CIA 2010 covert communication websites Searching for Carson Updated 2025-07-16
Edit: Carson was found Oleg Shakirov's findingsby Oleg Shakirov:
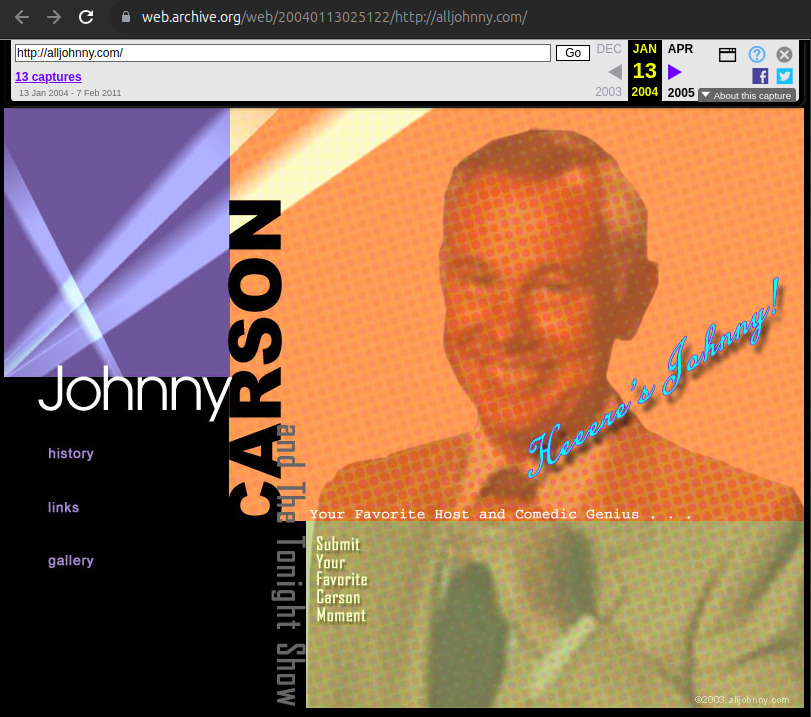
alljohnny.com, communicated at: twitter.com/shakirov2036/status/1746729471778988499, earliest archive from 2004 (!): web.archive.org/web/20040113025122/http://alljohnny.com/, The domain was hidden in plain sight, it was present in a not very visible watermark visible in the Reuters article screenshot! The watermark was added to the CIA to the background image, it is actually present on the website. In retrospect, it was actually present at on the expired domain trackers dataset, but the mega discrete all second word made Ciro Santilli miss it: github.com/cirosantilli/expired-domain-names-by-day-2015/blob/9d504f3b85364a64f7db93311e70011344cff788/07/05/02#L15722004 Wayback Machine archive of alljohnny.com
. What follows is the previous
The fact that the Reuters article has a screenshot of it, and therefore a Wayback Machine link, plus the specificity of the website topic, will likely keep Ciro awake at night for a while until someone finds that domain.
Some text visible on the Reuters screenshot:It is unclear however if this text is plaintext or part of a an image.
Johnny Carson and The Tonight Show
Your Favorite Host and Comedic Genius
Submit Your Favorite Carson Moment
Heeere's Johnny!
Holy crap, the "Here's Johnny" line from The Shining (1980) is a reference to Johnny Carson: www.youtube.com/watch?v=WDpipB4yehk, www.youtube.com/watch?v=aYnyPAkgyvc, Ciro never knew that... but every American would have understood it at the time.
Some failed attempts, either dry guesses or from DNS grepping dataset searches:
- johnnycarson.com: official
- johnnycarson.net: fan site: web.archive.org/web/20010501225614/http://johnnycarson.net/
- johnnycarsontonight.com
- carson-johnny.com: legit
- johnnycarsonshow.com: web.archive.org/web/20110208005558/http://johnnycarsonshow.com/captcha/index.php?d=johnnycarsonshow.com your IP has been blocked
- tributetojohnnycarson.com: only one archive web.archive.org/web/20180805132430/http://tributetojohnnycarson.com/
- bestofjohnnycarson.com: web.archive.org/web/20130525035938/http://bestofjohnnycarson.com/ Lived past 2013.
- bestofjohnny.com/: web.archive.org/web/20130506011824/http://bestofjohnny.com/ empty
- johnnycarsonvideo.com: dead early 2000s web.archive.org/web/20130605152818/http://johnnycarsonvideo.com/
- johnnycarsontv.com: web.archive.org/web/20230000000000*/johnnycarsontv.com
- thejohnnycarsonshow.com: web.archive.org/web/20230000000000*/thejohnnycarsonshow.com
- carsonsbest.com: web.archive.org/web/20230000000000*/carsonsbest.com
- johnnycarsonfans.com: web.archive.org/web/20230000000000*/johnnycarsonfans.com
- web.archive.org/web/20230000000000*/carsonified.com
- night:
- amazing:
- johnnyamazing.com: broken archives: web.archive.org/web/*/http://johnnyamazing.com/*
- carson
- johnneycarson.com: no archives
- johnnycarson.co: no archives
- johnnycarsons.info
- johnnycarsons.com
- johnnycarson.org
- johnnycarsonsdesk.com
- johnny-carson-video.com
- johnnycarsondvd.org
- johnnycarsondvds.org
- johnnycarsondvd.net
- johnnycarsondvd.tv
- johnnycarsondvds.net
- johnnycarsondvds.tv
- johnnycarson.tv
- johnnyguitarcarson.com
- johnnycarsonmovie.com
- hookedonjohnnycarson.com
- johnnycarsonbook.com
- licensingjohnnycarson.com
- johnnnycarson.com
- johnnycarson360.com
- koalajohnnycarson.com
- johnny-carson.com
- johnnycarsonbirthplace.com
- johnnycarsonbirthplace.net
- johnny:
- heres:
- heresjohnnyfilm.com: web.archive.org/web/20131011115733/http://www.heresjohnnyfilm.com/ legit
- hereisjohnny.net: no archives
- heresjohnnyradioshow.com: web.archive.org/web/20130509042107/http://heresjohnnyradioshow.com/, Legit most likely: web.archive.org/web/20140517103512/http://heresjohnnyradioshow.com/
- wherejohnnylives.net: broken archives
- heresjohnny.com: squat web.archive.org/web/20130607145841/http://heresjohnny.com/ Many other TlD like .net, .co.uk
- heeeeresjohnny.com: web.archive.org/web/20130612211448/http://heeeeresjohnny.com/: legit
- night:
- johnnylatenight.com: web.archive.org/web/20150801132622/http://johnnylatenight.com/ Legit broken
- web.archive.org/web/20110208161513/http://www.johnnysnight.com/
- heres:
- johnnycarson.org: squatted past 2013, nothing before
- carsonshow.com: squat: web.archive.org/web/20110224211714/http://carsonshow.com/
- tonightshow247.net: web.archive.org/web/20101226190209/http://tonightshow247.net/: squat
- tonightshow.tv: web.archive.org/web/20141221222442/http://www.tonightshow.tv/: legit
Searching the Wayback Machine proved fruitless. There is no full text search: Wayback Machine full text search, and a heuristic web.archive.org/web/20230000000000*/Johnny%20Carson search has relevant hits but not the one we want.
Another attempt was to search for "carson" on webmasterhome.cn which lists expired domains in bulk by expiration day, and it search engine friendly. It contains most of the domains we've found so far. Google either doesn't support partial word search or requires you to be a God to find it
so we settle for DuckDuckGo which supports it: duckduckgo.com/?q=site%3Awebmasterhome.cn+%22carson%22&t=h_&ia=web Adding years also helps: duckduckgo.com/?q=site%3Awebmasterhome.cn+%22carson%22+2011&ia=web with this we might be getting all possible results. Ciro went through all in 2011, 2012 and 2013 but no luck. Also fuck en.wikipedia.org/wiki/Carson_City,_Nevada and en.wikipedia.org/wiki/Carson,_California :-)
Let's search tools.whoisxmlapi.com/reverse-whois-search for "carson" contained in any historic domain name. 10,001 lines. Grepping those, no good Wayback machine hits for those that also contain "johnny" or "show". Data at: raw.githubusercontent.com/cirosantilli/media/master/cia-2010-covert-communication-websites/tools.whoisxmlapi.com_reverse-whois-search_carson.csv in case anyone want to try and dig...
CIA 2010 covert communication websites Selected screenshots Updated 2025-07-26
This section contains some of the most interesting and a few representative screenshots of the websites found.
We intentionally omit the screenshots already reported by the Reuters article.
