱⠌⢧⡍⠁⠀⠀⠈⠀⠀⠉⣏⠓⡐⢈⠀⢁⠰⢀⠂⠜⠠⡈⠜⠠⡁⢂⠅⡊⠤⠑⡌⢢⠑⡌⢢⠁⠆⡡⠑⡠⠈⡄⠡⢈⠐⢀⠂⠄⠂⢁⠀⠂⠀⡀⠄⠁⠀⡀⠀⠠⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠂⠁⠀⠀⠄⠈⠀⠀⠐⠈⠀⠀⠀⠄⠂⠀⡀⠀⠠⠀⠡⠈⠠⠐⠀⠠⠐⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠠⡘⡼⢻⣿⣲⢣⠎⡰⠀⠁⡈⠀⠄⠂⠠⠀⠀⠀⠀⠀⠁⡀⠀⠁⠀⠤⢃⠙⣆⠀⠀⣂⠡⠘⡈⠔⡐⠌⠡⡐⢡⠘⡠⢊⡑⢌⠢⡑⢌⠢⡑⡈⠤⠑⠠⡁⠄⡁⠂⠌⡀⠂⠄⠡⢀⣄⣂⣡⣤⣴⡶⠀⠀⠀⢀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⡀⠀⠄⠀⠀⠂⠀⠐⠀⢀⠈⠀⠀⠀⠄⠀⠐⠀⠀⠄⠀⡀⠁⠐⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⡌⡐⣸⢱⢻⣿⠇⢣⠘⢄⠓⡲⠄⠢⠐⡁⢂⠁⠀⢀⠀⠄⠀⠀⢀⠈⠀⢈⠀⠣⢮⠀⠀⡤⠈⢅⠒⠠⡁⢊⠡⠐⢂⠢⢑⠂⡌⢢⠑⡌⢢⠑⠤⠑⡈⠆⠡⠐⡀⢂⠁⠂⠄⣡⣾⣿⣿⣿⣟⣯⣛⣃⣀⣐⣀⣀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠐⠀⠀⠀⠀⡀⠐⠀⠀⠐⠈⠀⠀⠠⠈⠀⠀⠐⠀⠈⢀⠠⠐⠀⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠄⠀⠀⡔⢠⠁⣼⡃⡎⣿⡘⡄⠣⠌⢂⠡⡌⠆⠡⠐⠠⢈⠀⠀⠀⠀⠀⠂⠀⠀⠀⠀⠂⠡⢀⠀⠀⡷⢫⡄⠌⡡⠐⣁⢂⠩⠠⢑⡈⢆⡘⢄⠣⡘⠤⣉⠢⢑⠠⢁⢊⠐⡐⢠⢌⣴⣾⣿⠿⣩⢝⠲⠌⣻⣿⣟⣟⣿⣿⡿⠛⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⡀⠀⢀⠀⠁⠀⠀⢀⠈⠀⠀⠂⠈⠀⠀⠂⠁⢀⠀⠁⠀⡀⠄⠂⢀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⠂⠔⡁⠄⢺⣿⣿⢿⣿⢦⡁⢎⡴⢋⠔⡨⢐⠡⡘⠠⠀⠀⠀⠁⠀⠀⠀⠀⠄⠂⡔⣀⠠⠀⠀⣐⢧⠾⡶⢥⢒⠠⢂⠡⢁⠂⡌⠰⢈⠢⡑⢌⠒⡄⢃⠢⢁⢂⢂⡜⡘⣜⢾⣿⣿⣥⣘⠠⢈⠐⠠⢙⣿⣻⣯⣵⣿⠁⠀⠠⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⠀⠁⠀⢀⠀⠁⠀⠂⠁⠠⠐⠀⡀⢀⠈⠀⡀⠠⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠄⠂⠀⠌⣸⣿⣧⣏⣮⢳⡼⢏⡘⢤⠚⢠⠃⠰⣁⠂⡁⠀⠁⠀⠀⠐⠀⠀⠀⠤⠉⠀⠁⠀⠀⢋⠌⠐⡀⣊⣾⡷⣾⠤⣁⠒⣀⠣⢈⠔⡁⢎⡰⣈⡦⡵⠎⠎⠲⢀⠁⠀⠌⠡⢋⡾⠵⢾⣤⣎⣰⢀⡆⡱⣾⠘⠀⢀⠀⠀⡀⠀⠀⠠⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠐⠀⠀⠂⠀⠀⡀⠈⠀⡀⠀⠁⠀⠂⠀⠄⠀⡀⠀⠠⠐⠀⠠⠀⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢂⠁⠂⡍⣿⣿⣷⣯⡟⠱⡈⠜⡠⢉⠦⢁⢣⠦⣥⠀⠀⡀⠐⠀⠀⠀⠀⠄⠀⠠⠀⠁⠀⠀⠠⢀⠡⢐⠩⣴⣧⣍⣦⢰⡶⣤⡻⣵⢞⡻⢟⡋⣍⠒⢍⠒⡌⠐⠀⢠⠈⢀⠀⠡⠼⠀⡀⢀⠀⠉⠉⠈⠁⠀⡀⠠⠀⢀⠀⠀⠀⠐⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠠⠀⠀⢀⠀⠠⠀⠀⠐⠀⠀⡀⠁⠐⠀⠠⠀⠂⠀⠐⠀⠠⠈⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠄⢊⠱⣘⠼⣿⣿⣟⡰⢃⠬⣑⠢⢍⢂⠡⣎⠝⡂