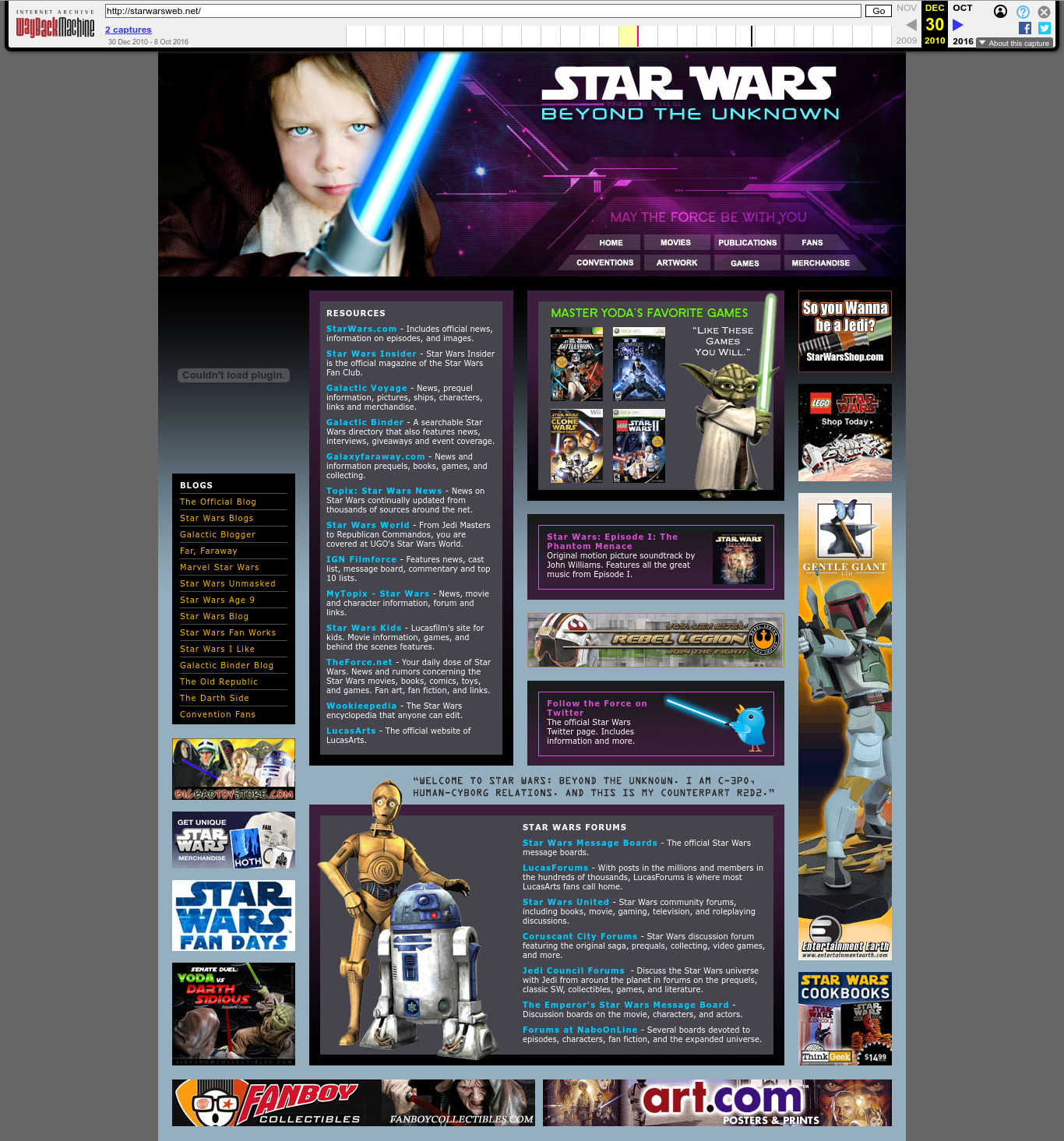
2010 Wayback Machine archive of starwarsweb.net
. The Star Wars one. Clearly branded websites like this are rare, which makes finding them all the much more fun. The Reuters article had two of them (Carson and rastadirect.net), so these were probably manually selected from the full hit dataset, and did not serve specifically as entry points. Most of the websites are quite boring and forgetful as you'd expect.
The subtitle "Beyond The Unknown" may be a reference to the Unknown Regions, an unexplored area of the galaxy in the Star Wars fictional universe.
The photo can still be licensed today as of 2025: www.gettyimages.co.uk/detail/photo/little-jedi-royalty-free-image/172984439. We found it by searching for "jedi boy" on gettyimages.co.uk. The photo is credited to a
madisonwi, presumably an alias based on the location Madison, Wisconsin. Here's a random website about adoption that uses it: www.adoptionadvocates.net/star-wars-adoption-language/ and where it can be seen without the watermarks.It later ocurred to Ciro Santilli that perhaps Reuters chose not to showcase this website because it features the photograph of a minor. But Ciro is sure that that minor is now a handsome young man in his 20's and would find the entire story very amusing if he ever finds out about it!
The images of the droids can be seen e.g. at: www.amazon.co.uk/04-Kampf-Droiden-Superheftig-Jedi/dp/B004TINSW6, a promotional material for a 2008 The Clone Wars television series audio CD and available as transparent PNGs without background in several sources. The Yoda art also seems to come from that show: rpggamer.org/page.php?page=4229.
One can almost picture the contractor who made that site seeing his children watching that show or playing the video game one evening, when a lightbulb popped over their head: tomorrow I'm going to have some fun at work.
In retrospect however, this website was likely a bad idea, since the massive pop culture appeal of Star Wars meant that when The CIA Secretly Ran a Star Wars Fan Site by Joseph Cox was published in 2025 the combination of "CIA" and "Star Wars" on a single sentence produced an irresistible clickbait that amplified knowledge of the fiasco to general public in a way that poor Johnny Carson and Bob Marley could never do. That's why you just can't have fun while working for the secret services anymore.
2011 Wayback Machine archive of alljohnny.com
. Source. Although alljohnny.com is one of the original Reuters examples, we are highlighting this screenshot here because the Reuters provided screenshot is from the extremely early 2004 version of the site, and it is interesting to see how this unique example was later updated in this 2011 version, the only known such case so far. The lack of OPSEC awareness is mind blowing, them reusing a domain like that after so many years in a completely new threat environment and possibly for a new asset.2011 Wayback Machine archive of webofcheer.com scrolled to show Johnny Carson
. Source. This website is a fansite for various comedians. It is the second known reference to Johnny Carson after alljohnny.com, which was one of the original screenshots given in the Reuters article. There must have been some massive Johnny Carson fan among the CIA contractors a that time!2011 Wayback Machine archive of iranfootballsource.com
. The third Iranian football on top of the two other published by Reuters: iraniangoalkicks.com and iraniangoals.com! Admittedly, this one is the most generic and less well designed one. But still. They pushed the theme too far!
The goalkeeper can be seen at: www.pixtastock.com/illustration/7323632.
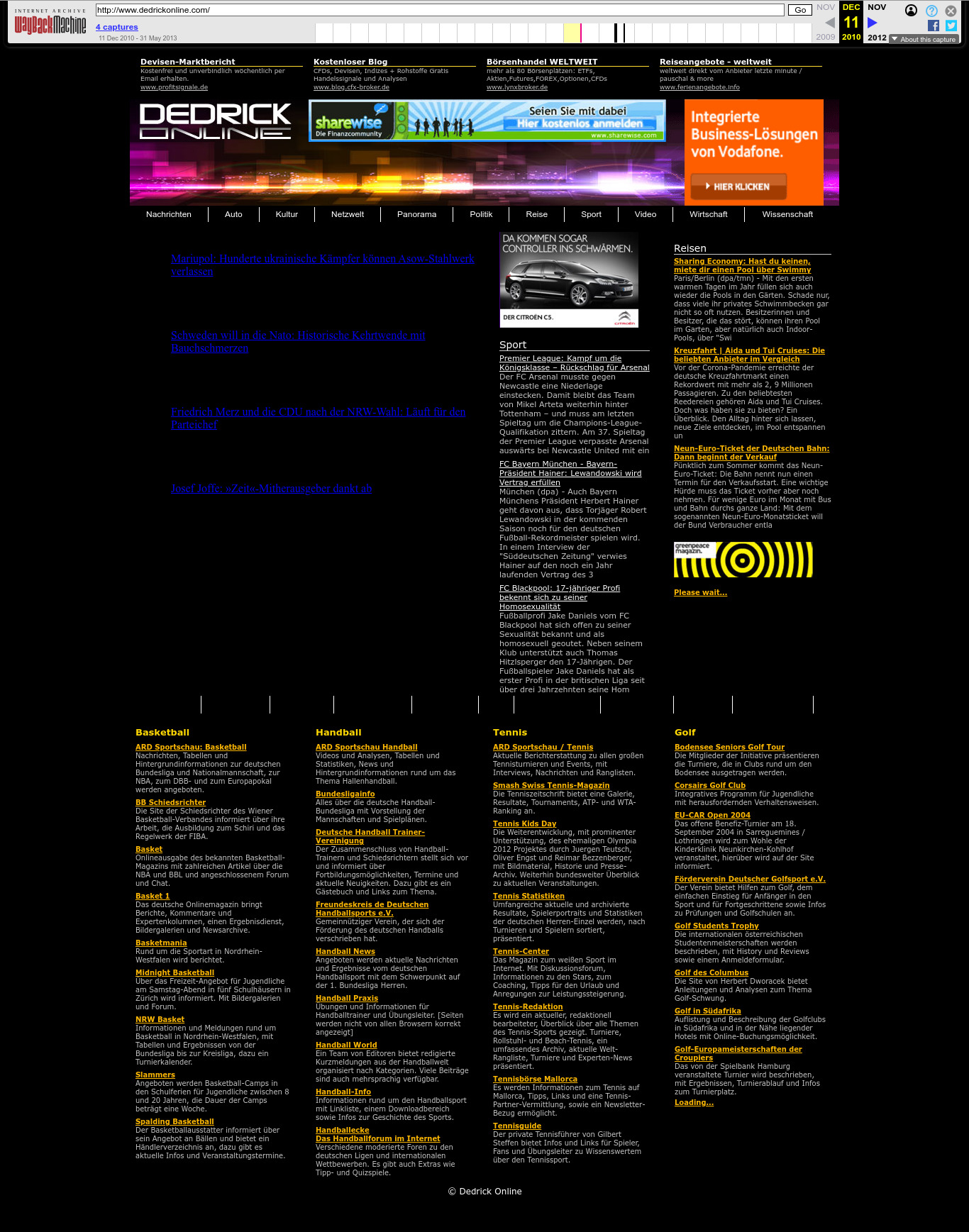
2010 Wayback Machine archive of dedrickonline.com
. The German one.