⠅⠀⠀⠀⡀⠀⠂⠀⠀⠠⢁⠂⠈⠀⠀⠁⡬⠖⠨⢀⠻⠿⠛⣈⠤⠑⠡⠼⡐⢆⡉⠌⡑⠌⠐⡀⠠⠀⢂⡁⢖⣈⠤⢜⠒⡁⠐⢀⠀⠄⠈⡀⠁⠠⠁⠀⡀⠄⠀⠀⠄⠂⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠠⠀⠀⠀⠀⠂⢀⠀⠁⠀⠐⠀⠈⠀⠐⠀⠁⡀⠂⠁⡀⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠠⠀⢈⠐⡌⢢⠌⡻⢿⣯⣟⠶⣉⠖⡡⢊⠐⡊⣑⢨⣰⡼⢃⠀⠀⠁⠀⡀⠀⠀⠄⠀⠌⠐⠈⠆⠀⠘⢂⠄⠁⠄⠂⠄⡡⠀⢠⠛⢄⠓⡀⠒⠠⠐⠠⡁⠆⡰⢀⠬⣁⠆⣑⠚⡘⠠⠀⠄⡁⠄⠂⠐⡀⠠⠀⢁⠀⠂⢀⠀⠐⠀⢀⠀⠀⠐⠈⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⡀⠀⠄⠂⠁⠀⡀⠀⠈⢀⠠⠈⠀⠁⠠⠈⢀⠀⠄⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠂⠀⠀⠀⢀⠂⡘⢄⠫⣖⠱⢚⠟⠿⢷⣯⣶⠯⢞⡵⣮⢗⠳⣌⠣⠄⠂⠀⠂⠐⠀⠀⡀⠈⡐⠠⠈⠀⠀⢀⠂⠄⢨⠀⠆⠸⠄⠐⠠⢁⠂⠡⠤⠁⠆⡡⣒⠀⢒⠧⠂⠕⡈⠐⡀⠂⠄⠡⠈⠄⠐⠠⠁⢂⠀⠐⢀⠠⠀⠂⠀⠀⠂⠈⠀⠀⠄⠀⠀⠀⠠⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠠⠀⠀⢀⠀⠀⠄⠐⠀⠀⡀⠁⠀⡀⠄⠈⠀⠄⠐⠀⠠⠀⠐⠀⠂⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⡀⠢⢌⡌⠰⣈⠛⣦⣭⣩⣍⡴⣰⠚⣭⣞⠳⢎⡳⣌⠡⠂⠀⠠⠈⠀⡐⠀⠀⠀⠄⠡⠈⠄⠀⢀⠋⠆⡖⠨⢂⠁⡐⣈⠣⢄⡈⠔⣤⢩⠰⠥⢂⠋⠌⡐⡉⢐⠠⠁⠄⠡⠈⠄⠡⠈⠄⠁⠂⠄⠂⢁⠠⠀⠐⡀⠁⠐⠀⠁⡀⠂⠀⡀⠂⠀⢀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⢀⠀⠂⠀⠁⠀⠠⠁⠀⠀⠂⠁⠀⠂⠈⢀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢂⠡⠀⠃⠂⣀⠳⣌⠳⣄⣃⠓⡌⢎⢥⣿⠳⣌⡛⡬⡕⡎⡔⢁⠀⠁⠀⠄⠀⠄⠀⠈⠄⠡⠈⠄⠀⠠⢈⡐⢀⠆⣀⠒⠠⢂⠡⢒⡘⢡⠐⡄⢃⠒⢄⠣⠘⡄⡘⣀⠂⢡⠈⢂⠡⠈⠄⠡⠈⠄⡁⠂⠌⡀⠐⢈⠀⠄⠈⡀⠌⠀⠀⠄⠀⠀⢀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠁⠀⢀⠀⠀⡀⠈⠀⠐⠀⡀⠈⠀⠐⠈⠀⠄⠁⡀⠠⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⡀⠀⡀⠀⠄⢀⠰⢠⢉⠳⣧⢘⠻⣷⣾⣾⣞⣣⡝⢦⣙⠶⡝⣞⡴⢂⠀⠀⠂⠀⠠⡀⠀⠀⠌⠠⢁⠂⠀⠠⢁⠰⢈⠐⠠⡈⢁⠢⢁⠂⠤⢁⠊⠤⢁⠊⡐⠌⡡⠐⠄⡐⠈⡄⠌⡀⢂⠡⠈⠄⡁⠂⠄⡁⢂⠐⢈⠠⠀⢂⠀⠄⠀⠐⠀⡀⠄⠈⠀⠀⠀⠀⠀⢀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠈⠀⠀⠄⠀⡀⠁⠀⠂⠀⠄⠁⠠⠈⠀⠄⠂⠠⠀⢂⠠⠀⠁⠀⠠⠀⡁⠀⠌⢀⠡⠐⡀⠰⠀⢈⠢⡑⢎⠤⡙⡞⣧⣙⠶⣦⣍⣛⣏⡽⣣⢮⣝⠾⣱⢊⢆⠠⠈⠀⡀⠁⠀⠀⠀⠌⡐⢀⠂⠀⠐⠠⠒⢠⢁⠒⠠⡁⢂⠢⠉⡔⠨⡐⠡⠌⡐⢌⠰⢠⠉⠤⢁⠒⡀⠂⠔⡀⢂⠁⠂⠄⡁⢂⠐⠠⢈⠠⠀⢂⠀⠄⠂⠈⠀⢀⠀⠀⠀⠀⡀⠀⠁⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠁⠀⠀⠁⠀⠠⠀⢀⠀⠁⡀⠈⠀⠐⠀⠠⠁⠀⠄⠁⠠⠀⢀⠐⠀⡀⠀⠠⠀⠄⠂⠌⠀⠀⠀⡁⠠⠂⠀⢧⡙⣦⢡⠹⣌⡻⢶⣅⠻⠿⣿⣿⣷⣯⣜⣣⢧⣋⣦⠁⠄⠀⡀⠠⠀⠈⢀⠢⠐⡀⠂⠀⠈⠡⠘⡀⠂⠌⠡⠠⢁⠂⡑⠠⢃⠰⢁⠊⠔⡈⠔⠂⡅⠒⣀⠂⡐⢁⠂⡐⠠⢈