The CIA has had a few Germany espionage scandals in the 2010s:
- 2014 www.bbc.co.uk/news/world-europe-28243933: a German Intelligence Agency agent was arrested for spying for the CIA
- 2021 www.reuters.com/world/europe/us-security-agency-spied-merkel-other-top-european-officials-through-danish-2021-05-30/ U.S. spied on Merkel and other Europeans through Danish cables
- 2020 www.dw.com/en/how-the-uss-cia-and-germanys-bnd-spied-on-world-leaders/a-52358527 it was revealed that Germany and the USA had an agreement to spy on world leaders, notably via compromised Swiss company Crypto AG
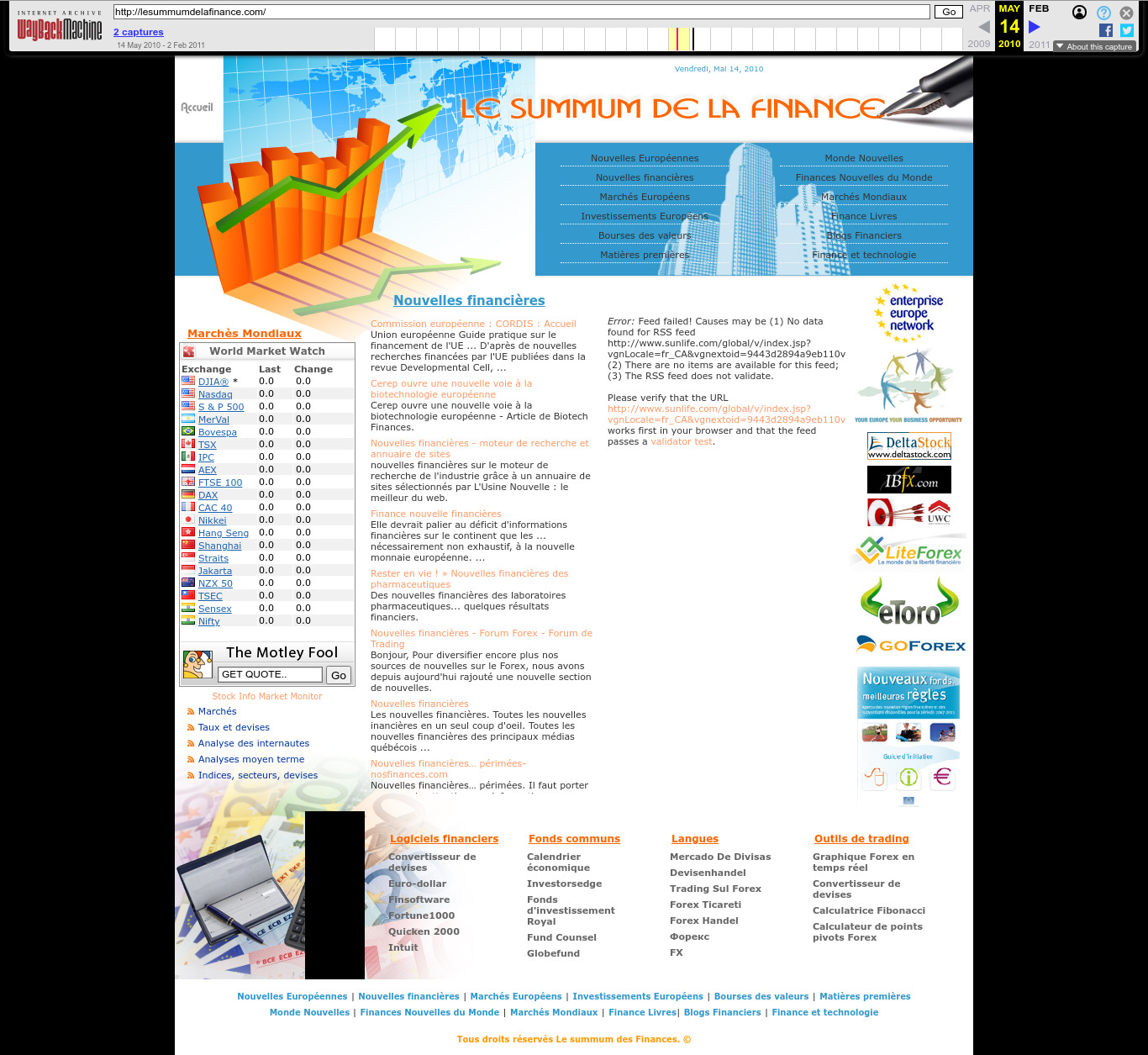
2010 Wayback Machine archive of lesummumdelafinance.com
. The arrow graph is very popular can be seen at: www.financialexpress.com/money/top-4-global-market-risks-for-2024-that-may-impact-your-finances-3346284/ and many other sites. Source unknown.
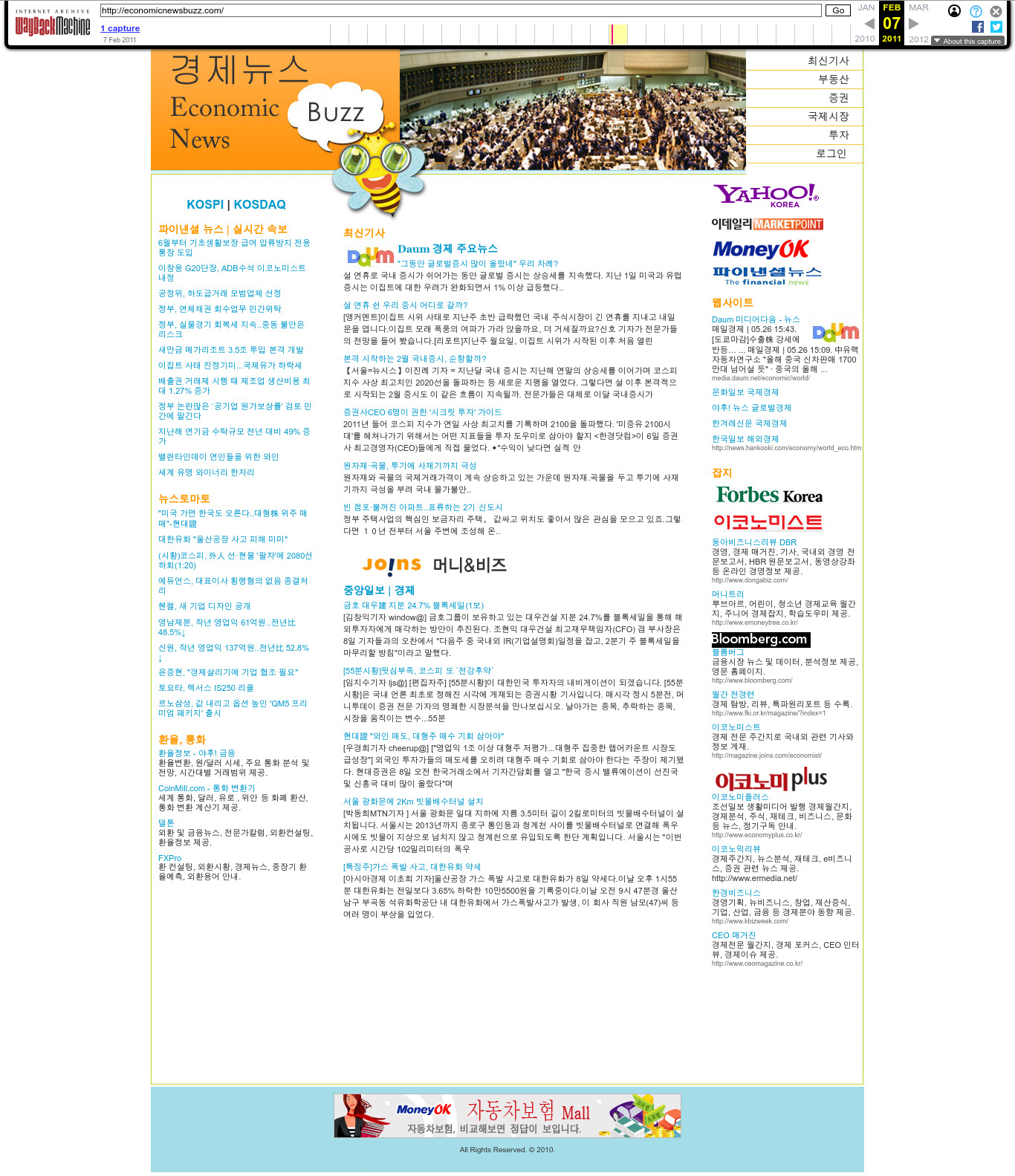
2011 Wayback Machine archive of economicnewsbuzz.com
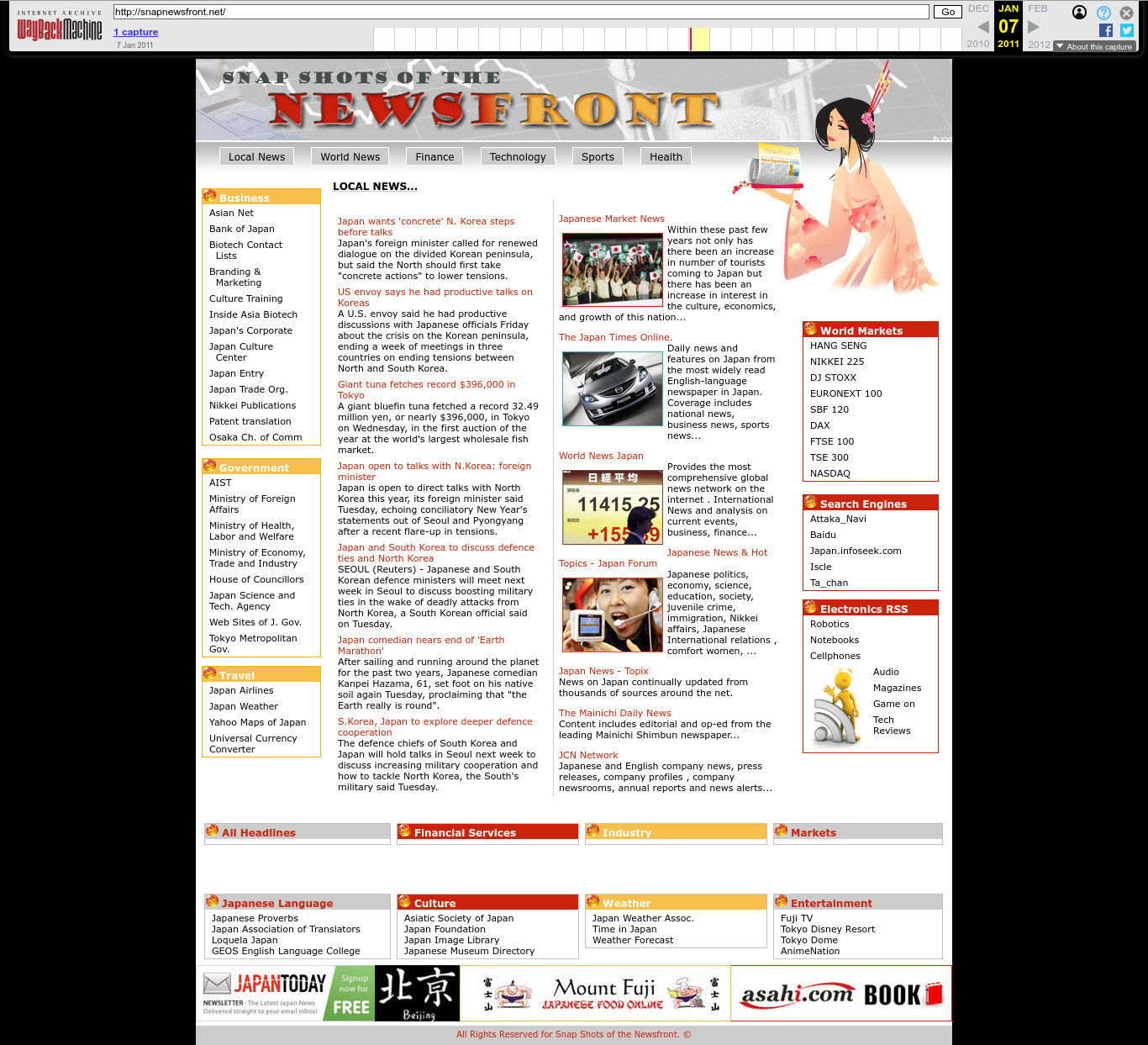
. The Korean one. Love the kawaii style!2011 Wayback Machine archive of snapnewsfront.net
. The Japanese one.
The geisha can be seen at: www.shutterstock.com/image-vector/pretty-geisha-16813348 by Larisa Frelke, assumed accounts: x.com/larra_vit | www.xing.com/profile/Larisa_Frelke
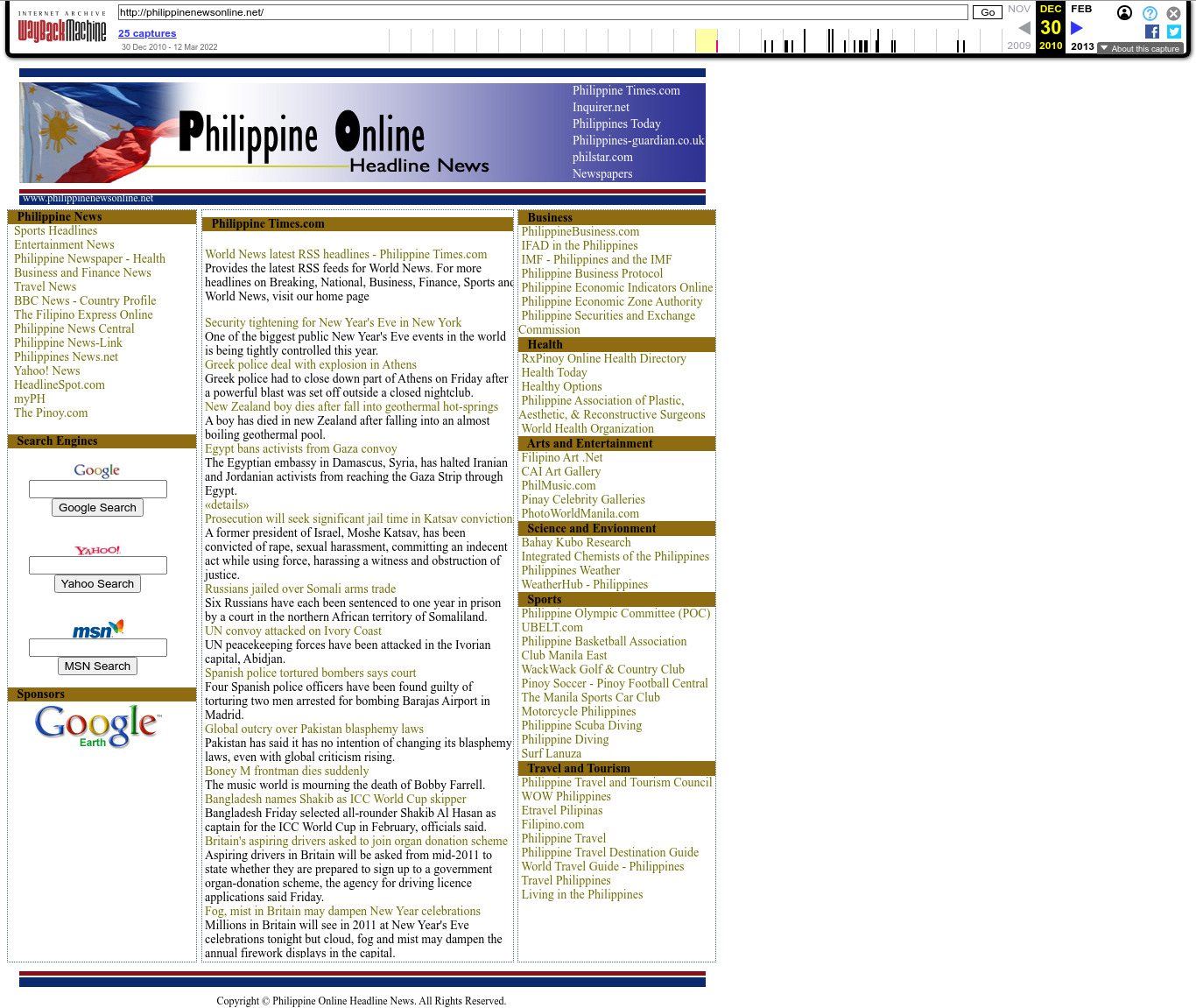
2010 Wayback Machine archive of philippinenewsonline.net
. The Philippine one one.2011 Wayback Machine archive of feedsdemexicoyelmundo.com
. The Mexican one.2012 Wayback Machine archive of easytraveleurope.com
. 2011 Wayback Machine archive of tee-shot.net
. One of the many golf-themed sites. Golf appears to be quite popular over in Langley. It's exactly what you'd expect for a mid-level spook to do in their free time!2011 Wayback Machine archive of nouvellesetdesrapports.com
. 2011 Wayback Machine archive of pangawana.com
. 2011 Wayback Machine archive of recuerdosdeviajeonline.com
. 2011 Wayback Machine archive of theworld-news.net
. 2011 Wayback Machine archive of kessingerssportsnews.com
. 2011 Wayback Machine archive of negativeaperture.com
. CIA 2010 covert communication websites The Reuters websites Updated 2025-07-16
But by looking at the URLs of the screenshots they provided from other websites we can easily uncover all others that had screenshots, except for the Johnny Carson one, which is just generically named. E.g. the image for the Chinese one is www.reuters.com/investigates/special-report/assets/usa-spies-iran/screencap-activegaminginfo.com.jpg?v=192516290922 which leads us to domain activegaminginfo.com.
Oleg Shakirov later discovered that the Carson one had its domain written right on the screenshot, as part of a watermark present on the original website itself. Therefore the URLs of all the websites were in one way or another essentially given on the article.
The full list of domains from screenshots is:
- 2011 archive: web.archive.org/web/20110208113503/http://activegaminginfo.com/. Contains mentions of 2010.