⠐⠠⠐⠀⠂⡁⠄⠀⠂⠀⠄⠂⢀⠂⠁⠀⠀⡀⠈⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⢀⠀⠂⠁⠀⢀⠀⠠⠀⢀⠀⠁⡀⠂⠀⠄⠁⠠⠈⢀⠐⠀⡀⠂⠠⢀⠀⠀⠀⡀⠀⠄⠀⠀⠀⠄⠀⠀⢳⡍⣖⢫⠖⣤⡙⢳⣽⣻⢷⣦⣝⣻⠿⣿⣿⡻⢿⣿⣿⢶⠀⠀⡀⠐⠀⢀⠂⠡⢀⠡⠀⠀⡁⠆⠡⢈⠐⠡⢁⠂⢌⠠⠑⡈⠔⣁⠊⠤⢑⠨⠑⠄⡃⠄⠒⣀⠂⡐⠠⢁⠂⡈⠐⢈⠀⡁⠠⠐⠈⢀⠁⠠⠈⠀⠠⠀⠈⠀⠀⠀⠀⡀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⡀⠀⠈⠀⢀⠀⠄⠀⠀⠄⠀⡀⠁⠠⠈⢀⠐⢀⠀⠂⠀⠄⢁⠠⢀⠀⠀⠀⡐⠀⢂⠑⠨⠀⠀⠠⢸⣾⣾⣿⣿⣷⣯⣷⢦⣙⠿⣾⣶⣾⠿⢶⣶⣽⣳⣦⡴⣠⢂⠀⠀⡀⠀⠀⠌⡐⢀⠂⠀⠀⡐⠈⠄⠡⡈⠔⠠⢁⠂⠌⢡⠈⠆⡄⠣⡈⠆⡡⢉⠢⢁⢊⠡⢀⠂⠄⡁⢂⠐⡀⠁⢂⠠⠀⠐⠀⡁⠠⠀⠂⠀⡁⠀⠀⠂⠁⢀⠀⠁⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠠⠐⠀⠀⠀⠂⠁⠀⠠⠀⠈⢀⠠⠀⠀⠄⠁⠠⠀⢀⠂⠀⠌⠀⡐⠀⠄⠀⢂⠀⠀⠀⠈⠀⠨⠀⠀⠐⠀⠀⣿⣿⣿⣻⡿⠿⠿⠿⡿⣿⢿⡿⡾⢿⡿⠿⢿⣻⠭⠙⠁⠁⢀⠀⠄⠀⠀⠂⡐⠠⢈⠀⠀⡐⠉⠤⢁⡐⢈⡐⠄⠊⢌⠠⠘⡠⠌⡐⢡⠘⡄⢃⠜⢠⠂⣂⠡⢈⠐⡀⢂⠐⠠⠁⠠⠐⢈⠀⠐⠀⠠⠐⠈⢀⠀⠈⠀⠠⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⡀⠐⠀⠀⠂⠀⠐⠈⠀⠀⠄⠁⠠⠈⢀⠐⠀⡐⠈⢀⠐⠀⡐⠈⠐⡀⠐⠀⠀⠈⠀⠂⠀⠀⠂⠀⡀⠈⠛⠿⠵⠀⠀⠀⠀⠀⠀⠀⠀⠀⡀⠀⣀⠠⢀⠠⠀⠐⠈⠀⠀⠠⠀⠀⠀⠄⡁⢂⠀⠀⠄⢃⠰⢀⠰⢀⠐⡈⠔⠂⠌⣁⠢⠘⣀⠃⡌⠰⣁⠊⡄⢃⠄⢂⠂⡐⢀⠂⠌⡀⢁⠂⢈⠀⠠⠁⠐⠀⠠⠈⢀⠠⠈⠀⠀⠄⠀⠂⠁⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⢀⠀⠀⠀⠀⠂⠀⠈⢀⠀⠈⢀⠠⠈⢀⠐⠀⠐⠀⠠⠐⠀⡀⠂⠠⠀⠁⠄⠂⠁⡐⠀⠀⠀⡀⠁⠀⠀⢀⠀⠀⠀⡀⠀⠀⠀⠐⠀⠀⠂⠈⠀⠀⡠⢌⠣⣍⢢⡁⠀⠀⠀⠐⠀⠀⡐⠈⠠⠐⠠⠀⠀⠌⡀⠆⡈⠐⠠⢈⠐⡈⠔⠡⡀⠆⢡⠐⠌⡐⠡⢄⠃⡌⢂⠌⠄⠒⡀⠂⠌⠠⠐⠀⠄⠂⡀⠁⠄⠈⢀⠐⠀⡀⠀⢀⠐⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⢀⠀⠀⠀⡀⠈⠀⡀⠈⠀⡀⠀⠈⠀⡀⠐⠀⠠⠈⢀⠈⢀⠐⠀⠠⠀⠁⠄⠁⢂⠈⠄⠀⠂⠌⢠⠀⠀⠀⠠⠀⠀⠈⢀⠀⠀⠀⠀⡀⠀⠀⠀⠀⠈⠀⠀⠉⠆⢁⠒⠀⢀⠈⠀⠀⠠⠀⠀⠠⠀⡁⢂⠀⠀⢂⠁⠢⢈⡐⢁⠂⠰⠐⡈⠰⢀⠊⢄⡘⢠⠡⠑⣂⠱⡐⠌⠰⢈⠐⠠⠁⠌⠠⢁⠈⠄⠂⢀⠂⠀⠁⡀⠀⠂⠀⠄⠀⠀⠀⠀⠄⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⢀⠠⠀⠀⡀⠁⠀⡀⠁⢀⠀⠐⠈⠀⠐⠀⡀⠂⢀⠈⠀⠌⠀⠄⢁⠠⠀⠂⠁⠄⠂⡀⠌⠁⠲⢄⣠⣀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠠⠀⠀⠄⠈⠀⢀⠐⠠⠀⠀⠂⠌⡁⢂⠐⠠⡈⢁⢂⠁⡒⢈⠐⢂⠰⢀⢊⠡⡐⠰⢈⠌⣁⠂⠌⠠⠁⠌⡐⠠⢈⠀⠌⡀⠠⠁⡀⠄⠐⠈⠀⡀⠂⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⢀⠀⠁⠀⠀⠁⠀⠀⠠⠀⢀⠀⠁⡀⠀⠂⢀⠈⢀⠈⠀⠄⠀⠂⢀⠠⠁⠐⠈⢀⠠⠀⠂⢁⠈⠠⠐⠀⠄⠡⠀⢂⠀⠠⠉⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠀⠀⢀⠂⠐⠀⢁⠀⠠⢁⠂⣀⡈⠐⡀⠂⠌⡐⠠⢁⠂⢡⠐⡈⠰⢈⡐⠌⠄⢢⠑⠨⠄⢒⠠⠌⡀⠃⠌⡐⠠⠁⢂⠈⠄⠠⠐⠀⡀⠄⠂⠈⢀⠀⠀⠄⠈⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠂⠈⠀⠐⠀⠠⠀⠀⠄⠀⠐⠀⡀⠠⠀⠠⠈⠀⠄⠁⡀⠠⠀⢁⠈⠀⠄⠂⢁⠠⠀⢁⠠⠁⡈⢀⠂⠠⠈⠄⠂⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠠⠀⠊⠄⢠⠀⠀⠁⠄⠀⠀⠈⠡⢀⢁⠢⢀⠁⠂⠌⡀⠂⠤⢁⠂⠰⠈⢌⡀⠎⣁⠊⢄⠒⠠⠁⠌⡐⠠⠁⠌⡀⢂⠠⠁⠄⠂⠀⠄⠂⠁⡀⠠⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠠⠀⠈⠀⢀⠠⠐⠀⠠⠀⠐⠀⡀⠈⠀⠄⠀⠄⠀⡁⠀⠂⢀⠂⢀⠐⠀⠄⠐⠈⡀⠐⠠⠐⠈⠠⠀⡁⠄⢀⠂⠁⠄⠂⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠁⠀⠀⠀⠠⠁⠌⠄⠀⠠⢁⠂⠀⠀⠀⡁⠂⠄⠂⠄⠌⡈⠐⠠⢁⠂⠤⢈⡁⠎⢠⠐⡈⠤⠘⡠⢈⠡⠌⡐⠠⠁⠌⡐⠠⠀⢂⠐⢀⠂⠁⡀⠂⠁⠀⠄⠀⡀⠁⠀⠄⠂⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⢀⠠⠀⠀⠀⠄⠀⠐⠀⡀⠄⠐⠀⡀⠂⠀⠂⠀⠄⠁⠠⠀⠂⠠⠈⡀⠌⠀⡐⠈⡀⠂⢁⠂⡁⠄⠂⠄⠂⡈⠄⠠⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠐⠀⠀⠀⠀⠈⠀⠀⠐⠀⠀⠄⠁⠄⠂⠄⠀⠂⠄⠡⢈⠐⡈⠐⠠⢉⠐⠠⢈⡐⠄⡐⠨⠄⢂⠅⠢⡑⢠⠁⠢⠐⠠⠁⠌⡐⢀⠂⡁⢂⠈⠠⠐⠀⠄⠂⠁⡀⠂⠀⢀⠠⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⡀⠠⠀⠀⠀⠀⠐⠀⡀⠈⠀⠄⠀⠄⠂⠀⠄⠀⡁⠠⠁⠠⠈⠀⠄⢁⠀⠂⠠⠀⡁⠄⠂⠄⠡⠀⠂⠄⢂⠁⢂⠁⠄⠂⡁⠐⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠁⠀⠀⠀⠀⠈⠀⠀⠠⠀⠂⠀⠠⠈⡐⢈⠀⠀⠈⠄⡁⢂⠐⠠⢉⠐⠠⡈⠄⠡⠐⡐⡈⠔⡈⢄⠊⡡⢐⠡⠌⢡⠈⠡⢈⠐⡀⢂⠐⠠⢀⠂⠁⠄⡁⠄⠂⠁⡀⠄⠁⡀⠀⠐⠀⠁⠀⠀⠂⠀⠀ Michael Jackson * First Onchain Collection 9/12 * Legends @ BTC⠀⠀⠀⠀ - 10/12 tx 74f2b9b61d2d79bf0f3ba1f13088fb1c56cf308202afd508b6b88fe4e8b99c74
- Pepe the Frog themed collections:
- "Hiddenpepe" collection. These are present inside HTML comments, and don't show well on ordinals.com. But you can see them by inspecting the HTML code, e.g. at: ../view-source:https://ordinals.com/content/a66a54878d428fc7bdf5758ea3bf2ebe1c76750043c22dc6ff05d7cb5a0c0a37i0.By looking at the short JavaScript code, the page seems to select one plain background color at random, but it didn't seem to work very well, we always get the same color?