- As of 2023, it seemed to be an actual legit photography website by German (amateur?) photographer Klaus Wägele. Archive: web.archive.org/web/20230323102504/https://www.capture-nature.com/Ciro Santilli actually sent him a message to let him know about the CIA thing in case he didn't, and he replied that he wasn't aware of it.
- 2011 archive: web.archive.org/web/20110201164741/https://www.headlines2day.com/. Dated "Copyright 2009".
fitness-dawg.com: English fitness website.2021 archive: web.archive.org/web/20110207104044/http://fitness-dawg.com/.rastadirect.net: English Rastafari culture website.- 2011 archive: web.archive.org/web/20110203021315/http://fightwithoutrules.com/. Contains mentions of 2009 news.
- 2004 archive: web.archive.org/web/20040113025122/http://alljohnny.com/.
CIA 2010 covert communication websites Timeline of public disclosures Created 2025-05-07 Updated 2025-07-26
The existence of the websites emerged in various stages, some of which may refer to this network or to other closely related communications failure since the published information is sometimes not clear enough.
May 21, 2011: various Iranian news outlets reported that:Iranian sources include:The news were picked up and repeated by Western outlets on the same day e.g.:At this point there were still no clear indications that the recruitment had been made with websites, however later revelations would later imply that.
30 individual suspected of spying for the US were arrested and 42 CIA operatives were identified in connection with the network.
- web.archive.org/web/20110729150642/http://www.presstv.ir/detail/180976.html "Iran dismantles US-linked spy network by Press TV (English, quoted above)
- web.archive.org/web/20110527084527/https://www.mehrnews.ir/NewsPrint.aspx?NewsID=1316973 "CIA spy network dismantled/30 American spies arrested" by Mehr news (Farsi)
- shiatv.net/video/dd6ee2d708a4a6cb2429 "Iran dismantles US-linked spy network" broadcast by IRIB, the main Iranian public broadcaster
- www.latimes.com/archives/blogs/babylon-beyond/story/2011-05-21/iran-intelligence-ministry-claims-to-arrest-30-alleged-cia-spies "Intelligence Ministry claims to arrest 30 alleged CIA spies" by the Los Angeles Times
Quite prophetically, this was on the same day that Christian radio broadcaster Harold Camping predicted that the world would come to an end.
December 2014: McClathy DC reported on "Intelligence, defense whistleblowers remain mired in broken system" that CIA contractor John A. Reidy had started raising concerns about the security of a communication systems used by the CIA and other sources mention that he started this in 2008[ref] The focus of the article is how he was then ignored and silenced for raising these concerns, which later turned out to be correct and leading to an intelligence catastrophe that started in 2010.[ref][ref] This appears to have come out after a heavily redacted appeal by Reidy against the CIA from October 2014 came into McClathy's possession.[ref] While Reidy's disclosures were responsible and don't give much away, given the little that they disclose it feels extremely likely that they were related to the same system we are interested in. Even heavily redacted, the few unredacted snippets of the appeal are pure gold and give a little bit of insight into the internal workings of the CIA. Some selections:
From January 2005 until January 2009, I worked as a government contractor at the CIA. I was assigned to [Directorate](ledger item 1) in the [Division] (ledger item 2). I served as a Uob) (ledger item 3) whose responsibility was to facilitate the dissemination of intelligence reporting to the Intelligence Community. I also served as a Oob 2) (ledger item 4) whose responsibility was to identify Human Intelligence (humint) targets of Interest for exploitation. I was assigned the telecommunications and information operations account.
As our efforts increased, we started to notice anomalies in our operations and conflicting intelligence reporting that indicated that several of our operations had been compromised. The indications ranged from [ redacted ] to sources abruptly and without reason ceasing all communications with us.
These warning signs were alarming due to the fact that our officers were approaching sources using [operational technique] (ledger item 16)
When our efforts began, ultimate operational authority rested with us. The other component provided the finances for the operation while we gave the operational guidance and the country specific knowledge.
knew we had a massive intelligence failure on our hands. All of our assets [ redacted ] were in jeopardy.
To give our compromise context, the U.S. communications infrastructure was under siege
All of this information was collected under the project cryptonym [cryptonym] (ledger item 52)
Meanwhile throughout 2010, I started to hear about catastrophic intelligence failures in the government office I formally worked for. More than one government employee reached out to me and notified me that the "nightmare scenario" I had described and tried to prevent had transpired. I was told that in upwards of 70% of our operations had been compromised.
it is not just a potential compromise in one country, It effects every country
May 2017: Mazzetti et al. reported for the New York Times at "Killing C.I.A. Informants, China Crippled U.S. Spying Operations" that:and that:
The Chinese government systematically dismantled C.I.A. spying operations in the country starting in 2010, killing or imprisoning more than a dozen sources over two years and crippling intelligence gathering there for years afterward.
January 2018: Pete Williams reported for NCB News at Alleged CIA China turncoat Lee may have compromised U.S. spies in Russia too that it was China that told Russia about the communications system:and that some theorize that former CIA agent Jerry Chun Shing Lee had betrayed Chinese spies, which some theorize may have been how China became aware of the communication network:According to Ex-C.I.A. Officer Sentenced to 19 Years in Chinese Espionage Conspiracy from November 2019 Lee was sentenced to 19 years in prison:
It was a shocking blow to an American spy agency that prides itself on its field operations. There was also a devastating human cost: Some 20 CIA sources were executed by the Chinese government, two former officials said — a higher number of dead than initially reported by NBC News and the New York Times. Then an unknown number of Russian assets also disappeared, sources say.
Soon after the task force concluded the Chinese had penetrated covcom, it got an even more troubling report: That after a joint training session between Chinese and Russian intelligence officers, the Russians "came back saying we got good info on covcom," as the former official put it
FBI agents began to suspect Lee after they received a tip that he had passed information to Chinese intelligence officers while working for a Japanese tobacco company in Hong Kong, sources said, a detail first reported Thursday by the New York Times. They also found it suspicious when Lee took a job at an auction house in Hong Kong that was co-owned by a senior Communist Party official, sources said. He eventually ended up working for Christie's, the international auction house.When agents searched Lee's hotel rooms in 2012, they found notebooks with the names of covert CIA sources, according to court documents.But not all of the agent arrests and deaths could be linked to information possessed by Lee, who left the CIA in 2007, the former officials said.
The former officer, Jerry Chun Shing Lee, 55, pleaded guilty in May to conspiring with Chinese intelligence agents starting in 2010, after he left the agency. Prosecutors detailed a long financial paper trail that they said showed that Mr. Lee received more than $840,000 for his work.
But F.B.I. agents who investigated whether he was the culprit passed on an opportunity to arrest him in the United States in 2013, allowing him to travel back to Hong Kong even after finding classified information in his luggage. F.B.I. agents had also covertly entered a hotel room Mr. Lee occupied in 2012, finding handwritten notes detailing the names and numbers of at least eight C.I.A. sources that he had handled in his capacity as a case officer.
Jerry Chun Shing Lee in blue tie at the unveiling of Leonardo da Vinci's 'Salvator Mundi' painting at the Christie's showroom in Hong Kong on Oct. 13, 2017
. Source. August 2018: Zach Dorfman reported for Foreign Policy at "Botched CIA Communications System Helped Blow Cover of Chinese Agents" that:and:Although no clear mention of websites is made in that article, the fact that there were "links" back to the CIA website strongly suggests that the communication was done through websites.
It was considered one of the CIA’s worst failures in decades: Over a two-year period starting in late 2010, Chinese authorities systematically dismantled the agency’s network of agents across the country, executing dozens of suspected U.S. spies. But since then, a question has loomed over the entire debacle. How were the Chinese able to roll up the network?
U.S. intelligence officers were also able to identify digital links between the covert communications system and the U.S. government itself, according to one former official—links the Chinese agencies almost certainly found as well. These digital links would have made it relatively easy for China to deduce that the covert communications system was being used by the CIA. In fact, some of these links pointed back to parts of the CIA’s own website, according to the former official.
The report also reveals that there was a temporary "interim system" that new sources would use while they were being vetted, but that it used the same style of system as the main system. It would be cool if we managed to identify which sites are interim or not somehow:
When CIA officers begin working with a new source, they often use an interim covert communications system—in case the person turns out to be a double agent.The communications system used in China during this period was internet-based and accessible from laptop or desktop computers, two of the former officials said.This interim, or “throwaway,” system, an encrypted digital program, allows for remote communication between an intelligence officer and a source, but it is also separated from the main communications system used with vetted sources, reducing the risk if an asset goes bad.
November 2018: Zach Dorfman and Jenna McLaughlin reported for Yahoo News the first clear report that the communication system was made up of websites at: "The CIA's communications suffered a catastrophic compromise. It started in Iran.":
In 2013, hundreds of CIA officers — many working nonstop for weeks — scrambled to contain a disaster of global proportions: a compromise of the agency’s internet-based covert communications system used to interact with its informants in dark corners around the world. Teams of CIA experts worked feverishly to take down and reconfigure the websites secretly used for these communications
The usage of of Google dorking is then mentioned:It seems to us that this would have been very difficult on the generically themed websites that we have found so far. This suggests the existence of a separate recruitment website network, perhaps the one reported in 2011 by Iran offering VISAs. It would be plausible that such network could link back to the CIA and other government websites. Recruited agents would only then later use the comms network to send information back. The target countries may have first found the recruitment network, and then injected double agents into it, who later came to know about the comms network. TODO: it would be awesome to find some of those recruitment websites!
In fact, the Iranians used Google to identify the website the CIA was using to communicate with agents.
Another very interesting mention is the platform had been over extended beyond its original domain application, which is in part why things went so catastrophically bad:
Former U.S. officials said the internet-based platform, which was first used in war zones in the Middle East, was not built to withstand the sophisticated counterintelligence efforts of a state actor like China or Iran. “It was never meant to be used long term for people to talk to sources,” said one former official. “The issue was that it was working well for too long, with too many people. But it was an elementary system.”
December 2018: a followup Yahoo News article "At the CIA, a fix to communications system that left trail of dead agents remains elusive" gives an interesting internal organizational overview of the failed operation:Much as in the case of Reidy, it is partly because of such internal dissatisfaction that so much has come out to the press, as agents feel that they have nowhere else to turn to.
Ciro Santilli conjectures that this fiasco was the motivation behind the creation of the Directorate of Digital Innovation.
As a result, many who are directly responsible for working with sources on the ground within the CIA’s Directorate of Operations are furious
The fiascos in Iran and China continue to be sticking points between the Directorate of Operations and the CIA’s Directorate of Science and Technology (DS&T) — the technical scientists. “There is a disconnect between the two directorates,” said one former CIA official. “I’m not sure that will be fixed anytime soon.”
Entire careers in the CIA’s Office of Technical Service — the part of DS&T directly responsible for developing covert communications systems — were built on these internet-based systems, said a former senior official. Raising concerns about them was “like calling someone’s baby ugly,” said this person.
Ciro Santilli conjectures that this fiasco was the motivation behind the creation of the Directorate of Digital Innovation.
That article also gives a cute insight into the OPSEC guidelines for the assets that used the websites:
CIA agents using the system were supposed to conduct “electronic surveillance detection routes” — that is, to bounce around on various sites on the internet before accessing the system, in order to cover their tracks — but often failed to do so, creating potentially suspicious patterns of internet usage, said this person.
29 September 2022: Reuters reported nine specific websites of the network at "America's Throwaway Spies", henceforth known only as "the Reuters article" in this article.
The most important thing that this article gave were screenshots of nine websites, including the domain names of two of them: iraniangoals.com and iraniangoalkicks.com:The "350-plus" number is a bit random, given that their own analysts stated a much higher 885 in their report.
In addition, some sites bore strikingly similar names. For example, while Hosseini was communicating with the CIA through Iraniangoals.com, a site named Iraniangoalkicks.com was built for another informant. At least two dozen of the 350-plus sites produced by the CIA appeared to be messaging platforms for Iranian operatives, the analysts found.
The article also reveals the critical flaw of the system; the usage of sequential IPs:
Online records they analyzed reveal the hosting space for these front websites was often purchased in bulk by the dozen, often from the same internet providers, on the same server space. The result was that numerical identifiers, or IP addresses, for many of these websites were sequential, much like houses on the same street.
It also mentions that other countries besides Iran and Chine were also likely targeted:
This vulnerability went far beyond Iran. Written in various languages, the websites appeared to be a conduit for CIA communications with operatives in at least 20 countries, among them China, Brazil, Russia, Thailand and Ghana, the analysts found.
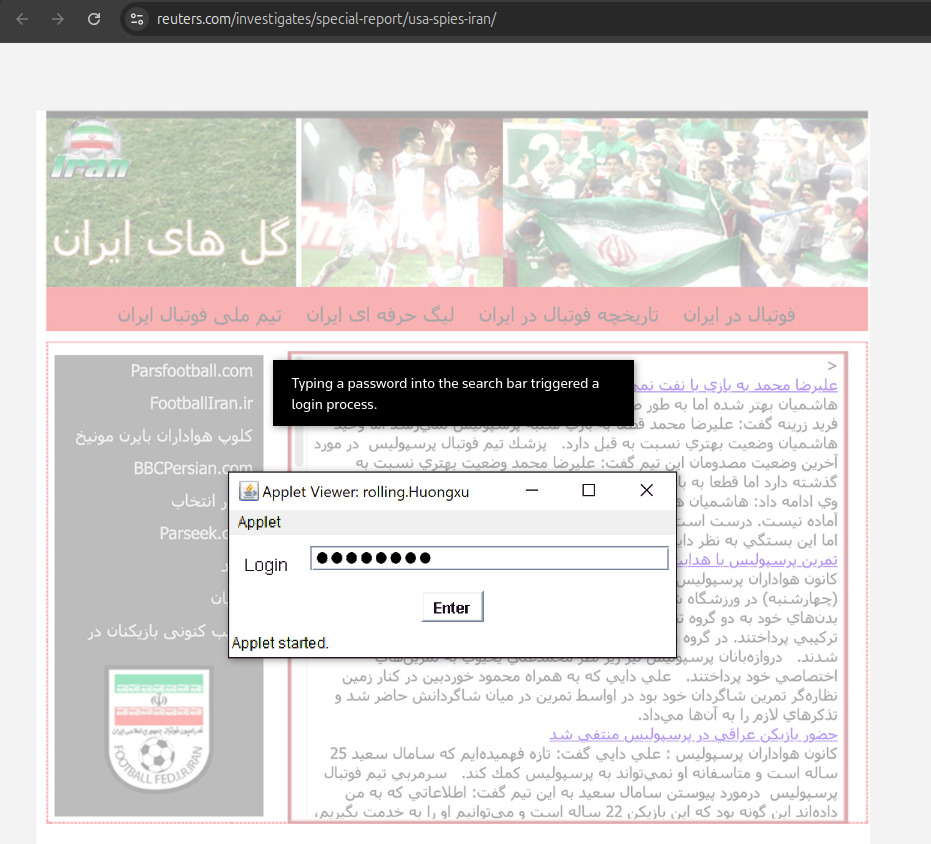
Reuters reconstruction of what the iraniangoals.com applet would have looked like
. Source. 29 September 2022: on the same day that Reuters published their report, Citizenlab, which Reuters used as analysts for the article, also simultaneously published their more technical account of things at "Statement on the fatal flaws found in a defunct CIA covert communications system".
One of the most important information given in that report is the large number of sites found, 885, and the fact that they are available on Wayback Machine:The million dollar question is "which website did they use" and "how much does it cost if anything" since our investigation has so far had to piece together a few different hacky sources but didn't spend any money. And a lot of money could be poured into this, e.g. DomainTools which might contain one of the largest historical databases, , seems to start at 15k USD / 1000 queries. One way to try and deduce which website they used is to look through their other research, e.g.:
Using only a single website, as well as publicly available material such as historical internet scanning results and the Internet Archive's Wayback Machine, we identified a network of 885 websites and have high confidence that the United States (US) Central Intelligence Agency (CIA) used these sites for covert communication.
- citizenlab.ca/2021/07/hooking-candiru-another-mercenary-spyware-vendor-comes-into-focus/ uses Censys, and it notably has historical data:Censys employee Silas Cutler AKA p1nk believes that Censys data does not reach that far back, since the company was only founded in 2017[ref].
- citizenlab.ca/2016/08/million-dollar-dissident-iphone-zero-day-nso-group-uae/ mentions scans.io/
- citizenlab.ca/2020/12/running-in-circles-uncovering-the-clients-of-cyberespionage-firm-circles/ mentions: www.shodan.io/
The article mentioned the different types of communication mechanisms found:
The websites included similar Java, JavaScript, Adobe Flash, and CGI artifacts that implemented or apparently loaded covert communications apps. In addition, blocks of sequential IP addresses registered to apparently fictitious US companies were used to host some of the websites. All of these flaws would have facilitated discovery by hostile parties.
They also give the dates range in which the system was active, which is very helpful for better targeting our searches:
And then a bomb, they claim to have found information regarding specific officers:This basically implies that they must have eitherWe have so for not yet found any such clear references to real individuals.
Nevertheless, a subset of the websites are linked to individuals who may be former and possibly still active intelligence community employees or assets:Given that we cannot rule out ongoing risks to CIA employees or assets, we are not publishing full technical details regarding our process of mapping out the network at this time. As a first step, we intend to conduct a limited disclosure to US Government oversight bodies.
- Several are currently abroad
- Another left mainland China in the time frame of the Chinese crackdown
- Another was subsequently employed by the US State Department
- Another now works at a foreign intelligence contractor
- found some communication layer level identifier, e.g. domain name registration HTTPS certificate certificate because it is impossible to believe that real agent names would have been present on the website content itself!
- or they may be instead talking about a separate recruitment network which offered the VISAs which we conjecture might have existed but currently have no examples of, and which might conceivably contain real embassy contacts
October 2022 Zach Dorfman, author of the 2018 Yahoo News and Foreign Policy articles gave some good anecdotes he had heard from his sources after the Reuters expose in his personal blog post On Agent Compromise in the Field, giving a more personal account of some of the events that took place:
Now, an important caveat: I have known dedicated former CIA officials who have spoken of the care, respect, and obligation they felt toward their sources, and the lengths they would go to assist them. For many case officers — that is, the CIA's primary corps of spy handlers — this is a core part of their professional identity.During the roll-up in China, for instance, a former U.S. official told me about a CIA officer who, aware that something was going terribly wrong there, organized final, assuredly dangerous, in-person meetings with agency sources. This distraught CIA officer essentially shoved wads of cash into sources' hands. This CIA officer warned them of the unfolding disaster and begged them to leave the country as fast as they could. Another source told me a story about a CIA official who, while being debriefed in Langley about the asset roll-up — and the slapdash COVCOM system — broke down in tears upon hearing that sources’ lives had been destroyed because of such obvious dereliction, of which they were previously unaware.