- 02 tx 747b4a8a8b112ee1ff1d88982fcad4ea517ad5b079eb8da44bd4dae8a617c48d
- 03 tx a66a54878d428fc7bdf5758ea3bf2ebe1c76750043c22dc6ff05d7cb5a0c0a37
- 04 tx 4353581d19da64ada15a0ff9e8ded380eb5778d036c607e9055d0eb85c10ed65
- 05 tx d45422e6ce033df0895ce3945ce26b25aa4d95ecda835a2504dcaaf6352c20c8
- 06 tx 7650ad0da7f563bd882cd28f88654ac7484b97e63426fda1667bf15da65aad0e
- 08 tx e104fb9c34e75418385f04eb7d92ed16afd45cc244923f5807ed4ca65c8f010f
- 09 tx a5256054de9f80593b9b347072ce6d4a159d70f811de38a9d4a027a229d6c803
- "Pistol Pepe": these simple browser games contain an ASCII art as an HTML comment. The are signed "www.twitter.com/tewz1 tewz.cent.co/" (twitter "Account suspended" as of April 2024).
ANSI art. These can only be viewed on a terminal:
- tx 2a319ec83d8e93cd8003a8d087514a0f775b7314128fbdf4d59aad2f9664ac04: Pepe the Frog with lots of terminal blink on the background, quite cool
- tx 2a96eb44afce6028cbb6c1a639c9e93cf40a58e2bdc97f9d642fa0ec5713507a: "incoming call Satoshi Nakamoto" has the image of a man in suite with some dark terminal colors, pretty cool
ASCII porn:
- tx de57a32fcae4c20c16ebb9782ecc550f199e2f7d3a2149188945b21fcff99177; man drinking with while pulling out his huge dick
Misc:
- tx 9089c4fac49593628e1334bbfe94080819bdac67eac18c9ffece5a2bc235a380: wizard taking a shower
- tx fdf9b82e3177c5404f8251ad26460788fc8b29cc4cbd4951ea5e8438dcce9631: and tx 2031b40ccb3944822be709c9a41f38e10ddf13c577b3f2c4d2046ac73020f6f9 middle finger Unicode art. Both marked "THE MIDDLE 1/15".