But I don’t want to oversell this point, either. By its nature, the world of espionage is steeped in the sordid aspects of human experience, exploiting people’s vulnerabilities for narrow informational gain. [...]Indeed, many former CIA officials have a decidedly pragmatic and amoral conception of their profession. Bad things happen when you spy, or recruit others to do so. [...] I had a conversation once with a former senior CIA official with experience in Iran issues who had an almost naturalistic view of recurring asset losses there over the years: for him, it was a built-in, cyclical feature of the work and environment, like the denuding of deciduous forests every fall.
CIA 2010 covert communication websites USA spying on its own allies Updated 2025-08-08
Being Brazilian, Ciro Santilli was particularly curious about the existence of a Brazil-focused mentioned in the Reuters article, as well as in other democracies.
WTF the CIA was doing in Brazil in the early 2010s! Wasn't helping to install the Military dictatorship in Brazil enough!
Here are the websites likely targeting democracies based on their language and content found so far, defining a democracy as a country with score 7.0 or more in the Democracy index 2010:In English, so more deniable:"Almost democracies":Ciro couldn't help but feel as if looking through the Eyes of Sauron himself!
- France (6: affairesdumonde.com, guide-daventure.com, lesummumdelafinance.com, football-de-luxe.com, romulusactualites.com, suparakuvi.com)
- Germany(2: dedrickonline.com, neighbour-news.com)
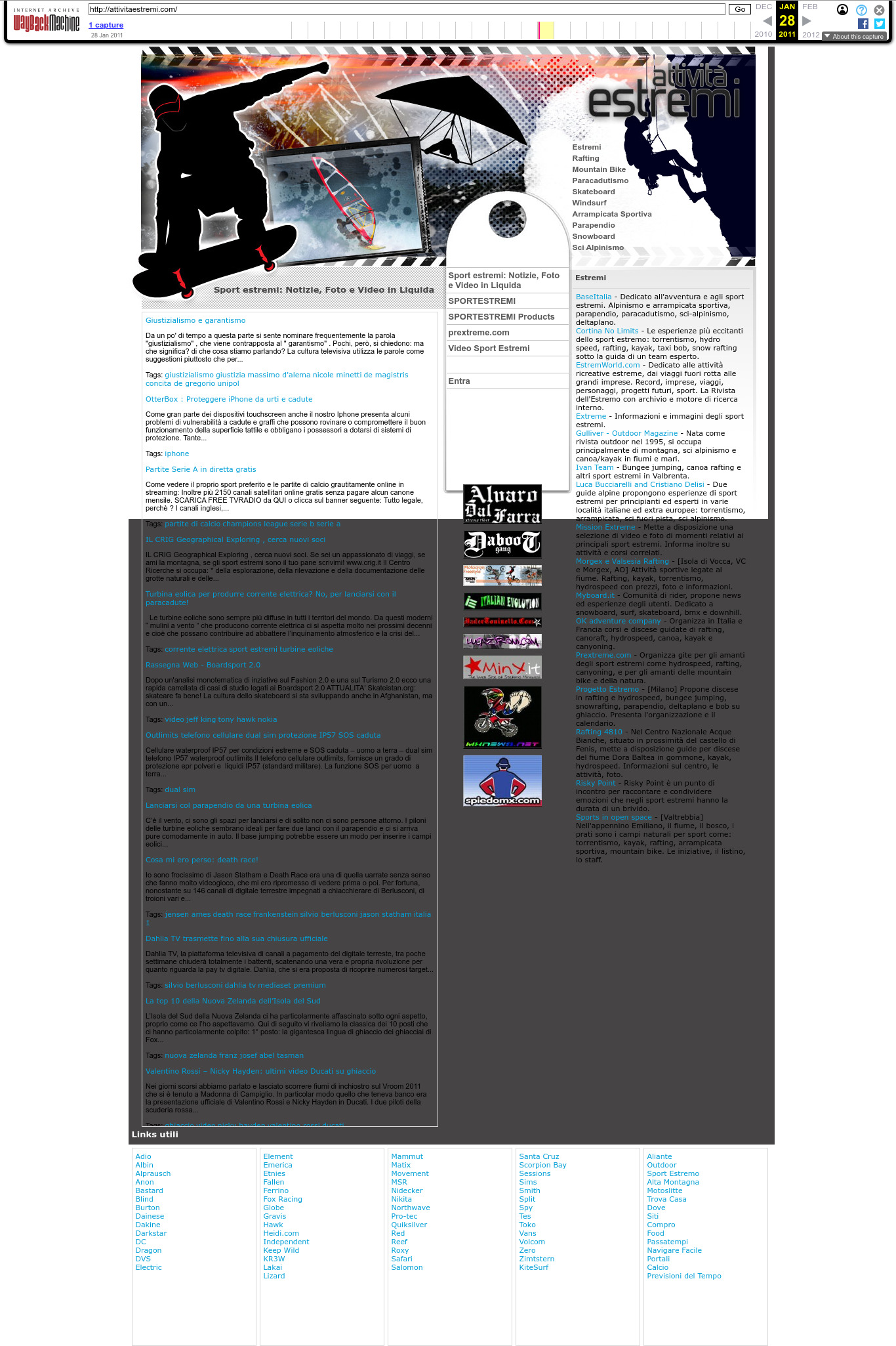
- Italy (2: attivitaestremi.com, garanziadellasicurezza.com, podisticamondiale.com)
- Spain (3: armashoy.com, montanismoaventura.com, ordenpolicial.com)
- Brazil (2: noticiasmusica.net, vejaaeuropa.com)
- South Korea (1: economicnewsbuzz.com)
- Poland (1: boxingstop.net)
- Japan (1: snapnewsfront.net)
- Canada (2: kanata-news.com, mynewscheck.com)
- Philippines (1: half-court.net)
- India (1: amishkanews.com)
- Croatia (2: european-footballer.com, stara-turistick.com)
- Thailand (1: thefairwaysaregreen.com)
- Peru (1: todosperuahora.com)
It is worth noting that democracies represent just a small minority of the websites found. The Middle East, and Spanish language sites (presumably for Venezuela + war on drugs countries?) were the huge majority. But Americans have to understand that democracies have to work together and build mutual trust, and not spy on one another. Even some of the enlightened people from Hacker News seem to not grasp this point. The USA cannot single handedly maintain world order as it once could. Collaboration based on trust is the only way.
Snowden's 2013 revelations particularly shocked USA "allies" with the fact that they were being spied upon, and as of the 2020's, everybody knows this and has "stopped caring", and or moved to end-to-end encryption by default. This is beautifully illustrated in the 2016 film "Snowden" when Snowden talks about his time in Japan working for Dell as an undercover NSA operative:
NSA wanted to impress the Japanese. Show them our reach. They loved the live video from drones. This is Pakistan right now [video shows American agents demonstrating drone footage to Japanese officials]. They were not as excited about that we wanted their help to spy on the Japanese population. They said it was against their laws.And we did not stop there. Once we owned their communications systems, we started going after the physical infrastructure.We'd slip these little sleeper programs into power grids, dams, hospitals. The idea was that if the day came when Japan was no longer an ally, it would be "lights out".But Austria?!
Another noteworthy scene from that movie is Video 2. "Aptitude test on communication networks scene from the 2016 Snowden film", where a bunch of new CIA recruits are told that:thus somewhat mirroring what actually happened with these real world websites.
Each of you is going to build a covert communications network in your home city [i.e. their fictitious foreign target location written on each person's desk such as Berlin, Istanbul and Bangkok, not necessarily where they were actually born], you're going to deploy it, backup your site, destroy it, and restore it again.
Cirism Updated 2025-07-16
Cirism is totally not a cult, has been officially verified to be compatible with all major world religions.
Enlightened Cirists donate money to the cause at: Section "Sponsor Ciro Santilli's work on OurBigBook.com". It is totally optional of course, your soul will just be eternally damned if you don't.
Ciro Santilli once proclaimed:
Thou shalt eat thy watermelon in the morning, and thy melon in the evening. Thou shalt not eat thy watermelon in the evening, nor shalt thou eat thy melon in the morning.
Cirocoin Updated 2025-07-16
Cirocoins can only be issued by Ciro Santilli.
Cirocoins are strictly nominal, and cannot be traded by recipients with anyone but Ciro, i.e. they are extremely illiquid.
Cirocoins can be removed from recipients at any point if they commit non-Cirist acts.
It is not possible to give a precise number to how many Cirocoins anyone owns. This is decided on a transaction by transaction basis. Ciro can therefore only inform you if your Cirocoin balance increased or decreased, but any attached number has no value, and thus are equivalent to expressions of type "you gained/lost a Cirocoin".
Ciro Duran Santilli Updated 2025-07-16
Ciro Santilli's full birth name is "Ciro Duran Santilli", with mother's last name "Duran" in the middle as per Brazilian tradition.
But Ciro's usage of "Duran" got gradually dropped to "Ciro Santilli", Ciro's official Italian name, as Ciro moved more and more definitively to Europe.