Figure 4. THE MIDDLE 1/15. Screenshot taken from ordinals.com/content/fdf9b82e3177c5404f8251ad26460788fc8b29cc4cbd4951ea5e8438dcce9631i0. - tx ed3bd1a0cd8a18743acfd7162649a43b69f25a540fbfe6a2352a612ebfb381e6: JavaScript that generates a demoscene ASCII art animation that looks like a rotating thing
- tx 78240e4691c7f75311a03125567f1e44fc0049db611f0ac554f04f8790e28e24: cute cartoon dog giving wearing a headband and giving thumbs up. The Chinese subtitle reads:which Google Translate translates as:
买海豹胆小鬼
TODO context. Sample hit at: twitter.com/0xTenkito/status/1612939684816031746A coward who buys seals
- tx 3a474f540c1917817fba51d2f9fd647887c8c3cd9687eb8d34ab6787c9e8a7fa: ASCII art of mysterious man typing on his laptop. Satoshi comes to mind. The man's hat contains the following Korean characters;which Google Translate translates as:
진실로같이가요
Let's go together truly
- tx 18b7728f32ff27d410e57e289bca7b8c2bdf7c30a1c572a41acc1a8ff576b6ab: "I Want you BTC Maxis, Ordinal Army Enlist Now"
- tx 2fc46b52e3ab7a1053c4c65a4dc3af6bb7e51eb15cb988294af3a203ad254eed: contains an ASCII art of an Iron Man-like mask with text:But hopefully/presumably the author meant Steganography and not encryption right? Code "Your free GrrCon ticket" comes to mind.
Did you know that within ASCII art an encrypted msg can be inside? All you need to do is decode it. Hence a pictureworthsthousandwords.
- tx 6d1d99ed05a152d59fdef4eb26a4a07a4f81dcd945249639af272504b4e70d27: Bitcoin whitepaper as Markdown, but with some great Unicode art rendition of the diagrams!
┌─────────────────────┐ ┌─────────────────────┐ ┌─────────────────────┐ │ │ │ │ │ │ │ Transaction │ │ Transaction │ │ Transaction │ │ │ │ │ │ │ │ ┌─────────────┐ │ │ ┌─────────────┐ │ │ ┌─────────────┐ │ │ │ Owner 1's │ │ │ │ Owner 2's │ │ │ │ Owner 3's │ │ │ │ Public Key │ │ │ │ Public Key │ │ │ │ Public Key │ │ │ └───────┬─────┘ │ │ └───────┬─────┘ │ │ └───────┬─────┘ │ │ │ . │ │ │ . │ │ │ │ ──────┼─────────┐ │ . ├───────────────┼─────────┐ │ . ├──────────────┼─────────┐ │ │ │ │ │ . │ │ │ │ . │ │ │ │ │ │ ┌──▼─▼──┐ . │ │ ┌──▼─▼──┐ . │ │ ┌──▼─▼──┐ │ │ │ Hash │ . │ │ │ Hash │ . │ │ │ Hash │ │ │ └───┬───┘ . │ Verify │ └───┬───┘ . │ Verify │ └───┬───┘ │ │ │ ............................ │ ........................... │ │ │ │ │ │ │ │ │ │ │ │ │ │ ┌──────▼──────┐ │ │ ┌─▼────▼──────┐ │ │ ┌─▼────▼──────┐ │ │ │ Owner 0's │ │ Sign │ │ Owner 1's │ │ Sign │ │ Owner 2's │ │ │ │ Signature │ │ ...........─►│ Signature │ │ ...........─►│ Signature │ │ │ └─────────────┘ │ . │ └─────────────┘ │ . │ └─────────────┘ │ │ │ . │ │ . │ │ └─────────────────────┘ . └─────────────────────┘ . └─────────────────────┘ . . ┌─────────────┐ . ┌─────────────┐ . ┌─────────────┐ │ Owner 1's │........... │ Owner 2's │.......... │ Owner 3's │ │ Private Key │ │ Private Key │ │ Private Key │ └─────────────┘ └─────────────┘ └─────────────┘ - tx e643b2a25b6df9c1d5b0fad7168677a71b96544707efab16f0cf0266981cbe53: "Dear Luke Dashjr, here’s why I want to join the @TaprootWizards"
- tx 6987171da8a07b365686f3ec25ccc08f731943eecbbebed0c9b0df63b58d69fe: classical painting of a nude female model marked "By Johnny Dollar J$"
- tx 8ae6534ba41e305fedf068696111d5445e90c48cbd18081503e831399f1a11fb: HTML of monkey face with bow tie and pink cheeks. Cute! The HTML code is also arranged in a monkey like pattern.