It can still however be seen in certain online places where Ciro didn't have the patience or power to change it e.g. some old École Polytechnique stuff: gitlab.binets.fr/ciro.duran-santilli/china-dictatorship
Ciro's 2D reinforcement learning games Updated 2025-07-16
Prototype: github.com/cirosantilli/Urho3D-cheat
Top Down 2D Continuous Game with Urho3D C++ SDL and Box2D for Reinforcement learning by Ciro Santilli (2018)
Source. Source code at: github.com/cirosantilli/Urho3D-cheat.Screenshot of the basketball stage of Ciro's 2D continuous game
. Source code at: github.com/cirosantilli/rl-game-2d-grid. Big kudos to game-icons.net for the sprites.Less good discrete prototype: github.com/cirosantilli/rl-game-2d-grid YouTube demo: Video 1. "Top Down 2D Continuous Game with Urho3D C++ SDL and Box2D for Reinforcement learning by Ciro Santilli (2018)".
Top Down 2D Discrete Tile Based Game with C++ SDL and Boost R-Tree for Reinforcement Learning by Ciro Santilli (2017)
Source. The goal of this project is to reach artificial general intelligence.
A few initiatives have created reasonable sets of robotics-like games for the purposes of AI development, most notably: OpenAI and DeepMind.
However, all projects so far have only created sets of unrelated games, or worse: focused on closed games designed for humans!
What is really needed is to create a single cohesive game world, designed specifically for this purpose, and with a very large number of game mechanics.
Notably, by "game mechanic" is meant "a magic aspect of the game world, which cannot be explained by object's location and inertia alone" in order to test the the missing link between continuous and discrete AI.
The question then becomes: do we have enough computational power to simulation a game worlds that is analogous enough to the real world, so that our AI algorithms will also apply to the real world?
To reduce computation requirements, it is better to focus on a 2D world at first. Such world with the right mechanics can break any AI, while still being faster to simulate than a 3D world.
The initial prototype uses the Urho3D open source game engine, and that is a reasonable project, but a raw Simple DirectMedia Layer + Box2D + OpenGL solution from scratch would be faster to develop for this use case, since Urho3D has a lot of human-gaming features that are not needed, and because 2019 Urho3D lead developers disagree with the China censored keyword attack.
Simulations such as these can be viewed as a form of synthetic data generation procedure, where the goal is to use computer worlds to reduce the costs of experiments and to improve reproducibility.
Ciro has always had a feeling that AI research in the 2020's is too unambitious. How many teams are actually aiming for AGI? When he then read Superintelligence by Nick Bostrom (2014) it said the same. AGI research has become a taboo in the early 21st century.
Related projects:
- github.com/deepmind/lab2d: 2D gridworld games, C++ with Lua bindings
Related ideas:
- www.youtube.com/watch?v=MHFrhIAj0ME?t=4183 Can't get you out of my head by Adam Curtis (2021) Part 1: Bloodshed on Wolf Mountain :)
- www.youtube.com/watch?v=EUjc1WuyPT8 AI alignment: Why It's Hard, and Where to Start by Eliezer Yudkowsky (2016)
Bibliograpy:
- agents.inf.ed.ac.uk/blog/multiagent-learning-environments/ Multi-Agent Learning Environments (2021) by Lukas Schäfer from the Autonomous agents research group of the University of Edinburgh. One of their games actually uses apples as visual represntation of rewards, exactly like Ciro's game. So funny. They also have a 2d continuous game: agents.inf.ed.ac.uk/blog/multiagent-learning-environments/#mpe
- humanoid robot simulation
- Section "AI training game"
- Section "Software-based artificial life"
OpenAI Plays Hide and Seek... and Breaks The Game! by Two Minute Papers (2019)
Source. Commentary of OpenAi's 2019 hide and seek paper. OpenAI does some similar simulations to what Ciro wants, but TODO do they publish source code for all of them? If not Ciro calls bullshit on non-reproducible research, and even worse due to the fake "Open" in the name. Does this repo contain everything?Much bigger simulation, AIs learn Phalanx by Pezzza's Work (2022)
Source. 2d agents with vision. Simple prey/predator scenario. Ciro Santilli Updated 2025-07-16
Quick facts:
- Nationalities: Italian and Brazilian
- Grew up in: Brazil
- Relationship status 2017-: married
- Given name pronunciation: take your pick from Ciro Santilli's given name
- Chinese name: 三西猴, means "three western monkeys". Phonetic approximation to SANtilli CIRO. More info at: Ciro Santilli's Chinese name. Semi-unintentionally reminds Chinese people of Sun Wukong (孙悟空). This association is further slightly strengthened by the phonetic choice of 三 San, which Ciro later noticed matches the middle character of Tang Sanzang (唐三藏), the monk in Journey to the West. The given name 西猴 was given by Ciro Santilli's wife, then recent girlfriend, as a semi-joke, and he took it up because the best way to take a joke is to play along with the joker. 三 was chosen by Ciro himself.
- laptop: high end Lenovo ThinkPad
- distro: latest Ubuntu release
- Vim or Emacs: vi/vim. But for The Love, will someone please make an open source C++ integrated development environment that actually just works?
- tabs or spaces: spaces
- Mailing list or Git(Hub|Lab): Git(Hub|Lab), with passion, see Section "Mailing list"
- system or unit tests: system
- programming languages: Python and C++. He'll learn Rust and Haskell once he's rich. As of the 2020s, Rust was picking up some serious steam, so Ciro might end up eating his own words there.
- musical instruments to listen: Chinese Guqin and electric Jazz-fusion guitar
- metric or imperial: metric, for The Love. Science? Standardization? 21st century anyone?
- QWERTY or Dvorak: QWERTY, alas
- birth name: Ciro Duran Santilli
Other people with the same name are listed at Section "Ciro Santilli's homonyms".
19th century illustration of the Journey to the West protagonist Sun Wukong
. Source. Sun Wukong (孙悟空) is a playful and obscenely powerful monkey Journey to the West. He protects Buddhist monk Tang Sanzang, and likes eating fruit, just like Ciro. Oh, and Goku from Dragon Ball is based on him. His japanese name is "Sun Wukong" (same Chinese characters with different Japanese pronunciation) for the love. His given name "Wukong" means literally "the one who mastered the void", which is clearly a Dharma name and fucking awesome in multiple ways. This is another sad instance of a Chinese thing better known in the West as Japanese.
It is worth noting however that although Wukong is extremely charming, Ciro's favorite novel of the Four Great Classic Novels is Water Margin. Journey to the West is just a monster of the week for kids, but Water Margin is a fight for justice saga. Sorry Wukong!
Ciro Santilli playing with a pipette at the University of Cambridge circa 2017
. The photo was taken in an open event organized by the awesome Cambridge Synthetic Biology outreach group, more or less the same people who organize: www.meetup.com/Cambridge-Synthetic-Biology-Meetup/ and who helped organize Section "How to use an Oxford Nanopore MinION to extract DNA from river water and determine which bacteria live in it".
Taking part in such activities is what Ciro tries to do to overcome his lifelong regret of not having done more experimental stuff at university. Would he have had the patience to handle all the bullshit of the physical word without going back to the informational sciences? Maybe, maybe not. But now he will probably never know?!
Notice the orange high visibility cycling jersey under the lab coat, from someone who had just ridden in from work as fast as possible as part of his "lunch break". It is more fun when it is hard.
Scribe Jean Miélot, 15th century
. Ciro Santilli fantasizes that he would have make a good scribe in the middle ages, partly due to his self diagnosed graphomania, but also appreciation for foreign languages, and his mild obsession with the natural sciences.
OurBigBook.com is Ciro's view of a modern day scriptorium, except that now the illuminations are YouTube videos.
Chill and eat your bread in peace comes to mind. A scribe, in a library, reading and writing the entire day in peace and quiet. The life!
The job of a Internet-age scribe is basically that of making knowledge more open, legally extracting it from closed copyrighted sources, and explaining your understanding of it to the wider world under Creative Commons licenses on the web. And in the process of greater openness, given a well organized system, we are able combine the knowledge of many different people, and thus make things more understandable than any single/few creator closed source source could ever achieve.
Ciro Santilli waving hello in infrared.
More info at: Figure "Ciro Santilli waving hello in infrared". Ciro Santilli Big Five Personality traits Updated 2025-07-16
This is how Ciro Santilli evaluates himself on the Big Five personality traits:
- Openness to experience; very high, see: Ciro Santilli's self perceived creative personality
- Conscientiousness: low, Ciro is driven very strongly by internal passion rather than external expectations
- Extraversion: high online, e.g. Ciro Santilli's campaign for freedom of speech in China, but much lower in the real world, no patience for something he's not Googled for in the last 5 seconds
- Agreeableness: high, see e.g. Ciro Santilli's self perceived compassionate personality. But Ciro has built some tolerance disagreement online for it online during Ciro Santilli's campaign for freedom of speech in China, you've got to fight for what is right.
- Neuroticism: medium high, Ciro does have some anxiety. It does help get things done sometimes, but it also sometimes gets in the way.
cirosantilli.com Updated 2025-07-16
However it won't remain like that for long, because it will be migrated to OurBigBook.com, and therefore become a brain dump of society itself.
Ciro Santilli Myers-Briggs Type Indicator Updated 2025-07-16
Ciro Santilli feels that Ciro Santilli Myers-Briggs Type Indicator is much more random/hard to determine than the Big Five personality traits