- tx d6c60f0efc9f3155712775c2a0f4e1d805f000fc50763c440cb575f252de371d: also seen at: www.h17n.art/: HTML with the busts of a few people who strongly criticized Bitcoin: Warren Buffet, "Paul Krugman", "Christine Lagarde" and "Peter Schiff":
., .., , ,.., *,. ,***/,..,/...,. ,.//(////*/#((//(##%#* . . . ,.**&&&&&%#%#%%%%%%###%%%%(//*,. . . ..**/%&@&%&&@&@&@&@@&&&%%%%#%%&%%####/ ... .,,.,(//(&&&&&&&&&&&&&@@&&%#%&(%%##%#%##%%%#((#(* ., /*(*(%&&&&&&&&&&&&@@@&@&&%%%%%%##((########(#((/(//,. * . .,(((%&@&&&@&&&&&&&&&&&@&&&%%#%####%##(((((((#(###((/*****.../ . .,,(%&&&&&&&&&&@@@@@@@@&&&%%#%######(#%#(#(###(((((#((#(#(((//##//*,,, . ,, %%&%&&&&@&&@&@&%#@########%##(((((((#((((#(((#((((((#(#####(//(##(#((// *.. ,.(%&&&&&&&@&&&&%&%%%%&&%&%%%%%%%&&&%%%%%%%%########((#######(#((/(((#%(#(((*. * **%&&&&&&&&%%@%%&&&&&&&&&&&&&&&&&&&&&%%%%%%%%##%##############(#(/##((####(((/,. * .#&&%&&%@&&%&&&&&&&&&&&&&&&&&&&&&&%%%%%%%%%#%%%%%#######((#####%#(//(((#((##((/((, , .%&%&&%&&%%&&@&&&&&@&&&&&&&&&&&&&&&&%%%%%%%%##%%%##(####(##(#(##%(((*(((###(#(/((/((#, .,&%%&%&%##&&@&&&&&&&&&&&&%&&&&&&&&@&&&&%%%%%%%%#######(####(((####/#/(/(#(((##(/(((((#(/* .#%#%&&&#&&&&&&&&&&&&&&&&&&&&&&&&&&&&&%%%#%%%%#######(#####(((##(#(/%/(//(#///(((/(((((((/. *(#%&&%%%%&&&&&&&&&&&&&&&&&&&&&&&&&&&%%%%%#%%#####(##((#((((((((####(/((/((##/((((//(/((((/* ,###%%##%%&&&&&&&&&&&&&&&&&&&&&&&&&&%%%%%#########(#(((((((((((((%##(///*/((#/(#/((/(///(/**. */#%%%%%&&&&&&&&&&&&&&&&&&&&&&&&&&&%&%#%%#%#########(#(#((((/((//(//#(#(/((/*//(((#(/*,,**** *##%%%%%&&&&&&&&&&&&&&&&&&&&&&&&&%%%%%%%#%%########((((((((///(##%(((#/(##,*(/#//((/****,... *(#%%%&&%&&&&&&&&&&&&&&&&&&&%%%&%%%%%#%#%#%%%#%###(/(((/(//(((/%(((/(////*/**//*****,***, ,#&&%%&%%&&&%&&&&&&&&&&%&%%%%%%#%%%%&%&&%&&%%%%###(((/////((###(%(/*/*,/,*,,,******,,,* *.&%&&&&&&%%%%%%%%%%%%%%#&%%%%&%&&%%%%%&&#####((##((((////(/###%(#//.**,***//,....,*. *%&%&&&&&&&&&%#%##%####(%%%&%&&&&%%(#(%%###(#((((/(////(((((/**..,,,**,**,,..,,,,,,* **///(%%&%#%####((#%%#(/((#/(,/(**//**,/%**///(#(/((/**,*.*%((//*/*/,***,,,,,***,,*/ *,///*/((/**,*,**#%/*,/%&&##/**,***,,,*//((((((///.*..*.,.*(////*//*//**(***,,**////***(* *./* ..##(*,,,,, ,,*///##*,*/*,.,*,,,,.**.. .,..*,*/*#((///////////(******,,. .*****// ((.. (((###((###(//,*(#(/*/*//*//(//(((((((#####(#,/%#((///////////******//,,.,,***/* .*.. %%%&%%%%%%####,%&@&%#,/*###(##((###%%%%###%#%./#((//(//******/*****////,**//((/. .#,..%%%%%%%%####%%%&&&%%#(*,/#%%%%%%%#####%%%%&&%.#((///////***********////,**/((*, ,@,#%%%%%%&&&%%%&&&&&%#####(*(#%&&&&&&&&&&&%&%/#///////***************/*/**/(/*./, ((,/(%%###/*/%&&&&%%##(##%%%%//#%#((##/#//////(((((////****************,,,***(/ .#%%%&&&&%%(%&&&&&&%##(#%##%((#%&%%%&&&&%%%%###((((////*********///***(/////(( #%%&%&%%%#%&&&&@&%%%###%%##(#(*,//###%#######((((//////****//*///****(//((#(, ,###%%#(//%%%%%%%#(//(((///**,./(//*/(((((((((//////**/*****/********.//((/* /((((/*,.///(///*,,. ..,*((##((/**//////***,,,,**************,,.,,,,*/ ////*,.,(##(/*,, .,*///(##(((//////(***,,,,..,*////******,,,,,,,,,,////. ((**,,,*/(((((//**///((((((((//////******/*,//(//(///****,,,,,,,,,,*////*,. (#####((//*/((((((((((////*/*,,,,,,,**//##(((////(/*,,,,,,,,,,,,,//////*... (#%%%%#(##/*/(///***,,,,.. .,,**/**/#%%##(///*///*,,,,,,,,,,,*///////,,*. .##%%##%#%###(//////#%#(###(/////(#%#%##(///**//*,,,,,,,,,,,////((//*** .. .... (###%##((#####(#(((((((/*////##%%#(##(///*,*//,,,,,,,,,,*/////((//// . .. .. . .... (##%%%((((#(((/(((/((((//(((#(%##(#(/***,*//,,,,,,,,,**/////(///(. . ......... .. .... .......,#%&%#((((((#/(((#(((//###%%((#(/((*,,,***,,,,,,.,****///////(/ .......... ............. .,...,......(%%%%%#%%%%%%%####%%#%%%###(//**,.,,*,,,,,,,,,****///////(( .. ... .......... .............. .............../%%%#%##%######%###%###////,,,,...,.,,,,,.**,**/////((((. . ............... .............. ...........,,......############(##(#(/****,,,...,.,,,,,,,*,,,**////((//* ................. ............... ......................((#((((/////***,,,,.,,.,.,,,,,,,,,,,.,,*///((///* ..................... ................ .............................,*,,,,,,,,,,,,,,,,*,,. .,,,,,,,*/((((/*** ...................................... ............................ .#&%%%%%%#/,.,,... .,,,,,,,**/((#((/**/,........................ ................. ............................ .(&&&%%%###(*,**/*,,,,,,***/((###(*////.......................... ................. ............................../&&&#* . . ////////(((##%#/////(........................... ...........,...... ............................. ,#,,,,,/ /, ., ,##(####%%%#(((/*/#/............................ ...,.............. ............................ *#****..#, /*. (*, (%%%%##((((///#%(.............................. .................. ............................./%&///*...#*.*(/ .*/.##(((((((#%%&&................,.............. ................... ............................/%@@@#*..,.. . , ((((##%%&&&,....................... . .............,.......... ...........................,/%@@@@%/,..,. ,. . *#%%#%%&&&&&%...................... ........................,..... ..........................,/%&@@#* .#((.....* ,(%&&&&&&@@@@@...............................,................. ...... ..........................,/#&@@*./#,..(/*.*. ,%@@@@@&&&@@@(......,.,...,....,...........,..,........................ .....................,....,/#&&@(*...&(*,...,#(*&@@@@@@@@@@...................,..............,.......,................ .........................,/#%&@*##(#.,,...%(*..(@@@@@@@@&.....,............. ...,.............................,....... .........................,/#%&@%.#*/*..,#%...(*,%@@@@@&&#.,................. . ............... ........................
Small art as part of an ad for something like a collection or service:
- tx e00318a4c0769f641ee62cfd8d55ac671d987244762a34895cc29c6142964dd4: ordinal bears collection header
- tx b0f140eddbe03c98d982524d81ab5beecfee3e135bc658173e38ffd675ca9f08: 999 club
- tx 29a4d4fb8ea570a5e6520c0c6d56bf44d00e5c0028b33f57eb1d2bbda4c467e1: "Bitcoin Bots"
- tx 86747b2b5118dd3c3911f8506818af7f6bf102ecd35f854d796021466bc4b548: "Bad Bunnies" badbunnies.xyz/ ad
- tx 0fc35f856bfd43e0c939100d9a21beccdac8264db81c0927cb681dcd22628dd6: EspressOrdinals
- tx 65bded5452fb0d158da19652afbee41cbc50c01513f3a50cf3540a059ace6e8a: ORDINALIENS twitter.com/ordinaliens
- tx 72c5d96279012faed9c464e75877186abd21c0fe6f5f00e244a7bd606d515b26: inscribeords.com "Inscribe Ords", an inscrption service
- tx 99e90c6f741921cc6740c4b402dbd69f40d3686be06d18aab39561871ad22b16: "immordal" Unicode art
Our algorithm is designed to give a rarity score to tweets based on their visibility and interaction. We take into account metadata such as views, likes, and retweets, and assign a grade to each category. These grades are then used to determine the rarity score of the tweet. We believe that this system will create a more just and equitable online community, where individuals are rewarded for meaningful contributions, rather than for clickbait or sensationalism. - tx 61ab46f60128c36a0dd9f9503711d38eef8737e88e6b78cad7365a54fdac7aa4: twitter.com/minidogeart "Ordinal Mini Doges"
- tx 9402c3c7f837353e68fae663027e7251b52820bd10dfd3fb57779c3c4bcb291a: Bitkoingz @BitKoingz
CSS flex Updated 2025-07-16
Other examples include:
- css/flex-fill-vertical.html: minimal setup for a editor: docs.ourbigbook.com/editor
That example calculates and displays the final widths via JavaScript, making it easier to understand the calculations being done.
react/ref-click-counter.html Updated 2025-07-16
Dummy example of using a React
ref This example is useless and to the end user seems functionally equivalent to react/hello.html.It does however serve as a good example of what react does that is useful: it provides a "clear" separation between state and render code (which becomes once again much less clear in React function components.
Notably, this example is insane because at:we are extracing state from some random HTML string rather than having a clean JavaScript variable containing that value.
<button onClick={() => {
elem.innerHTML = (parseInt(elem.innerHTML) + 1).toString()In this case we managed to get away with it, but this is in general not easy/possible.